- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud Cloud Network Security CloudMates General CNAPP CloudGuard - WAF Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Open Garden In Action:
Find and Remediate Threats Everywhere!
New Appliance Announcements
and Faster Threat Prevention
Remote Access VPN – User Experience
Help us with the Short-Term Roadmap
It's Here!
CPX 2025 Content
CheckMates Go:
AI Agents
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Cannot disable IPSec blade on the gatewa
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Cannot disable IPSec blade on the gatewa
Dear Mates
I need your urgent help.
I have enabled IPSec blade on one of our clusters, and I now need to disable it because it mays be causing some issues with another IPSec that we use from a vendor within our network.
When I try to disbale IPSec, itshows the message on the image bellow:
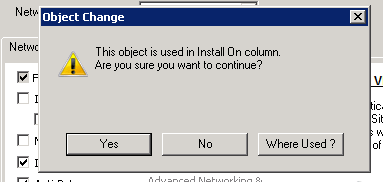
When I check where used, it shows all the entries in the image bellow, but I dont how. Could you kindly help me on how I can proceed with the disabling of IPSec on this cluster object? Why fear is if I disbale IPSec may cause some problem.
Please help out.
Thanks in advance
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I forgot to add this piicture.
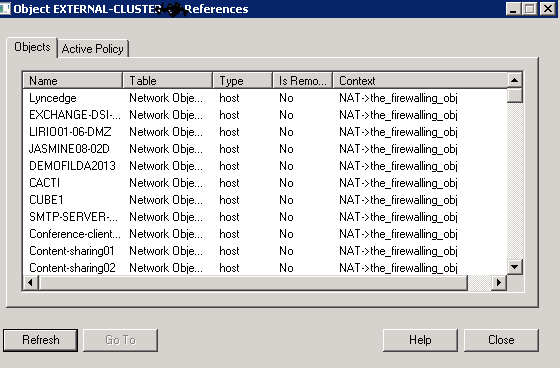
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The use of the firewall object in an automatic NAT setup (which is what is shown in your screenshot) shouldn't matter in regards to unchecking the IPSec VPN blade. However if you scroll down in that References list I imagine you will see the firewall explicitly specified in a Firewall policy rule as the Install On gateway, and that same rule also specifies a VPN Community object in the VPN column. Or the firewall object is defined as a participating gateway in a VPN Community object. If you were to uncheck the IPSec VPN blade in this case and attempt to install policy this will almost certainly cause a policy verification failure.
Please post a screenshot of where else the firewall object is used other than "NAT->the_firewalling_obj" for further analysis. And be sure to take a Database Revision before trying to make this change if you are using R77.30 management just in case.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices
Self-Guided Video Series Coming Soon
Self-Guided Video Series Coming Soon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have done it, and I had no further impact. Thanks for your feddback.
I would like to take this opportunity to ask an additional question: if you have on external cluster that leads to the Public Internet, and an internal cluster to control your internal resources. Is it possible to allow the Remote Access to be on the internal cluster instead of the External Cluster? if yes, how?
Thank you once again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm assuming that your ISP-routable space ends at the external cluster and you are using some kind of RFC1918 space on the screened subnet (or whatever the network is) between the external cluster and the internal cluster. Terminating remote access VPNs on the internal cluster is definitely possible assuming you set "Statically NATted IP" on the Link Selection screen under IPSec VPN on the internal cluster object. The address you put here is whatever Internet-routable Static NAT address has been allocated to the internal cluster by the external cluster.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices
Self-Guided Video Series Coming Soon
Self-Guided Video Series Coming Soon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tim,
I got one final question to you with regards to this cenario.
I have replicated the lab into the production and it is working perfectly. when a client on the Remote site access a VPN, it get the office mode IP address, but when it access an internal server, when I run the wireshark, the IP that appears there is an IP that belongs to Network N which means the office mode address is being NATed.
I would like to know if in my implementation cenario is possible to stop NATing so that office mode IP gets to the Network N without being NATed? if yes, can you give an ideia about the NAT rule?
By the way, your book is on its way to me, and I am sure it will be very handy.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are using the default CP_default_Office_Mode_addresses_pool object for the Office Mode address, it has NAT enabled on it by default. Just go to the NAT tab on that object and uncheck it. If you are using some other object, you may need to add a manual anti-NAT rule for the Office Mode range at the top of your NAT policy.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices
Self-Guided Video Series Coming Soon
Self-Guided Video Series Coming Soon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tim,
I am using some other object and created a Manual NAT, and It worked just fine.
In your personal opinion, in terms of security, which way is the best:
1. Office Pool being NATed
2. Office Pool not being NATed
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
NATing the Office Mode address isn't really a matter of increasing security, but ensuring proper routing behavior for traffic returning to the firewall for encryption back into the Remote Access VPN tunnel. Normally you don't need to NAT Office Mode addresses, and you just specify an IP subnet for the Office Mode assignments that your internal network is guaranteed to return to that same firewall in a symmetric fashion.
One situation where you might NAT Office Mode addresses is in a Multiple Entry Point (MEP) VPN scenario which involves several firewalls at different locations with their own Internet connections, and a backend WAN connecting all the different sites as well. In some cases Remote Access VPN traffic might enter the inside network via Firewall A, but then try to asymmetrically return to the Internet through Firewall B located at another site which will not work. If you are not able to correct the routing inside your network due to technical or political reasons, performing NAT on the source IP of the Office Mode traffic at Firewall A and making it an address that is guaranteed to be returned to Firewall A symmetrically can help avoid this issue.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices
Self-Guided Video Series Coming Soon
Self-Guided Video Series Coming Soon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your valuable comment Mate... Much appreciated.
The figure bellow depicts our current setup, and we want to terminate the VNP connection on the internal gateway because that gateway can reach all the networks that we want. So based on the figure, which address in the simulated networks bellow should be statically NATed, and to which address.
Once again thank you for your time.
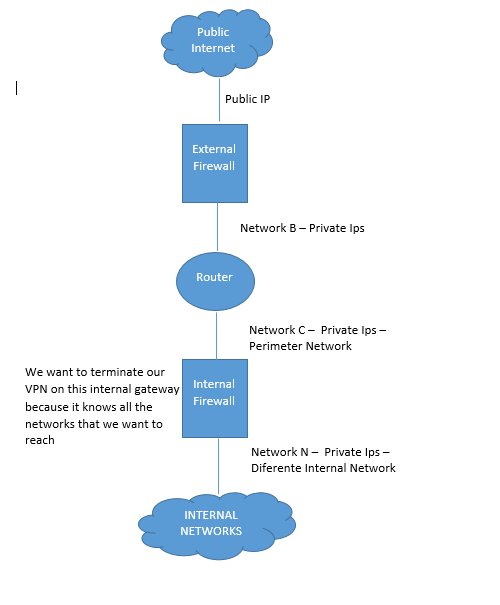
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Allocate an unused Public IP, and on the External Firewall statically NAT it to the Internal firewall's interface address on Network C. Then set the Internal Firewall's VPN Link Selection Static NAT to the value of the assigned Public IP. You will also need a rule in your Firewall/Network Policy Layer on the External Firewall permitting a service of Any, source Any to the Internal Firewall's public NAT address.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices
Self-Guided Video Series Coming Soon
Self-Guided Video Series Coming Soon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much Timothy Hall, I will try that first in my lab environment, and then give you the feedback of my experience.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tim,
I have followed your instructions and the Site is not responding.
I have created the same cenario in a lab first, and this is what I am doing.
Public IP: 192.168.1.3 NATed to 10.10.3.1 (the internal firewall address in network C)
Internal Firewall Link Selection to: 192.168.1.3
The last part about the Firewall/Network policy is what I dont understand very well. Could please elaborate more on that. Do I only need one policy on the external firewall? dont I need another policy in the internal cluster?
Thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tim,
I followed the instructions you have shared but I am getting the following problem:
1. The site is not responding when I try to connect
2. When I check the Log in smartview tracker, the traffic going to the public IP that was statically NATed to the internal firewall is getting there in http and https, not ike traffic.
Any thoughts as to what could be causing this.
Kind regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi again Tim,
I finally got it up and running.
Your contribution helped me alot. I had to enable Sticky Forwarding Function because our Cluster is in Load sharing mode. Then everything worked just fine.
Thank you
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Wed 16 Jul 2025 @ 10:00 AM (CEST)
Master GCP Security with the Cloud Architects Series (Multilingual Webinar)Wed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 22 Jul 2025 @ 10:00 AM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - EMEATue 22 Jul 2025 @ 05:00 PM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - AMERWed 16 Jul 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part II: Threat Hunting & Incident ResponseTue 22 Jul 2025 @ 10:00 AM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - EMEATue 22 Jul 2025 @ 05:00 PM (CEST)
Cyber Security Training in the Era of AI Threats: Managed SmartAwareness Explained - AMERWed 13 Aug 2025 @ 04:00 PM (CEST)
Operationalizing Threat Intelligence, Part III: Threat Modeling & Security PreparednessAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


