- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- Re: Leveraging the R80.10 API to Automate and Stre...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Leveraging the R80.10 API to Automate and Streamline Security Operations
On 15th August 2017 we did a webinar with Ryan Darst about the automation and orchestration capabilities you can achieve with the R80.10 API. Specifically, this session covered:
- Introduction to using the R80.10 APIs using a variety of tools from Postman to Ansible
- Tips on leveraging the API from both the R80.10 CLI and from the RESTful API to do simple tasks from adding objects and services to adding rules
- Additional use cases for using other features in the R80 API from policy verification to running scripts on gateways
- A demonstration of a complete Check Point cloud auto-scaling environment using Ansible and the R80.10 APIs
The content presented is below:
Slides: How to use R80.10 API for Automation and Streamlined Security (PPT)
Video: How to use R80.10 API for Automation and Streamlined Security (Video)
Scripts: CheckMates_Aug15_Demos.zip
Labels
- Labels:
-
Access Policy
-
General
-
Object Management
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It was really a great presentation and demo by Ryan Darst.
Question-1: Is this automation limited to cloud or can we create objects, rules etc in VSX environment?
Question-2: Any suggestions on integration with ticketing systems - to get the source, destination, ports and create objects and rules based on that information?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Automation can be done with on-premise gateways with VSX as well (though creation and some configuration of VS still requires a CLI command)
Integration with ticketing systems requires some business-specific logic.
I know (in general) we are working on specific integrations with some of these systems to assist with that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
q1 : You can use the API's put-file and run-script:
Check Point - Management API reference
put-file file-path "/home/admin/" file-name "vsx_conf" file-content "vs ip 192.0.2.1\nvs2 ip 192.0.2.2" targets.1 "corporate-gateway" --format json
Check Point - Management API referencerun-script script-name "Script Example: run /home/admin/vsx_conf" script "/home/admin/vsx_conf" targets.1 "corporate-gateway" --format json
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Webinar was absolutely fantastic!
We want to test automation in our company so I downloaded a trial R80.10 version. Seems like Management API is not available there (nothing in Manage & Settings). Is it available only in licensed versions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Management API Settings
- Startup Settings
- Select Automatic start to automatically start the API server when the Security Management Server starts.
In these environments, Automatic start is selected by default:
- Distributed Security Management Servers (without gateway functionality) with at least 4GB of RAM
- Standalone Security Management Servers (with gateway functionality) with at least 8GB of RAM
In other environments, to reduce the memory consumption on the management server, Automatic start is not selected by default.
- Select Automatic start to automatically start the API server when the Security Management Server starts.
- Access Settings
Configure IP addresses from which the API server accepts requests:
- Management server only (default) - API server will accept scripts and web service requests only from the Security Management Server. You must open a command line interface on the server and use the
mgmt_cliutility to send API requests. - All IP addresses that can be used for GUI clients - API server will accept scripts and web service requests from the same devices that are allowed access to the Security Management Server.
- All IP addresses - API server will accept scripts and web-service requests from any device.
- Management server only (default) - API server will accept scripts and web service requests only from the Security Management Server. You must open a command line interface on the server and use the
To apply changes, you must publish the session, and run the api restart command on the Security Management Server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The options mentioned by Ofir Sh can be found here in the SmartConsole:
MANAGE & SETTINGS > Blades > Management API > Advanced Settings...
I would also like to add that you can use the API over HTTPS also in the cloud demo. You have to: set an administrator's password, enable the API access, publish the session, copy the demo server's IP address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Guys, I know how to read documentation. I said I don't have such option on a trial license:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By trial license, do you mean the built-in 15-day one you get on install?
I know it works with ones generated from User Center.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even so I did a fresh install with R80.10, using the built-in license, and found the GUI option there.
Another way to enable the API is through the CLI, which I describe here: https://community.checkpoint.com/thread/1082
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
are you using MDM (MDS)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From your screenshot I see it's a Multi-Domain deployment and you have logged into one of your domain. API settings are managed in the MDS domain since it's one process for the server (since it has no inner state).
Please log into your MDS domain and set the settings.
Dameon Welch Abernathy Ofir Sh Václav Brožík I challenge u to spot my proof for that being a multi-domain screenshot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Challenge accepted ![]()
The key appears to be here:
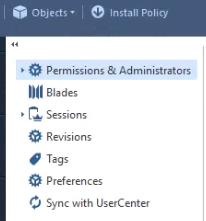
In an MDM (or at least the screenshot Stefan Stefanov), there is no Permissions & Administrators and Sync with UserCenter options.
The above screenshot is from my standalone (not MDM) manager.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I am using Terraform for infrastructure provisioning and Ansible for configuration in AWS to deploy checkpoint FIrewall R80, I am stuck on few points below,
1. How to add URL for Egress filtering. We need to policy through Ansible so that Internal subnet can access the Some URL on the Internet and rest should be blocked.
2. How to add gateways in the Management server.
3.How to enable other blades(IPS etc.) if required.
4. How to config for lag management, I am planning to send to Splunk server.
4. How we can define instance as the Management server. For Gateway I am using below in user data file.
my_user_data: |
#!/bin/bash
clish -c 'set user admin shell /bin/bash' -s
clish -c 'set static-route {{ aws_lb1_subnet_cidr }} nexthop gateway address {{ aws_internal_route }} on' -s
clish -c 'set static-route {{ aws_lb2_subnet_cidr }} nexthop gateway address {{ aws_internal_route }} on' -s
clish -c 'set static-route {{ aws_webserver_subnet_cidr }} nexthop gateway address {{ aws_internal_route }} on' -s
clish -c 'set static-route {{ aws_database_subnet_cidr }} nexthop gateway address {{ aws_internal_route }} on' -s
config_system -s 'install_security_gw=true&install_ppak=true&gateway_cluster_member=false&install_security_managment=false&ftw_sic_key=vpn12345';shutdown -r now;
Any help would be highly appreciable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Questions 1-3 can be answered by reading the API documentation: Tip of the Day: Local R80.x API Documentation
I would search for and ask the specific API questions as seperate thread(s) here: Developers (Code Hub)
Question 4 should be solved with Log Exporter, see: Log Exporter guide and Log Exporter - Splunk Integration Update
Question 5, you need to (at a minimum) modify the config_system line, see: How to run the First Time Configuration Wizard through CLI in Gaia R76 and above
You probably need to do other things as well and it might be worth reviewing the CloudFormation script for installing Management in AWS.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


