- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- Need To Perform Mass Modification Of All User Acco...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Need To Perform Mass Modification Of All User Accounts Expiration Dates
It came to my attention today that I have a large number of user accounts expiring on 1/1/2020. Given the number, it would be best to update these en masse. I have seen a couple other posts where some folks were accomplishing this using a series of API requests / changes. However, I also came across this older sk article: sk522
Can anyone comment whether this is still a valid method on an R80.30 SMS? I'm not opposed to going the API route if necessary, but this method seems to accomplish the same thing in a single command.
Thanks!
Dan
R80 CCSA / CCSE
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.30 SMS does know nothing about this commend and tells us:
Usage:
fwm ver [-f] ... # Display version
fwm load [opts] [filter-file|rule-base] targets # Install Policy on targets
fwm dbload [targets] # Download the database
fwm logexport [-h] ... # Export log to ascii file
fwm ikecrypt <key> <password> # Crypt a secret with a key
# (for the dbexport command)
fwm kill [-sig_no] procname # Kill firewall process
fwm getpcap ... # Fetch packet capture from gateway
I have added a feedback to sk522 and asked for versions R80.xx...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good catch! I didn't notice that it wasn't listed in the syntax options for fwm.
Perhaps this is why other members were coming up with API-based solutions. Which I'm opposed to if that is truly the only, or best, way!
Thanks!
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
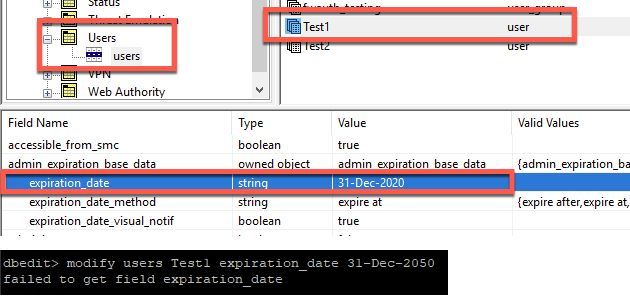
This is also interesting, it looks like you should be able to do this via dbedit, but it returns "failed to get field expiration_date" when attempting to modify it...
Is there something dumb I'm just not seeing here? 😫
Edit: Does this have something to do with expiration_date being under the admin_expiration_base_data opened object?
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Easy explanation (see skI3301 How to use the dbedit utility):
In R7x, dbedit could be used for manipulating all object stored in objects_5_0.C and in other fwset files.
In R80.x, the tool is still supported, but it can manipulate only some of the objects (gateways and global properties for instance), while other objects (such as rulebase) can be managed only by the new mgmt_cli tool.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This can be done using the API using the set administrator command. It will have to be performed against the "System Data" domain.
[mgmt01]# mgmt_cli -d "System Data" -u admin login > session.id
[mgmt01]# mgmt_cli -s session.id show administrators details-level full -f json | jq -r '.objects[]|[.name,."expiration-date"."iso-8601"]|@csv' > users.csv
On my test system, this responds with the following content:
"admin","2030-12-31T00:00-0500"
"cam","2020-01-01T00:00-0500"
"pam","2020-01-01T00:00-0500"
"sam","2020-01-01T00:00-0500"
The CSV file can then be edited to change the expiration dates of the users that expire on 2020-01-01. I have also added the header row of "name, expiration-date" in order to use it in batch mode.
name,expiration-date
"pam","2021-01-01T00:00-0500"
"sam","2021-01-01T00:00-0500"
Running the command and then verifying the changes
[mgmt01]# mgmt_cli -s session.id -b users.csv set administrator
[mgmt01]# mgmt_cli -s session.id show administrators details-level full -f json | jq -r '.objects[]|[.name,."expiration-date"."iso-8601"]|@csv' > changes.csv
[mgmt01]# more changes.csv
"admin","2030-12-31T00:00-0500"
"cam","2020-01-01T00:00-0500"
"pam","2021-01-01T00:00-0500"
"sam","2021-01-01T00:00-0500"
Don't forget to publish and logout of your API session when complete.
[mgmt01]# mgmt_cli -s session.id publish
---------------------------------------------
Time: [05:47:48] 2/12/2019
---------------------------------------------
"Publish operation" succeeded (100%)
... <snipped>
[mgmt01]# mgmt_cli -s session.id logout
message: "OK"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for this!! This seems like the best course to take since dbedit doesn't appear to support those fields anymore.
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Would be nice if we could find this in SK - an equivalent of sk522 How to perform a mass modification to all user accounts' expiration dates for R80.xx...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a followup question as I just ran this command in my test environment. It looks like this query is only returning Check Point Administrator accounts. I apologize if I wasn't clear from the beginning, these are users defined as RADIUS users for Client Authentication purposes.
I'm assuming this output is because we are querying administrators by using "show administrators". Is there an equivalent query to see non-Administrator users?
This would be users appearing under Users -> Users in the Object Explorer, for example:
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So that's my misunderstanding. Your subject clearly states "All User Accounts" and has nothing to do with Administrators. 😲
There does not appear to easily display and edit the users list via the mgmt_cli command. You can export the list of users via Object Explorer in SmartConsole to review their expiration dates. If you have that information, it is possible to track down the UIDs of each user (manually) and use the generic-object API to manipulate the expiration date. This is how I handled it in my test environment.
Since this uses the generic-object API, please proceed with caution.
I created a user "usertest" in Smartconsole. Using the show object with a filter for the username as well as a select filter in JQ, I was able to retrieve the UID for the usertest user object.
[mgmt01]# mgmt_cli -s session.id show objects filter usertest -f json details-level full | jq '.objects[]|select(.type=="CpmiUser")|[.name,.uid,.expirationDate]|@csv'
"\"usertest\",\"75bbb024-de6b-46b1-934f-cea899f7a285\",\"01-Jan-2020\""
Once the UID has been found, the adminExpirationBaseData.expirationDate setting can be adjusted to the new date.
(For full details on the object, use "mgmt_cli show generic-object uid <UID> details-level full"
[mgmt01]# mgmt_cli -r true set generic-object uid 75bbb024-de6b-46b1-934f-cea899f7a285 adminExpirationBaseData.expirationDate "01-Jan-2021"
---------------------------------------------
Time: [13:46:17] 2/12/2019
---------------------------------------------
"Publish operation" succeeded (100%)
WARNING: If you mess-up the date field on the user, it will not be properly set. Using a numeric date does not appear to work and will leave the expiration missing.
Results
[mgmt01]# mgmt_cli -s session.id show objects filter usertest -f json details-level full | jq '.objects[]|select(.type=="CpmiUser")|[.name,.uid,.expirationDate]|@csv'
"\"usertest\",\"75bbb024-de6b-46b1-934f-cea899f7a285\",\"01-Jan-2021\""
Keep in mind that use of the generic-object API is not recommended as it's quite possible to quickly mess things up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's strange, using your example, I can't seem to find any of these objects in our DB:
mgmt_cli -s session.id show objects filter Test1 -f json details-level full
{
"total" : 0,
"objects" : [ ]
}
mgmt_cli -s session.id show objects filter fwauth -f json details-level full
{
"total" : 0,
"objects" : [ ]
}
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possible that your session expired?
Does the management return any values if you just do a "show objects"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I see a dump of database objects. However, if I grep for one of the usernames, I do not see it.
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have an answer concerning SecureKnowledge solution sk522
Your feedback was:
------------------
What about the R80.xx versions ?
------------------
This article is not relevant for R80.x
Thank you,
Stella Shteinbuk and the SecureKnowledge Team
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter