- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast Weekly Reports - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Check Point
for Beginners
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Educational Resources
- :
- Check Point for Beginners
- :
- Part 10 - Identity Awareness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
OPEN OTHER ARTICLES
 Part 1 - The Architecture
Part 1 - The Architecture
 Part 2 - Preparing the Lab
Part 2 - Preparing the Lab
 Part 3 - Installing Security Management Server
Part 3 - Installing Security Management Server
 Part 4 - Installing Security Gateway
Part 4 - Installing Security Gateway
 Part 5 - Gaia WebUI and CLI
Part 5 - Gaia WebUI and CLI
 Part 6 - Working with SmartConsole
Part 6 - Working with SmartConsole
 Part 7 - Managing Security Policies
Part 7 - Managing Security Policies
 Part 8 - Network Address Translation
Part 8 - Network Address Translation
 Part 9 - Application Control, URL Filtering and Content Awareness
Part 9 - Application Control, URL Filtering and Content Awareness
 Part 11 - Threat Prevention
Part 11 - Threat Prevention
 Part 12 - Logs and Reporting
Part 12 - Logs and Reporting
 Site to Site VPN in R80.x - Tutorial for Beginners
Site to Site VPN in R80.x - Tutorial for Beginners
 Absolute Beginner’s Guide to R80.x
Absolute Beginner’s Guide to R80.x
 Handling Traffic in the Access Policy - Knowledge Nuggets
Handling Traffic in the Access Policy - Knowledge Nuggets
 Video - Security Administration Experience
Video - Security Administration Experience
 Video - Securing Hybrid Cloud Environment
Video - Securing Hybrid Cloud Environment
 Video - Smart-1 Cloud - Cloud Based Security Management
Video - Smart-1 Cloud - Cloud Based Security Management
 Video - Container Security
Video - Container Security
 Video - Identity Based Segmentation
Video - Identity Based Segmentation
 Video - Securing Public Cloud Environment
Video - Securing Public Cloud Environment
 Video - Threat Hunting, Detection, and Monitoring
Video - Threat Hunting, Detection, and Monitoring
 Video - Firewall as a Service (FWaaS)
Video - Firewall as a Service (FWaaS)
 Video - Application Control and URL Filtering
Video - Application Control and URL Filtering
 Video - TLS Inspection
Video - TLS Inspection
 Video - Hyper Scale Clustering with Quantum Maestro
Video - Hyper Scale Clustering with Quantum Maestro
 Video - Check Point R81.X - Crash Course - Introduction
Video - Check Point R81.X - Crash Course - Introduction
 Video - Check Point R81.X - Crash Course - Admin GUI
Video - Check Point R81.X - Crash Course - Admin GUI
 Video - Check Point R81.X - Crash Course - SmartConsole
Video - Check Point R81.X - Crash Course - SmartConsole
 Check Point Jump Start - Product Deployment
Check Point Jump Start - Product Deployment
 Network Security
Network Security
PREVIOUS ARTICLE
TO READ THE FULL POST
it's simple and free
NEXT ARTICLE
Part 10 - Identity Awareness
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2020-06-11
04:55 AM
Introduction
Identity Awareness (IA) allows you to easily add user, user group, and machine identity intelligence to your security defenses.
Traditionally, firewalls use IP addresses to monitor traffic and are unaware of the user and computer identities behind those IP addresses.
Identity Awareness maps users and computer identities to IP addresses, allowing you to enforce access and audit data based on identity. IA is an easy to deploy and scalable solution. It is applicable for both Active Directory and non-Active Directory based networks, as well as for employees and guest users.
Check Point supports both local and external users. Local users are defined on Security Management Server. External users are those whose records are managed on Active Directory, RADIUS, or an LDAP server.
Access Role objects define users, computers, and network locations as one object and can be used as a source or destination in a rule. Access Role objects can include one or more of these objects:
- Networks
- Users and user groups
- Computers and computer groups
- Remote access clients
The Identity Awareness Software Blade provides multiple methods to obtain a user’s identity, including:
- AD Query,
- Browser-Based,
- Identity Agents,
- RADIUS Accounting,
- Remote Access clients,
- Identity Collector and the Identity Web API.
For better understanding of IA methods, refer to Identity Awareness Administration Guide.
In this lecture, we will concentrate on Browser-Based method.
Enabling Identity Awareness
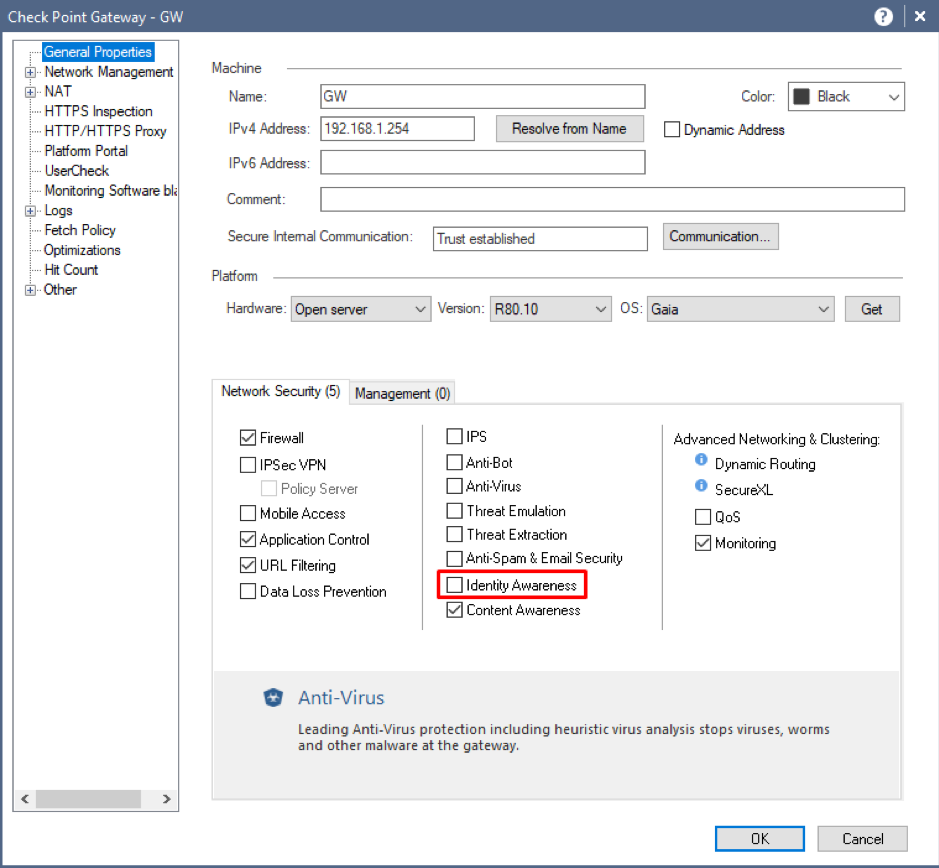
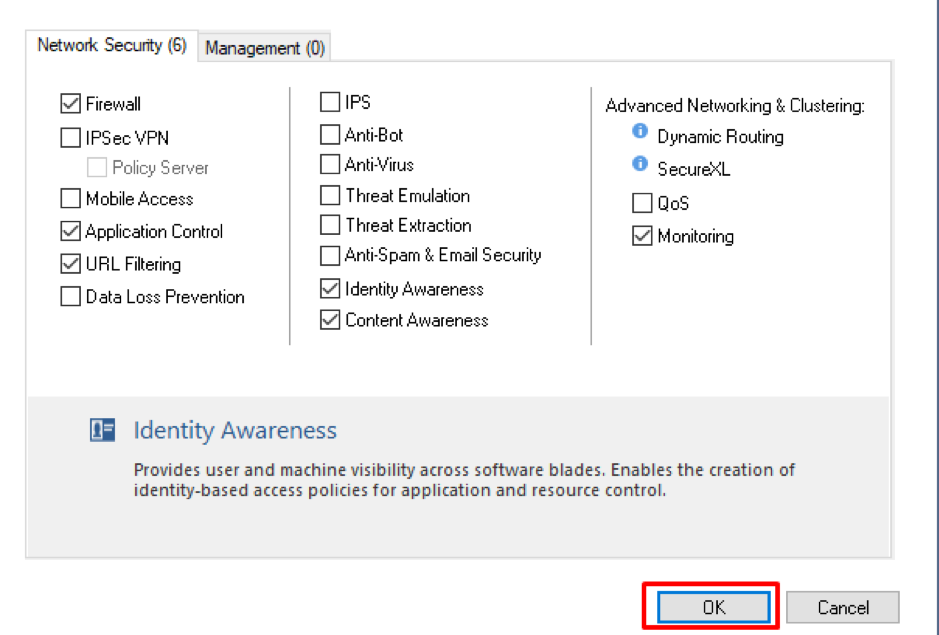
Let’s activate the IA Software Blade. Open your Security Gateway object and mark IA checkbox in Network Security space:
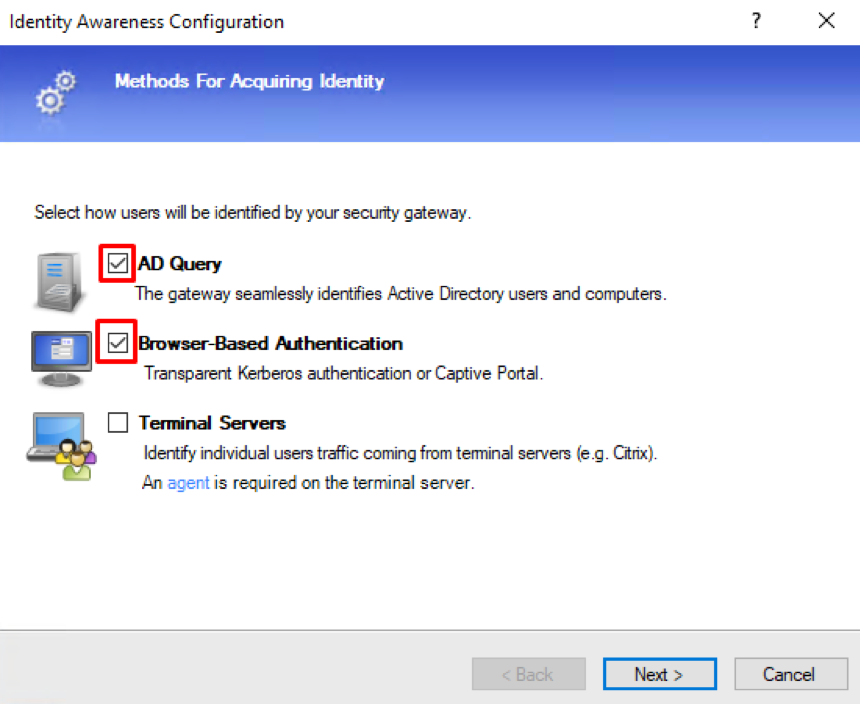
In the pop-up menu, mark AD Query and Browser-Based Authentication.
Press Next.
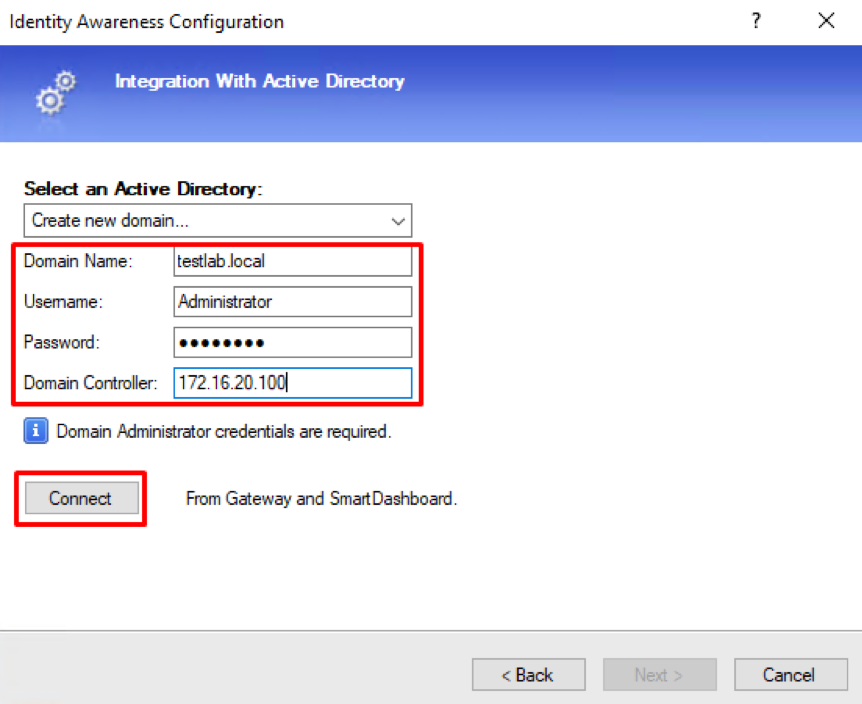
At this stage, we need to connect to our AD server. In the lab, AD server is located in the DMZ, with IP address 172.16.20.100.
You need to specify Domain Name, Username, Password, and IP address of our AD server:
You will have to use admin AD account or, alternatively, set up a special account with permissions described in sk93938.
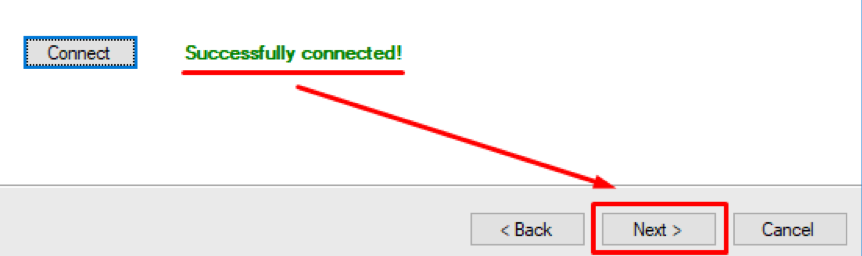
Press Connect and wait for “Successfully connected!” message to appear Press Next:
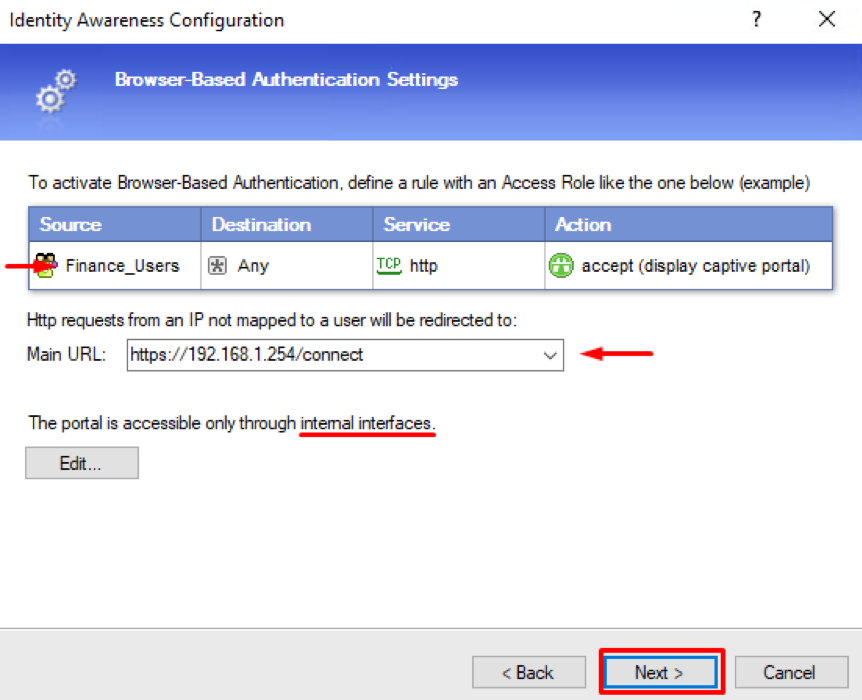
A new window explains how to set up Browser-Based Authentication. Review it carefully and press Next:
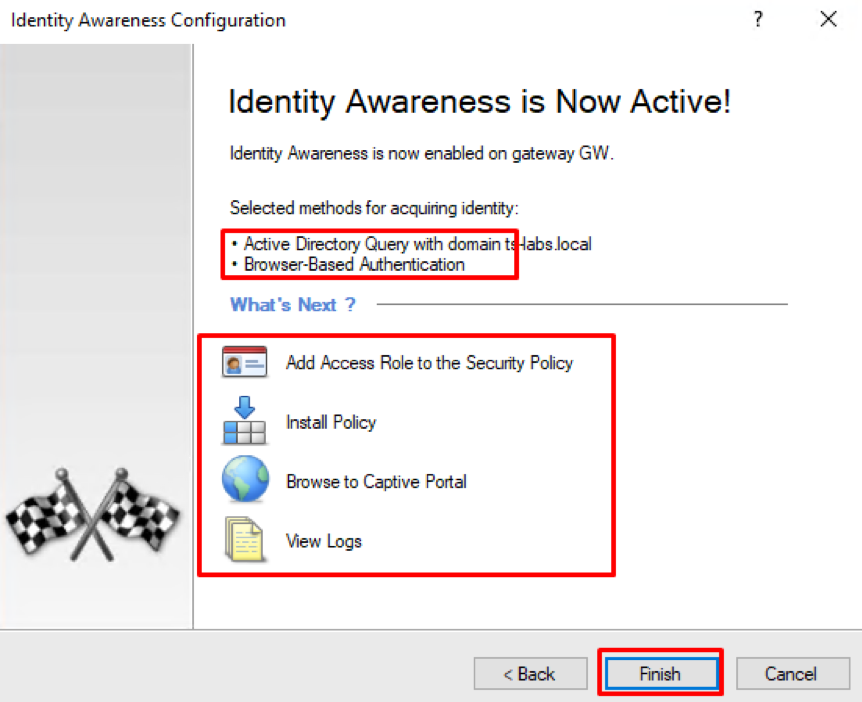
The final window shows you the summary of defined settings and provides a short instruction of setting up IA with your security policy. You can now press Finish:
Exit from the Security Gateway object by pressing OK:
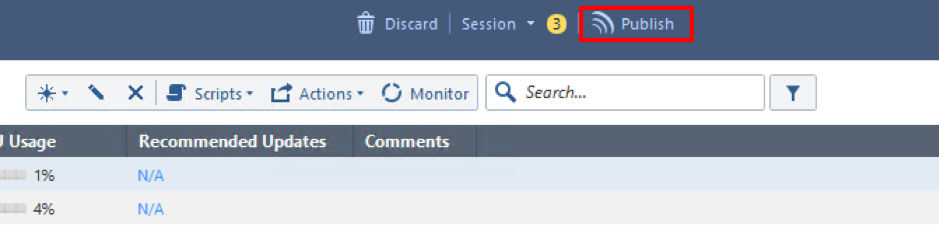
You need to publish the changes:
Adding Identity Awareness to your Security Policy
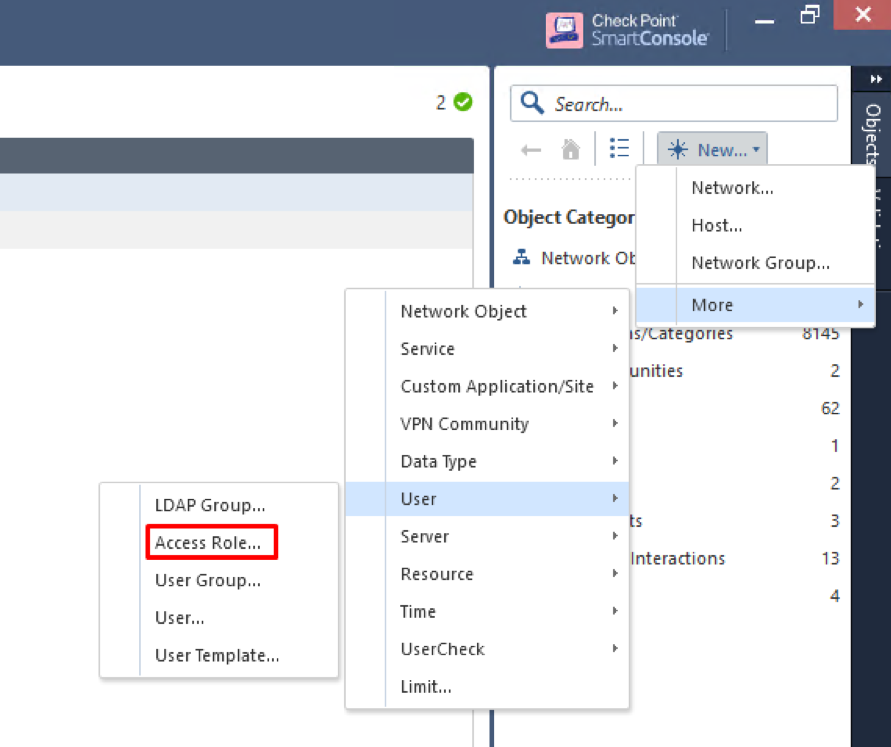
We need to set up an Access Role before moving further. Go to objects menu and choose New > More > User > Access Role:
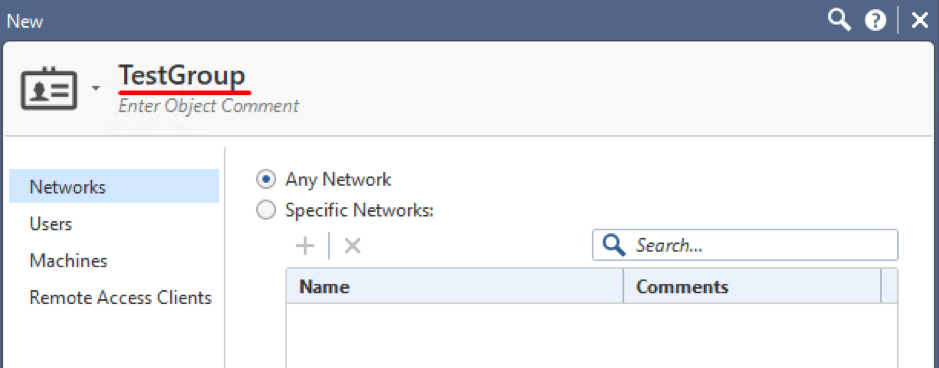
Set up a Name for your new Access Role object:
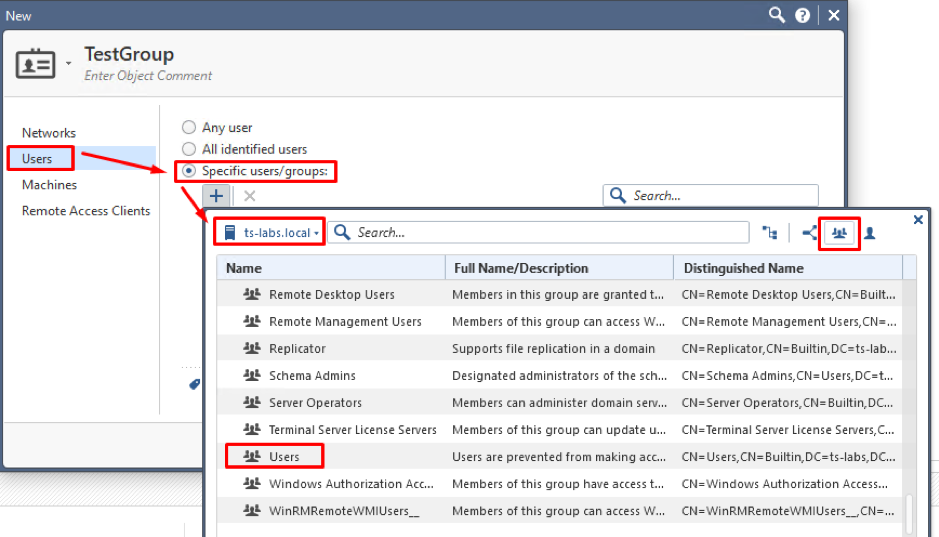
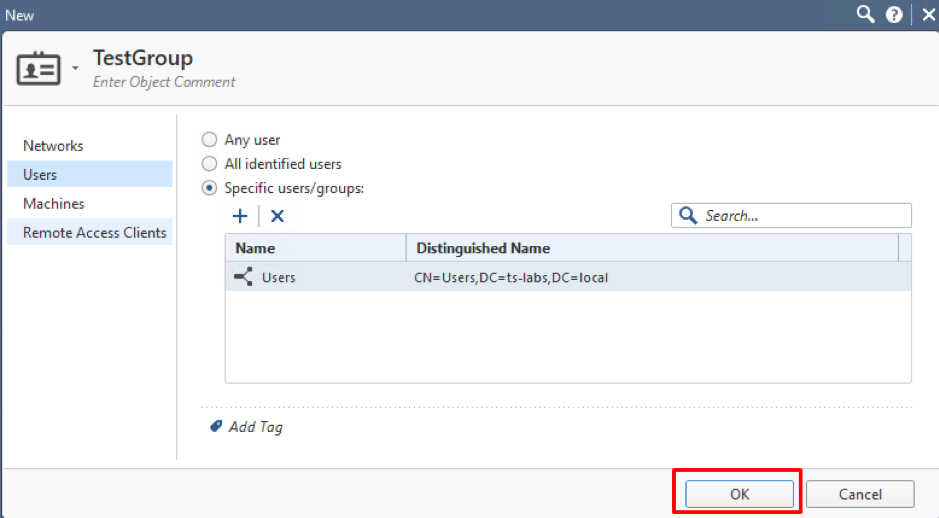
Leave Any Network in the Networks Tab. Go to the Users tab and choose a group you want to use. Note that we are skipping AD and User Group settings here:
Press OK:
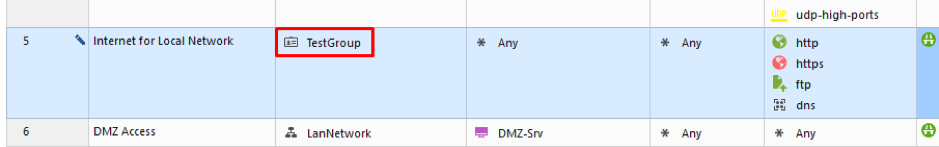
Let’s edit our Security Policy. From our rule number 5, delete LanNetwork object and replace it with our Access Role object:
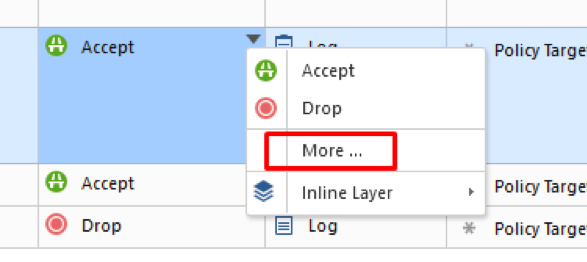
We need to activate Captive Portal. Right-click on Accept Action and chose More:
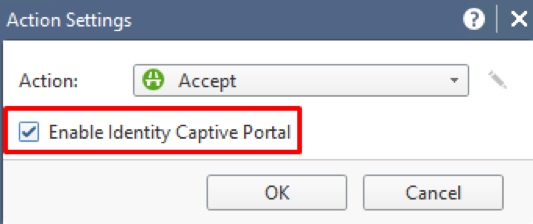
Mark Enable Identity Captive Portal:
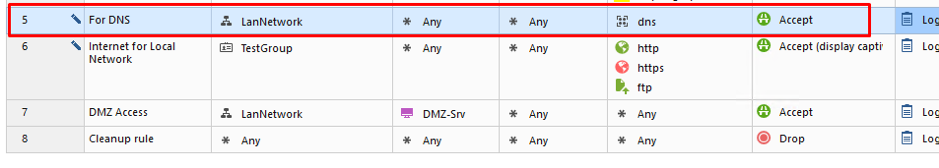
We also need to create a rule allowing DNS to function. Place this rule above one you have just edited. Our policy should look like this:
Install Policy. Now we can run some tests.
Testing Identity Awareness
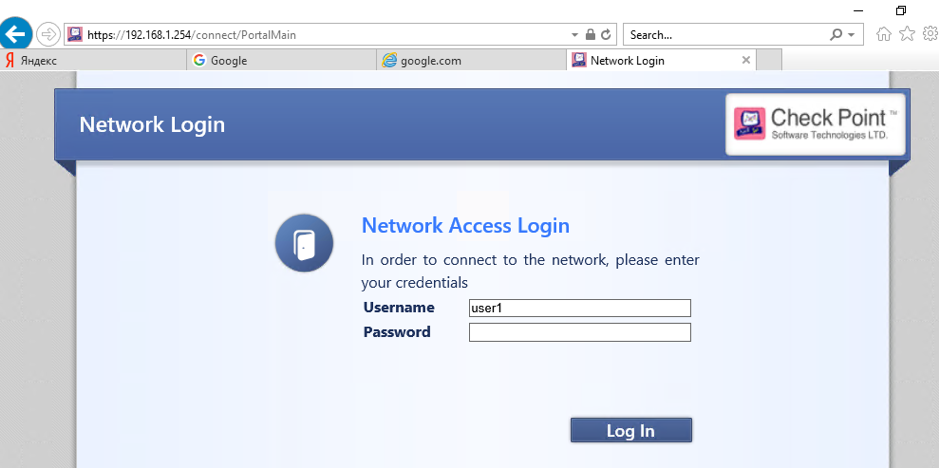
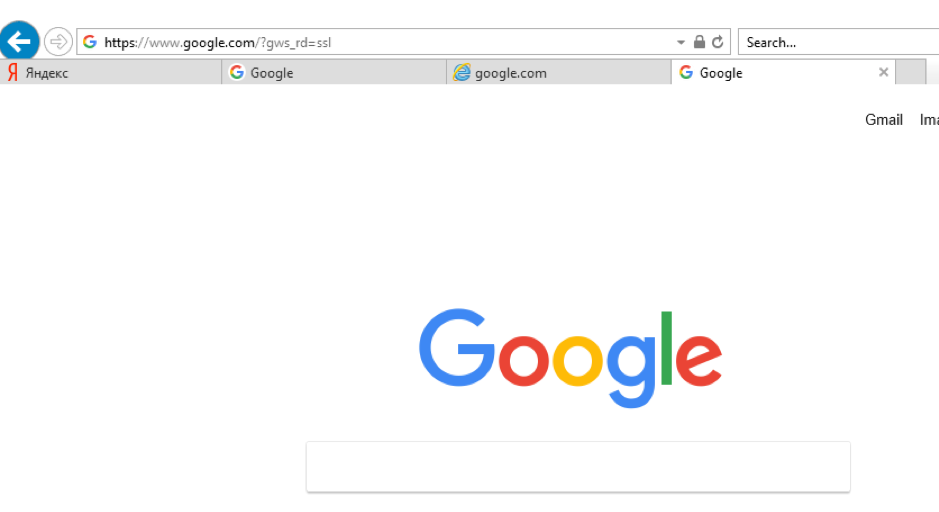
Try accessing any Web site, for example google.com. You should see an authentication prompt from your Captive Portal:
Type in username and password for your domain used and press Log In. After successful authentication, you will get the access to the requested Web site. At this point, you should be able to access other web resources without additional authentication.
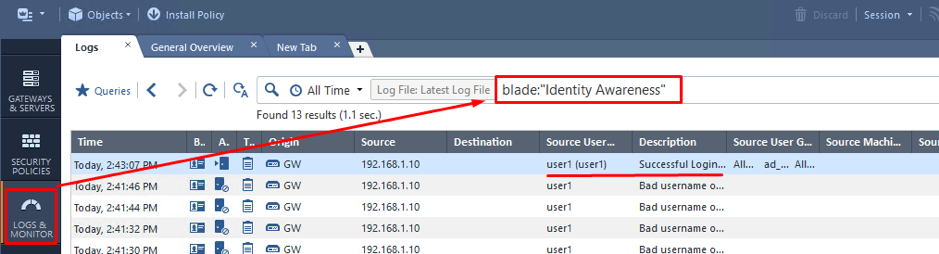
Open SmartConsole go through Identity Awareness logs:
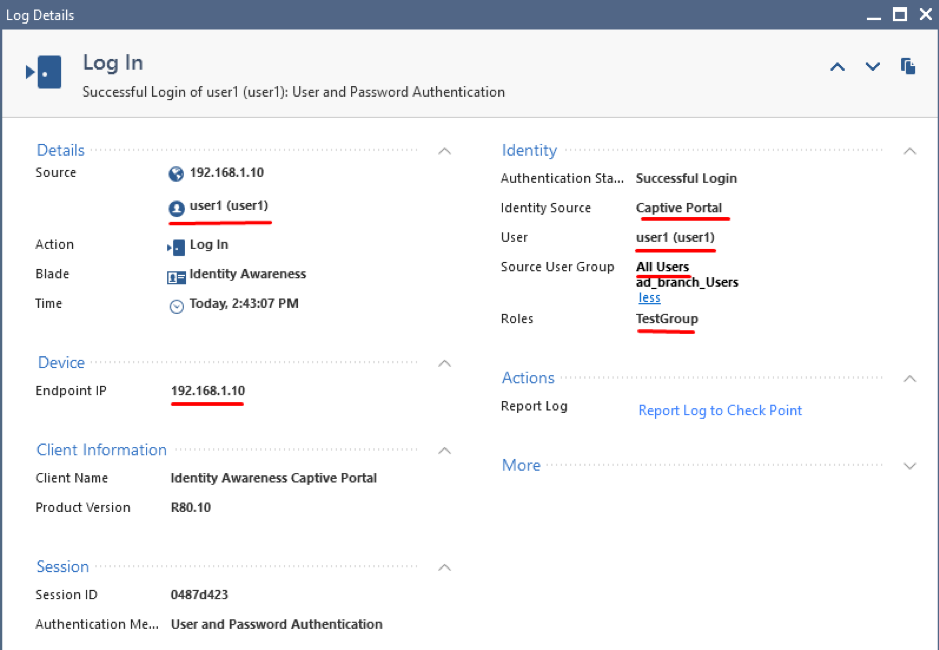
Double click on the log entry for more details:
This is the end of the lecture. Next time we will discuss Threat Prevention.
Labels
Introduction
Identity Awareness (IA) allows you to easily add user, user group, and machine identity intelligence to your security defenses.
Traditionally, firewalls use IP addresses to monitor traffic and are unaware of the user and computer identities behind those IP addresses.
Identity Awareness maps users and computer identities to IP addresses, allowing you to enforce access and audit data based on identity. IA is an easy to deploy and scalable solution. It is applicable for both Active Directory and non-Active Directory based networks, as well as for employees and guest users.
Check Point supports both local and external users. Local users are defined on Security Management Server. External users are those whose records are managed on Active Directory, RADIUS, or an LDAP server.
Access Role objects define users, computers, and network locations as one object and can be used as a source or destination in a rule. Access Role objects can include one or more of
...
3 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter