- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
Mastering Compliance
Unveiling the power of Compliance Blade
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- Automate deployment of Indicators of Compromise (I...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Automate deployment of Indicators of Compromise (IOC) with a new API.
The R80.20.M1 - Management Feature Release gives new API for something that previously we could only do from the SmartConsole GUI - deployment of IOC's.
IOC's (Indicators of Compromise) are sources which are known as malicious.
Steps to deploy IOC's with the Management API:
1. Login to the Management Server with the login command. The response contains a session ID. Use it for the next steps.
2. Add, edit or delete indicators. The session ID is a required parameter in the "sid" header.
3. Publish your changes with the publish command.
4. Install the Threat Prevention Policy on the gateways in which you would like to enforce this change, using the install-policy command. Remember, installing just the threat prevention part of the policy separates you from the network objects and access control changes that may have happened at the security management server.
Examples of indicator command executions:
Option A: define the indicators as part of the parameters:
mgmt_cli add threat-indicator name "My_Indicator" observables.1.name "My_Observable" observables.1.mail-to "someone@somewhere.com" observables.1.confidence "medium" observables.1.severity "low" observables.1.product "AV" action "ask" profile-overrides.1.profile "My_Profile" profile-overrides.1.action "detect"
Option B: place an indicators file - in CSV or STIX format - and import its raw data:
mgmt_cli add threat-indicator name "My_Indicator" observables-raw-data ""
Option C: edit the indicator action for a given threat profile. A threat profile is connected to some scope behind a gateway in the threat prevention policy.
mgmt_cli set threat-indicator name "My_Indicator" action "prevent" profile-overrides.remove "My_Profile"
Option 😧 show all indicators or one of the indicators:
mgmt_cli show threat-indicators
mgmt_cli show threat-indicator name "My_Indicator"
Option E: delete some indicators:
mgmt_cli delete threat-indicator name "My_Indicator"
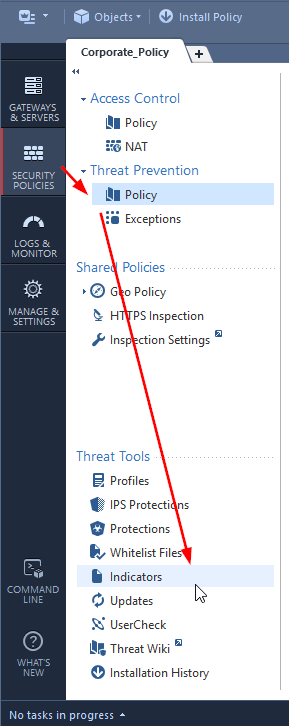
To get to it in SmartConsole:
1. Open Security Policies
2. Navigate to Threat Prevention-->Policy
3. The bottom part changes to "Threat Tools". Click on "Indicators".
Let us know your feedback on this.
Labels
- Labels:
-
Threat Prevention Policy
1 Solution
Accepted Solutions
DeletedUser
Not applicable
2020-01-24
01:59 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Once you set up the gateway IoC feed, the updates are "automatic", but yes if you're adding indicators via the management API, then you have to build it using a tool. Which tool do you have in mind? You can use Check Point Ansible modules or Terraform Check Point Provider.
18 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Following up Tomer's post, this post may be usefull as well -
https://community.checkpoint.com/docs/DOC-3012
Robert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it is good to know that there is a CSV support ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's very useful and important to leverage 3rd party resource integrated with threat prevention policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This API can provide import CSV file from FTP or HTTP server ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are 3 ways to import CSV's:
1. download the files, parse them and send as JSON
2. place on the Management Server and send the path
3. download the files, reorder the CSV columns to have exactly this order: Name, Value, Type, Confidence, Severity, Product, Comments, and then use the "observables-raw-data" parameter to send each row, for example:
observables-raw-data "my_observable_1,someone@somewhere.com,mail-to,medium,low,AB,my comment"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tomer,
For the CSV, does it support using web API to insert multiple parameters (observables) in single threat indicator name in single api command?
When i tried it will show that the name already exist (as name is required parameter) but the command only allow to put single observables-raw-data
So the idea is something like this:
{
"name" : "Test",
"observables-raw-data" : "my_observable_1,someone@somewhere.com,mail-to,medium,low,AB,my comment",
"my_observable_2,someone@somewhere.com,mail-to,medium,low,AB,my comment",
"my_observable_3,someone@somewhere.com,mail-to,medium,low,AB,my comment",
"action" : "ask",
"profile-overrides" : [ {
"profile" : "Test",
"action" : "detect"
} ],
"ignore-warnings" : true
}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Doesn't seem to be a usable method for more than a few indicators. I tried to import a CSV file with 500 lines (all type IP). Progress showed 20% for over 40 minutes so I finally aborted. I tried again with just 10 lines to verify my format was good. On R77.30 I run a daily import of 9 CSV files totaling about 7000 lines; takes just a couple minutes using the load_indicators command. Unfortunately I cannot use load_indicators on R80.20M1 because of an apparent bug (doesn't like IPs that have a zero in one of the IPv4 octets).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It shouldn't take this long. Please open a support ticket.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tomer Sole I followed your instructions and could import the CSV files just fine to the management...
BUT, when I want to look at them on the SmartConsole, the Windows process spikes to 20% cpu usage (for at least 10 minutes) and the application freezes. I'd to kill the process in order to login again and it only happens when I go to "Threat Tools" and then click on "Indicators".
If it's useful I imported 7 CSV files with a lot of records, if you need it I could count how much rows has them.
From where can I start debugging the issue?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How many lines in the CSV file?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dameon, the total lines of all of the CSV files are 76238. The most lengthy file has 60774 lines, and other one has 11567
The rest of it doesn't have more than 1k lines.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm guessing that 76k line file is causing an issue.
Generally speaking, if you've got that many IOCs, it might be better to employ a Private ThreatCloud appliance.
In that case, you upload the IOCs to your PTC appliance and all your gateways consult it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, In the case of using PTC appliance, gateways enforce policy immediately or policy installation is needed?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is great stuff. Is there a plan to do more of a real time update? This would be something like as soon as a publish occurs, the IOC would propagate to the gateway automatically? Thinking along the lines of IPS where you can set a policy (which requires a threat prevention policy install) and IPS sigs would automatically get enabled on the gateway based on the policy, it would be nice for a way to add some IOCs and the gateways pick it up near real-time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check out How to extend and enhance SmartConsole? to integrate web pages inside SmartConsole
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How is this automated? It is a great feature, but these instructions are all done manually. I'd like a way to feed IOCs via API with an automation tool.
DeletedUser
Not applicable
2020-01-24
01:59 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Once you set up the gateway IoC feed, the updates are "automatic", but yes if you're adding indicators via the management API, then you have to build it using a tool. Which tool do you have in mind? You can use Check Point Ansible modules or Terraform Check Point Provider.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 25 Apr 2024 @ 11:00 AM (CEST)
CheckMates in Russian - Возможности и риски искусственного интеллектаThu 25 Apr 2024 @ 11:00 AM (CEST)
CheckMates in Russian - Возможности и риски искусственного интеллектаThu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center


