- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Toolbox Contest 2024
Submit a Tool for a Chance to WIN a $300 or $50 Gift Card!
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
Harmony Endpoint:
Packing a Punch in 2024
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
The Difference Is In The Details
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- DevSecOps
- :
- Re: Verify Policy Ansible with Checkpoint
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Verify Policy Ansible with Checkpoint
Hi,
Goal: I am trying to Verify Access Control Policy using Ansible for a particular domain
I used the documentation https://docs.ansible.com/ansible/latest/collections/check_point/mgmt/cp_mgmt_verify_policy_module.ht...
- name: verify-policy cp_mgmt_verify_policy: policy_package: standard
I set
- name: verify-policy cp_mgmt_verify_policy: policy_package: #the UID or String of the device
I got an error message when I ran my playbook
Playbook.yml
---
- hosts: check_point
connection: httpapi
gather_facts: False
vars_files:
- 'my_var.yaml'
- 'login.yml' tasks:
- name: verify-policy
check_point.mgmt.cp_mgmt_verify_policy:
policy_package: #device name or UID added here
#cp_mgmt_verify_policy: #policy_package: standard
my_var.yaml
ansible_httpapi_validate_certs: False
ansible_httpapi_use_ssl: True
ansible_network_os: check_point.mgmt.checkpoint
ansible_python_interpreter: /usr/bin/python3
login.yml
ansible_user: #checkpoint username
ansible_password: #checkpoint password
host inventory
[check_point]
#ip address of my checkpoint device
Error Message
$ ansible-playbook Playbook.yml
PLAY [check_point] **************************************************************************************
TASK [verify-policy]
fatal: [checkpoint]: FAILED! => {"changed": false, "msg": "Checkpoint device returned error 404 with message {'code: 'generic_err_object_not_found'} Unpublished chnages were dicharged"}
PLAY RECAP **********************************************************************************************
checkpoint :ok=0 changed=0 unreachable=0 failed=1 skipped=0 rescued=0 ignored=0
I'm I doing anything wrong here, is there anything I should be aware of?
4 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
policy_package:
i guess that it refers to the policy/security package that you are running the verification for.
dunno if it's case sensitive.
L.E. just saw that you are doing it for a specific domain in an MDS env. try and add at end
---
- hosts: check_point
connection: httpapi
gather_facts: False
vars_files:
- 'my_var.yaml'
- 'login.yml' tasks:
- name: verify-policy
check_point.mgmt.cp_mgmt_verify_policy:
policy_package: policy-name
vars:
ansible_checkpoint_domain: "domain"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi,
the name of the policy package that you are setting rules in and installing on the gateways.
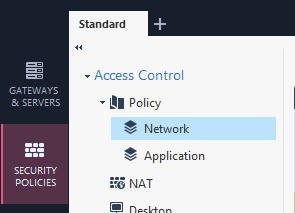
you can see it in Security Policies ( default name is Standard ) or from the firewall with fw stat.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You said you are executing against the domain, so you are in MDS environment. You have to provide the CMA/Domain/DMS name as in the MDS as well. See the README and search for ansible_checkpoint_domain: https://galaxy.ansible.com/check_point/mgmt
In short, you have to give the variable ansible_checkpoint_domain the CMA domain name as in the MDS at either the inventory level, the playbook, or the task level.
Inventory file for your host:
mds-cma-name ansible_host=192.168.1.111 ansible_checkpoint_domain=CMA1
That should be it.
Also, when you execute the playbook, add 1 verbosity level (-v) so that you can see more stdout than just "changed".
Furthermore, as this is just a verify and no changes are made, consider adding changed_when: false to the root level of the task.
---
- name: Verify Policy
hosts: mds-cma1
connection: httpapi
tasks:
- name: verify-policy
check_point.mgmt.cp_mgmt_verify_policy:
policy_package: "My_Policy"
changed_when: false- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
well, in the ini format you can list the hosts as if they are CMAs with the variable ansible_checkpoint_domain
[cmas]
cma1 ansible_host=192.168.1.11 ansible_checkpoint_domain=cma1
cma2 ansible_host=192.168.1.11 ansible_checkpoint_domain=cma2
cma3 ansible_host=192.168.1.11 ansible_checkpoint_domain=cma3I believe there is a bug in the login/discard/logout process of each httpapi plugin connection instantiation, because if in the playbook we call hosts: cmas or multi-host execution, we don't relogin but reuse the same session. That is a bug. So for now if you want to loop all hosts in the cmas hosts group, you will have to write a separate playbook and call it for each CMA, or can still have the same playbook with the same hosts-group cmas, and limit the execution to a host in the group like ansible-playbook ... --limit=cma2
Sorry, but this is the workaround for now.
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
policy_package:
i guess that it refers to the policy/security package that you are running the verification for.
dunno if it's case sensitive.
L.E. just saw that you are doing it for a specific domain in an MDS env. try and add at end
---
- hosts: check_point
connection: httpapi
gather_facts: False
vars_files:
- 'my_var.yaml'
- 'login.yml' tasks:
- name: verify-policy
check_point.mgmt.cp_mgmt_verify_policy:
policy_package: policy-name
vars:
ansible_checkpoint_domain: "domain"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I am very confused, it in terms of policy/security package, can you give me an example?
Would I say
policy_package: Access Control
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi,
the name of the policy package that you are setting rules in and installing on the gateways.
you can see it in Security Policies ( default name is Standard ) or from the firewall with fw stat.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Technically, access control is an ordered layer and policy package would be the name of the policy that you gave (I dont know, could be standard, or companyname_policy or whatever you named it)
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You said you are executing against the domain, so you are in MDS environment. You have to provide the CMA/Domain/DMS name as in the MDS as well. See the README and search for ansible_checkpoint_domain: https://galaxy.ansible.com/check_point/mgmt
In short, you have to give the variable ansible_checkpoint_domain the CMA domain name as in the MDS at either the inventory level, the playbook, or the task level.
Inventory file for your host:
mds-cma-name ansible_host=192.168.1.111 ansible_checkpoint_domain=CMA1
That should be it.
Also, when you execute the playbook, add 1 verbosity level (-v) so that you can see more stdout than just "changed".
Furthermore, as this is just a verify and no changes are made, consider adding changed_when: false to the root level of the task.
---
- name: Verify Policy
hosts: mds-cma1
connection: httpapi
tasks:
- name: verify-policy
check_point.mgmt.cp_mgmt_verify_policy:
policy_package: "My_Policy"
changed_when: false- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, everyone. Everyone's contribution on here was a solution. It works!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
what if I have multiple domains with many policies in them. How do I write my inventories to contain those domains and policies?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
well, in the ini format you can list the hosts as if they are CMAs with the variable ansible_checkpoint_domain
[cmas]
cma1 ansible_host=192.168.1.11 ansible_checkpoint_domain=cma1
cma2 ansible_host=192.168.1.11 ansible_checkpoint_domain=cma2
cma3 ansible_host=192.168.1.11 ansible_checkpoint_domain=cma3I believe there is a bug in the login/discard/logout process of each httpapi plugin connection instantiation, because if in the playbook we call hosts: cmas or multi-host execution, we don't relogin but reuse the same session. That is a bug. So for now if you want to loop all hosts in the cmas hosts group, you will have to write a separate playbook and call it for each CMA, or can still have the same playbook with the same hosts-group cmas, and limit the execution to a host in the group like ansible-playbook ... --limit=cma2
Sorry, but this is the workaround for now.
Upcoming Events
Thu 16 May 2024 @ 10:00 AM (CEST)
EMEA: Playblocks & MS Defender – Security Automation DeepDive into New Endpoint IntegrationThu 16 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - ACHTUNG, Sie werden gehackt! So schützen Sie sich!Thu 16 May 2024 @ 05:00 PM (CEST)
Americas: Playblocks & MS Defender – Security Automation DeepDive into New Endpoint IntegrationFri 17 May 2024 @ 10:00 AM (CEST)
CheckMates Live Netherlands - Sessie 26: ElasticXL & VSNext DescriptionTue 21 May 2024 @ 10:00 AM (CEST)
CheckMates Live DACH - Einführung in Check Points Hyperscalinglösung - Quantum MaestroThu 16 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - ACHTUNG, Sie werden gehackt! So schützen Sie sich!Fri 17 May 2024 @ 10:00 AM (CEST)
CheckMates Live Netherlands - Sessie 26: ElasticXL & VSNext DescriptionTue 21 May 2024 @ 10:00 AM (CEST)
CheckMates Live DACH - Einführung in Check Points Hyperscalinglösung - Quantum MaestroWed 22 May 2024 @ 10:00 AM (BRT)
Brazil: Desafios e melhores práticas na gestão de CibersegurançaAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center