- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- New -Easy Migration from Azure Firewall to Check P...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
New -Easy Migration from Azure Firewall to Check Point
Hi All,
I’m happy to share a small PowerShell script that will save you a ton of time when you decide to switch from Azure Firewall to Check Point CloudGuard Network Security.
The script will export your firewall policies on Azure, including all of its objects, to multiple CSV files.
Then, import the CSV files to your Check Point management machine.
At the end of the process, you will get all the objects and policies created on the Check Point management machine.
Depending on your policy size on Azure, the entire process, end to end, should not take more than 10 minutes.
The PowerShell script is attached to the end of the post.
Here is a quick how-to guide (At the end of this guide, you will also find a tutorial video)
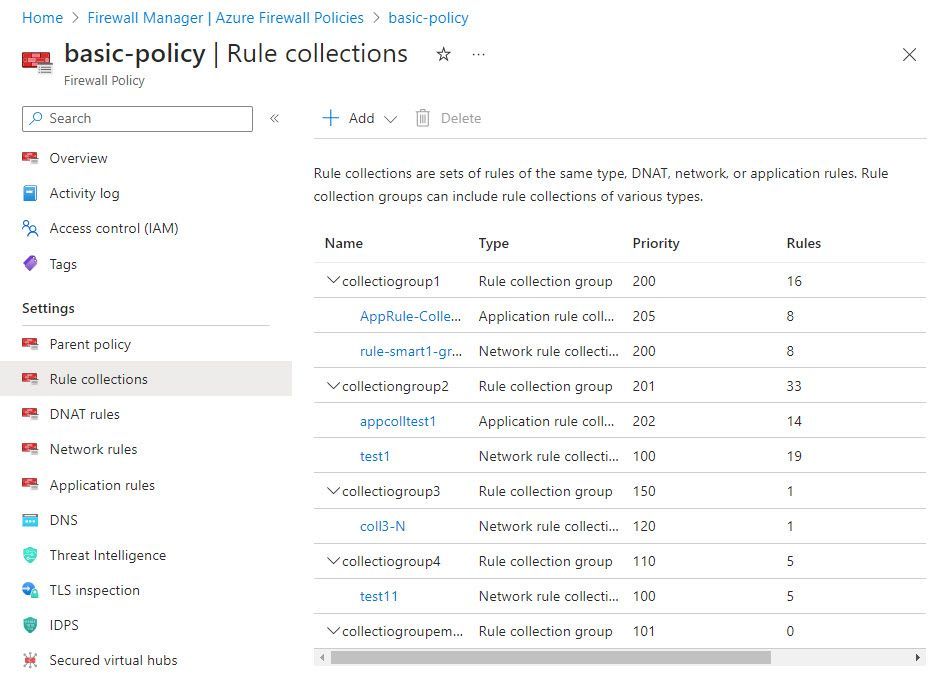
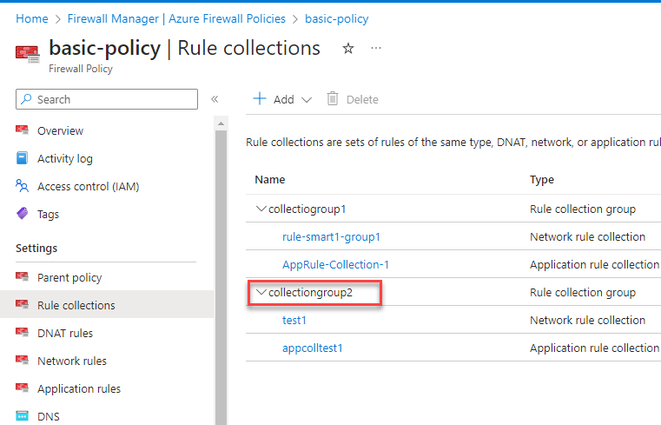
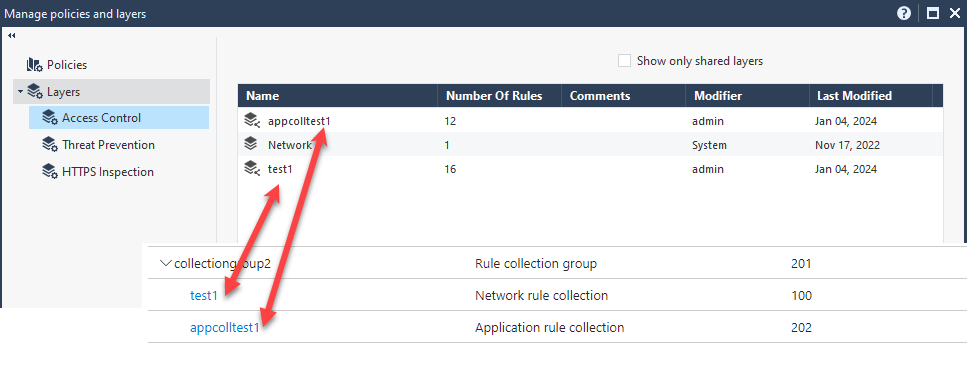
On the Azure Firewall, I have a firewall policy with five collection groups.
Each collection group consists of one or more rule sets (network rule collection and Application Rule collection)
When you run the PowerShell script, run it against all the collection groups at once.
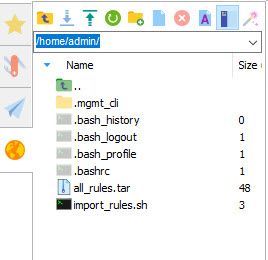
First, download the attached zip file, and export its content to a temp directory.
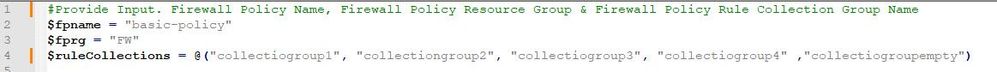
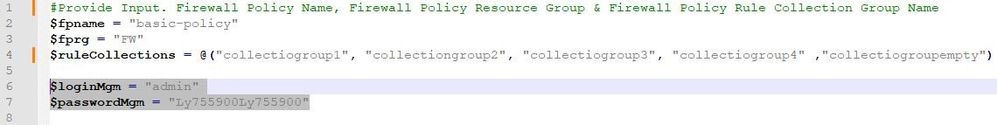
Open the PowerShell script in Notepad++ and replace the values in rows 2, 3, and 4
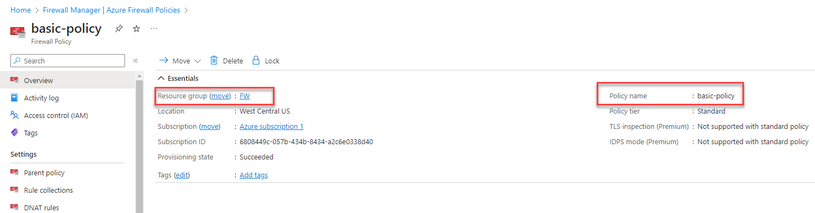
The $fpname value should be replaced with the policy name.
The $fprg value should be replaced with the policy resource group.
The $fprcgname should be replaced with the collection group names.
Set your Check Point management username and password on rows 6 & 7.
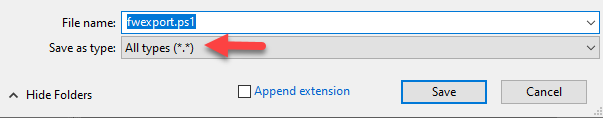
Create a folder C:\temp\export
Save the file fwexport.txt to the new Folder, and ensure the extension is ps1.
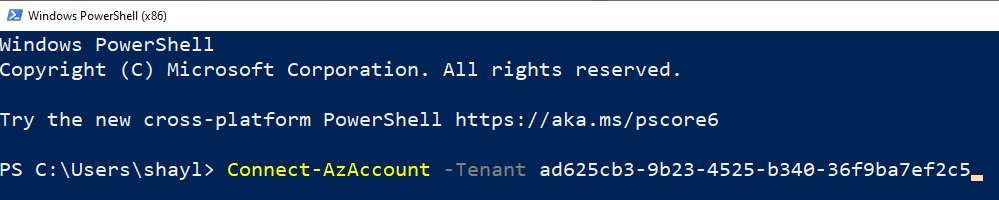
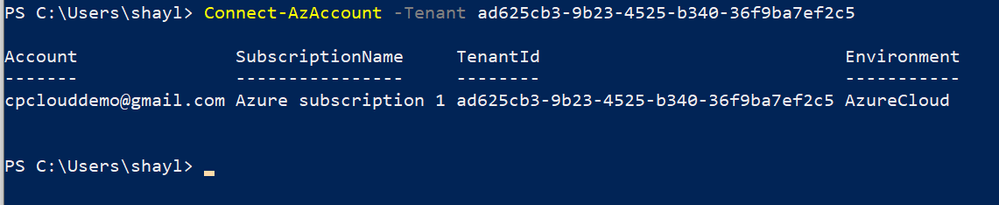
Open PowerShell and log in to your Azure Tenet ( Connect-AzAccount –Tenant ‘tenant-id’ )
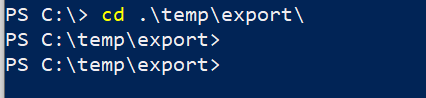
Switch the directory to C:\temp\export
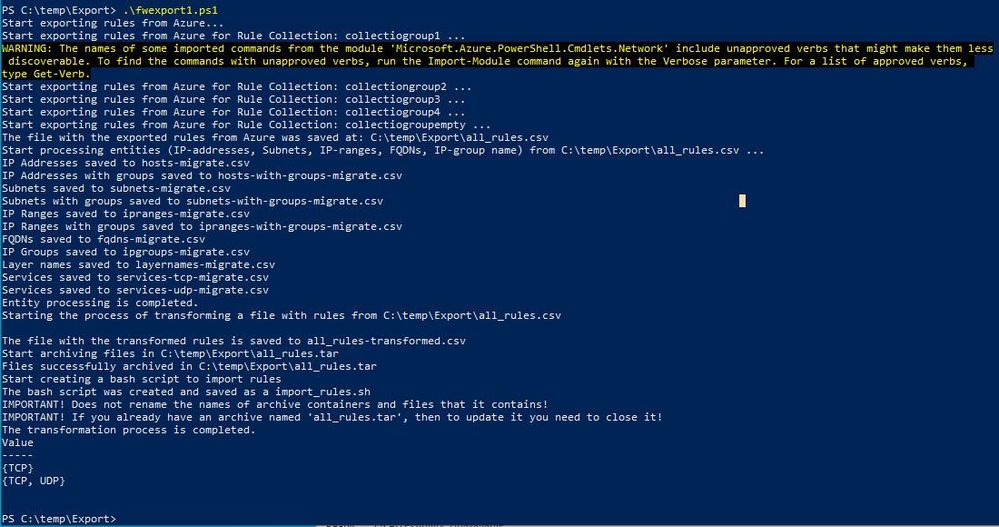
Run the PowerShell script
The script will export the policy and create a tar file with multiple CSV files that include all the required objects. (Be patient; it might take a few minutes ….)
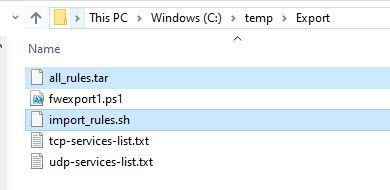
Two files will be created, *.tar & *.sh
Copy the two files to the home folder of the Check Point management machine.
Copy the two files to the home folder on the Check Point management.
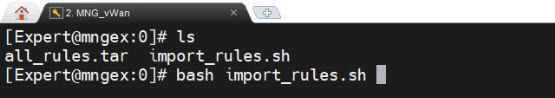
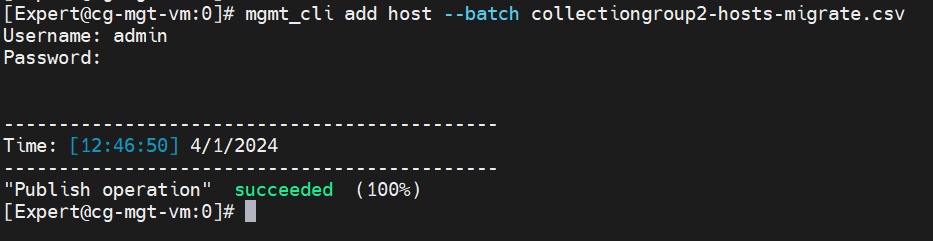
Open SSH to the Check Point management machine ( switch to expert mode ) and run the command: bash import_rules.sh
The script will extract the tar file and import each one of the CSV files.
** If you prefer to import each file manually, you can extract the tar file and run the command below in the following order:
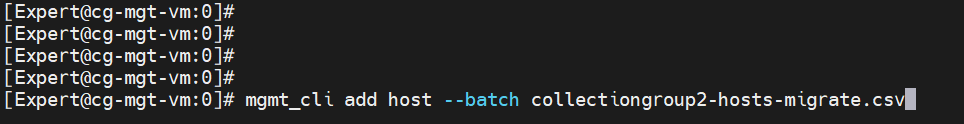
mgmt_cli add host --batch hosts-migrate.csv
mgmt_cli add network --batch subnets-migrate.csv
mgmt_cli add address-range --batch ipranges-migrate.csv
mgmt_cli add dns-domain --batch fqdn-migrate.csv
mgmt_cli add group --batch ipgroups-migrate.csv
mgmt_cli add access-layer --batch layernames-migrate.csv
mgmt_cli set host --batch hosts-with-groups-migrate.csv
mgmt_cli set network --batch subnets-with-groups-migrate.csv
mgmt_cli set address-range --batch ipranges-with-groups-migrate.csv
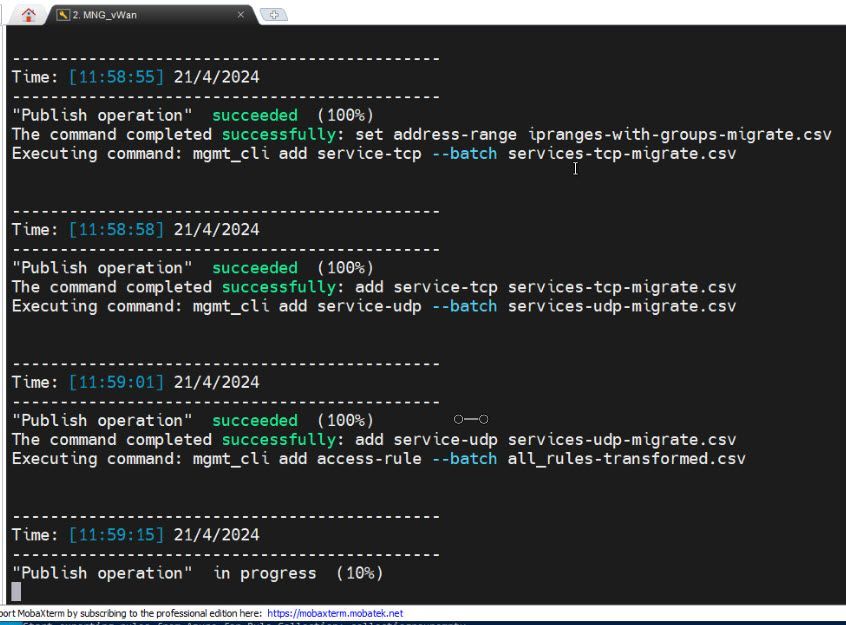
mgmt_cli add service-tcp --batch services-tcp-migrate.csv
mgmt_cli add service-udp --batch services-udp-migrate.csv
mgmt_cli add access-rule --batch all_rules-transformed.csv
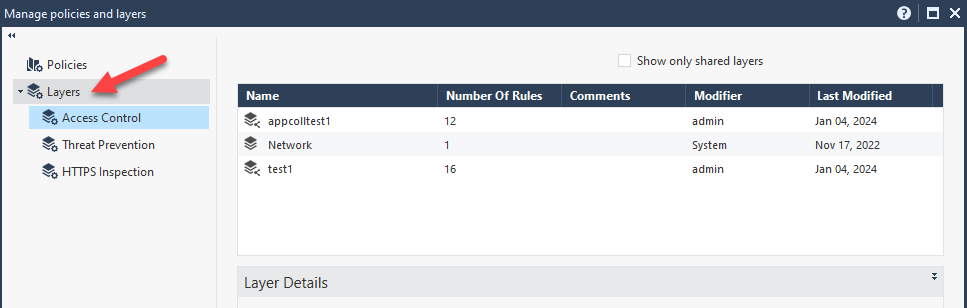
Once all the CSV files have been imported, Open SmartConsole and open Policies & Layers with ‘Ctrl+o’
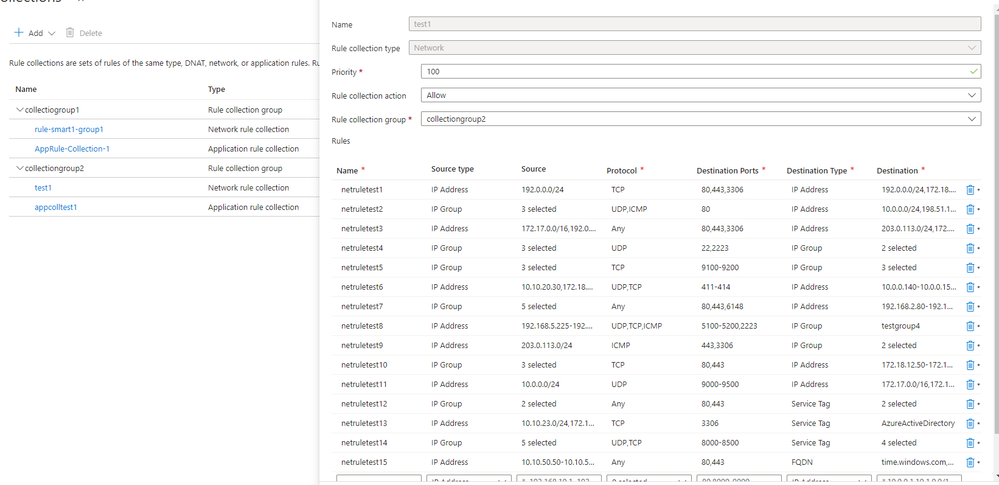
Click on the Layers tab, and you will see on the right pane the two new layers that have been imported (test1 and appcollection1)
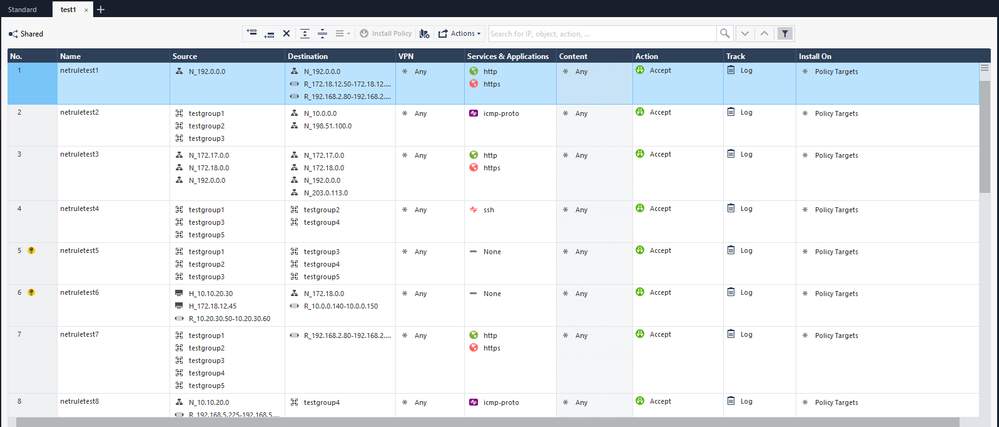
Right-click on each layer and open it in a new tab.
Now, you can use this layer or just copy multiple rules from one layer to a different policy or different layer.
Limitations:
Feel free to edit the script and adjust this list per your needs.
1. On Azure Policy, The Destination Type: ‘Service Tag’ in the Network Rule Collection will not be translated; in this case, the destination in the Check Point policy will be ‘none’
- On Azure Policy, Destination Type: ‘FQDN Tag’ and ‘Web Categories’ in the Application Rule Collection will not be translated; in this case, the destination in the Check Point policy will be ‘none.’
- On Azure Policy, DNAT Rules – Export is not supported at this stage.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great work @Shay_Levin !
"I’m happy to share a small PowerShell script that will save you a ton of time when you decide to switch from Azure Firewall to Check Point CloudGuard Network Security."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Shay_Levin Just curious, is this officially supported by TAC in case process does not work as expected?
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
TAC does not support it, but anyone with an issue can post here or message me directly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great, thats fair, thanks very much.
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another quick question, sorry...does the script support importing ALL kinds of rules or ONLY security rules?
Any idea?
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Security rules and application rules are supported.
The above two are heavy-lifting; the DNAT Rules, Threat Intelligence, and IDPS will not require much time to convert manually if needed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Got it, thanks a lot. Sorry for all my questions.
Best,
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great Work !!! Amazing Post 8)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Shay_Levin
We are planning to migrate from Azure firewall to Check Point NVA? As part of that, can you please help me pre-requisites for running this script.
We have Check Point MDS running in R81 version with 51 CMA.
Is this supported in MDS environment with R81 version? If so, what are the pre-requisites, such as do we need to explicitly enable any feature or option something like that?
Do we need to run this script from MDS context or specific CMA, so that it will create policies on that CMA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81 is supported.
For the import, you will need to do the following process :
Export the tar file.
mgmt_cli login user admin password your-password domain "Domain-Name" > id.txt
mgmt_cli add host --batch hosts-migrate.csv -s id.txt
mgmt_cli add network --batch subnets-migrate.csv -s id.txt
mgmt_cli add address-range --batch ipranges-migrate.csv -s id.txt
mgmt_cli add dns-domain --batch fqdns-migrate.csv -s id.txt
mgmt_cli add group --batch ipgroups-migrate.csv -s id.txt
mgmt_cli add access-layer --batch layernames-migrate.csv -s id.txt
mgmt_cli set host --batch hosts-with-groups-migrate.csv -s id.txt
mgmt_cli set network --batch subnets-with-groups-migrate.csv -s id.txt
mgmt_cli set address-range --batch ipranges-with-groups-migrate.csv -s id.txt
mgmt_cli add service-tcp --batch services-tcp-migrate.csv -s id.txt
mgmt_cli add service-udp --batch services-udp-migrate.csv -s id.txt
mgmt_cli add access-rule --batch all_rules-transformed.csv -s id.txt
mgmt_cli publish -s id.txt
Ensure you execute it in the precise sequence provided
*** Per a request of one of our enterprise customers, I have updated the script to support the export of multiple collection groups at once and also migrate the service.
I will update the post by the end of the day tomorrow with the new PowerShell script and its instructions.
If you want to wait another week, I will also add support for importing all the objects to the MDS without running the mgmt_cli against each one of the CSV files.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Shay_Levin
Can we have 5 to 10 minutes call when you free next week? so I can show you and clarify my doubts. We are planning to move out from Azure firewall to Check Point NVA in all regions. Hence, this script will be more helpful for us. As we have multiple Rule Collection Groups (RCG) and multiple rule collection in each RCG.
Please reach out me through my mail id or share your email id whichever is okay for you, so I can contact you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Shay,
Great work 🙂
I might be missing the info, but is this supported for MDS by now?
Thanks for the great work.
Rasmus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Import into MDS is supported but you would not be able to do it with the bash script but import each one of the CSV files manually,
Check my reply above to Nandhakumar_N
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This script works in fantastic way and we have successfully completed our migration. This script saves our huge manual efforts and complete migration in timely manner.
I can confirm, it works fine in MDS environment. Thanks @Shay_Levin for your help with this 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the feedback 🙂