- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- CheckPoint IaaS VMSS -Azure - Doubt in Outbound NA...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CheckPoint IaaS VMSS -Azure - Doubt in Outbound NAT for Internal server
Dear CheckMates,
I have CheckPoint VMSS working in Azure.
I have given Hide NAT behind Gateway for Internal Server, so it gets Hide behind one of VMSS and reaches Internet - works fine
Requirement is - I want to Hide NAT my Internal Server to a New Public IP (Not to use any of VMSS Public IP)
I tried creating New External Interface in VMSS and able to Hide NAT my Internal Server to that New IP.
Outbound packet gets Hide NAT with New IP, but UNABLE to see REPLY traffic from Internet.
Is there any way to achieve the Outbound Hide NAT for Internal Server using New IP apart from VMSS IP?
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure exactly what you can do on the Azure side to make this work, but that is where the issue lies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello PhoneBoy,
Yeah looks like that will not work as I had made many trials and reason could be in "ifconfig" of VMSS where the Primary External Interface is tagged and no other External can be added onto its NIC settings (ens192P2g3..... adapter is bound for eth0 ONLY)
Now as per document I'm doing the below and still unable to get it done.
1) Created CheckPoint VMSS without ILPIP.
2) Integrated with Mgmt Server with Frontend NIC Private IP of VMSS
3) Created Inbound LB rule in FrontendLB to reach Internal Server - works fine
4) Now my VMSS & Internal Server both don't have Internet Outbound Connectivity.
5) As per CheckPoint document and Azure, I had given Outbound Rule in FrontendLB so that Backend VMSS instances will get Outbound Internet using FrontendLB Public IP.
But no luck. I tried some NAT in SmartConsole on VMSS Objects and subnets for Internal Server - -No Luck
Any idea how should I achieve the Outbound Internet Connection for my VMSS instances which has ONLY Private IP (No ILPIP) and for Internal Servers
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Prabu,
according to the information on this page Azure LB I guess it´s too complicated for a VMSS as outbound Load Balancing Rules have the following limitation:
< Outbound rules can only be applied to primary IP configuration of a NIC. You can't create an outbound rule for the secondary IP of a VM or NVA. Multiple NICs are supported.
So you would have to add NICs to each ScaleSet Member , not sure if this is supported by Checkpoint at all.
In addition, the LB has to be of type "Standard", with a Basic LB you can not configure outbound Rules.
May be a Single GW or Checkpoint Cluster for outbound traffic could be a alternative ?
At least for a Single GW I have tested it that way:
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias,
Yes I could create additional NIC but it cannot be used for Outbound traffic.
Yes in Single GW it is working but not in Cluster & VMSS.
Anyways I could able to get Internet Outbound for VMSS & Internal servers with FrontendLB's IP as my VMSS don't have ILPIP.
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Prabu,
<Yes I could create additional NIC but it cannot be used for Outbound traffic.
Have you studied the provided microsoft link:
With outbound rules, you can explicitly define outbound SNAT behavior.
Outbound rules allow you to control:
- Which virtual machines are translated to which public IP addresses.
- Two rules were backend pool A uses IP address A and B, backend pool B uses IP address C and D.
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias,
Yes had looked into SNAT behavior.
But in my setup - For FrontendLB - The backend Pools weer only VMSS and no other Internal VMs.
So I made HIDE NAT with All gateway(VMSS) for Internal machine so that Internal machine will Hide behind VMSS and go outside.
Had Outbound Rules for VMSS to use FrontendLB Public IP. So my both VMSS & Internal VMs use FrontendLB IP for outgoing Traffic.
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Prabu,
the backend Pool consists of NICs, not VMs. As you would have a VM/scaleset with multiple NICs you could define two backendPools on the external LB, each containing a different NIC of the same VM/scaleset
Same is true for your external and internal LB which is deployed with your VMSS. Check the backend Pool of these LBs, same scaleset but different NICs
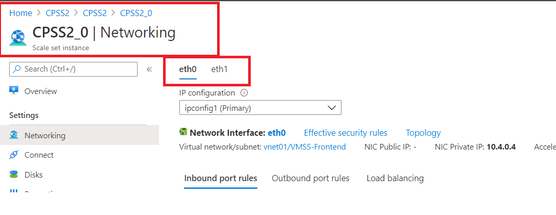
(eth1 with the backend-lb, eth0 with the frontend-lb)
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias,
Created New NIC on VMSS instance and tried to add or create New backendpool for this new NIC - no luck.
Its not getting added fo new NIC VMSS instance.
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Prabu,
I guess you still have only two NICs at the instance level ?
Regards
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias,
I created 3rd NIC as External apart from etho(External) & eth1(Internal).
So already 1st backendpool for FrontendLB has been tagged with eth0 of VMSS.
Now if I try to create 2nd backendpool with 3rd NIC of VMSS - unable to do so.
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Prabu,
when I added a 3rd NIC , I had to redeploy the already running instances. Only then the 3 NICs where available at the instance level and I could add a further backend pool with the third NIC.
Have you done this ?
Regards
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias,
Yup after new VMSS spinned, I can see 3rd New NIC as well.
Created 2nd Backendpool to tag New NIC, but unable to do so.
Thats where I was stuck.
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Prabu,
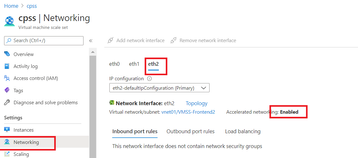
look´s like the NIC has to have network acceleration enabled (which is not the case if added via the Azure Portal).
If doing so via azure CLI like:
az vmss update -g cpss --name cpss --set virtualMachineProfile.networkProfile.networkInterfaceConfigurations[2].enableAcceleratedNetworking=true
i was able to add a 2nd Backenpool. (after redeploying the instance again)
After configuring a outbound rule, the second public IP of the external LB was used.
Regards
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias,
Let me try your action.
In Azure CLI - Should i need to replace any text in below:
az vmss update -g cpss --name cpss --set virtualMachineProfile.networkProfile.networkInterfaceConfigurations[2].enableAcceleratedNetworking=true
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Prabu,
yes, the name is the resource group the scalest ist deployed in and after the "-g" switch you have to add the name of your scaleset.
If it is succesfull, the added NIC (I called it eth2) should have acceleration enabled:
After that, you have to redeploy the instance again.
Regards
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias,
Thanks for your input, I could able to create 2nd BackendPool & tagged New NIC as well.
Now my requirement is that my VMSS should go Outbound to Internet thru this New NIC.
It doesn't work if I do as above?
It works only thru backendpool which has eth0..Not with backendpool which has newnic
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Prabu,
your VMSS is using eth0 as your default route is through eth0, I guess ?
If you change the default route to the first IP of the newnic network it will use that interface
But if I get it right, only your internal Server should use that new Public IP ?
Regards
Matthias
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias,
I also changed the Default route in VMSS from eth0 to newnic & checked. VMSS lost Internet connection. (Then changed back from newnic to eth0 in Default Route - started woking)
For Internal server, I made HIDE NAT of NewNIC IP of VMSS.
No luck.
Seems to me a limitation????
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Prabu,
did you put the newnic (10.10.10.5) in the same subnet as eth0 (10.10.10.4) ?
Regards
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes of course.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In some cases you may wants to allow the outbound from a static IP , AFAIK You cant use different IP but may be you can ensure for particular destination traffic should route via particular gateway . adding a nic is complicated and not recommended approach
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
was this problem solved somehow in the meantime? We've got multiple VMSS (and more than 500 CP FWs) and need use PIP per source for security reasons (whitelist on other end). Group of Azure machines using specific PIP for specific Internet destination. For VMSS it is clear from discussion that adding NIC manually does not work (and is not desirable due to manageability). There would have to be NIC per PIP pretty much + .
Different scenarios:
VMSS not possible to use because of Azure LB limitation
- Primary NIC only, no multiple NICs
- no secondary IPs supported
Checkpoint Cluster does not work
- mentioned by someone in thread earlier
Single GW not possible
- load limitation and lack of redundancy
Two or more standalone CP gateways behind internal loadbalancer ?
- PIPs per GW per purpose following what Matthias done for single GW
- that also means FW policy per GW because of NAT or how could this be solved? Security zones even with version R81 can not be used because it is same interface with multiple secondary IPs...
Any help appreciated.
Best regards