- CheckMates
- :
- Products
- :
- Harmony
- :
- Endpoint
- :
- Speed up Threat Emulation or ignore specific file
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Speed up Threat Emulation or ignore specific file
We are finding a significant delay in downloading a specific .exe application (Support-LogMeInRescue.exe). Threat emulation is set to Default (Emulate with Suspend) for .exe downloads which is ideal setting for these types of web downloads.
Is there any way to speed up Threat Emulation for Support-LogMeInRescue.exe or to add this file to an exclusion from Threat Emulation ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can add the MD5 sum of the file to the Whitelist and override the inspection settings for it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Many thanks Sigbjorn. What white list are you referring to, I can't see anywhere within Threat Extraction to add MD5 check sum?
I can only see two places where files can be excluded.
1. Inspect all domains and files except Trusted Sites
2. Prevent legitimate applications exploitation attempts
"1. Inspect all domains and files except Trusted Sites" I can see the domain could be added so that could be an option for trusted sites, there is also an option to add SHA1 HASH. Would adding a file here exclude Web Download Emulation ?
"2. Prevent legitimate applications exploitation attempts" I can see a process can be added but only as process path. Would adding file as *\Support-LogMeInRescue.exe exclude Web Download Emulation ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
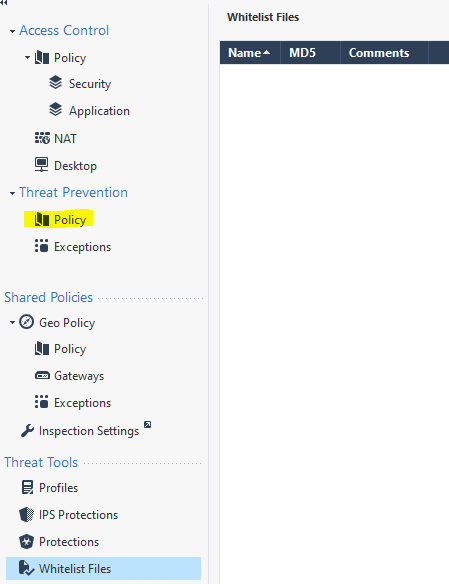
When you're in the Threat Policy view, there's view called "Whitelist Files" under the Threat Tools in the botton left corner. In that view you can add filenames with their md5sum, and then use that in the threat policy.
Once the file is added, go back to the Threat Policy and create a new exception, choose the file you created in the "Protection/Site/File/Blade" column.