I am on a verge of loosing my cool after spending half a day on a seemingly trivial task of trying to create an exception for the Threat Prevention policy.
The goal is to allow my client's PCs to receive the Phishing training communication from the KnowBe4.
The vendor has three IPs but each campaign generates new resources.
Every time client tries to go to the spoofed site, i.e. "gmail.net-login.com", the gateway promptly bags it with:
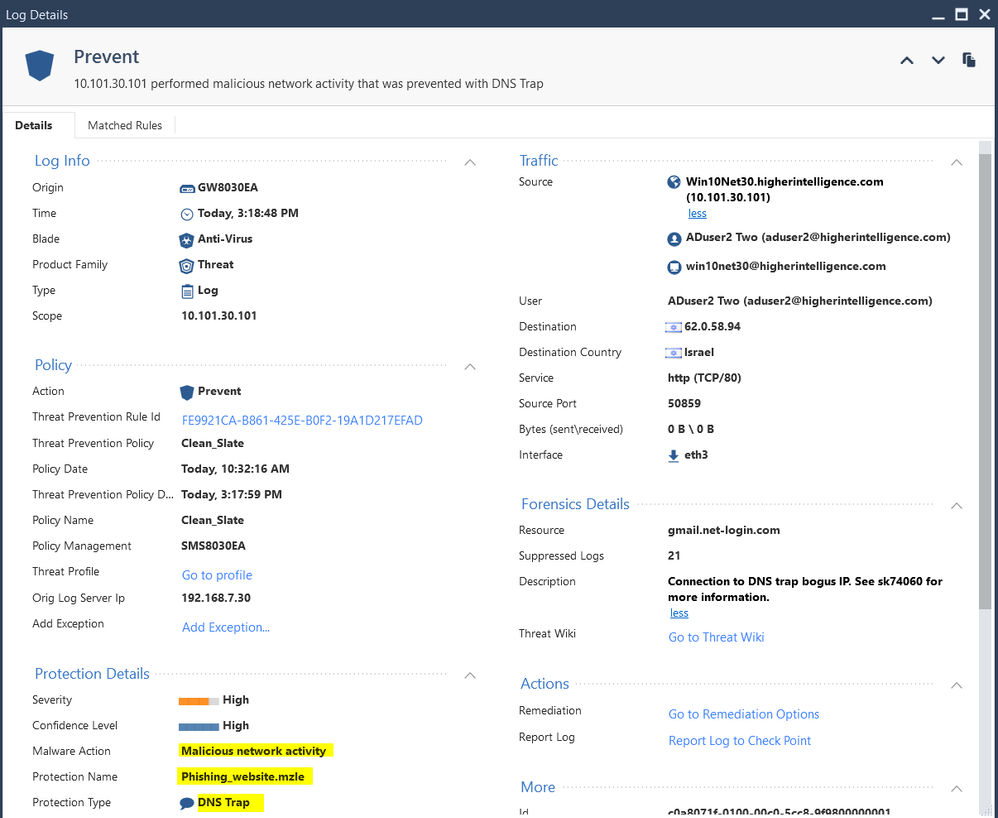
Time: 2019-04-30T19:18:48Z
Interface Direction: inbound
Interface Name: eth3
Id: c0a8071f-0100-00c0-5cc8-9f9800000001
Sequencenum: 1
Threat Prevention Policy: Clean_Slate
Threat Prevention Policy Date:2019-04-30T19:17:59Z
Source: 10.101.30.101
Source Port: 50859
Destination Country: Israel
Destination: 62.0.58.94
Destination Port: 80
IP Protocol: 6
Session Identification Number:0x5cc89f98,0x1,0x1f07a8c0,0xc0000001
Protection Name: Phishing_website.mzle
Description: Connection to DNS trap bogus IP. See sk74060 for more information.
Confidence Level: High
Severity: High
Malware Action: Malicious network activity
Protection Type: DNS Trap
Threat Prevention Rule Id: FE9921CA-B861-425E-B0F2-19A1D217EFAD
Protection ID: 0018B6567
Log ID: 2
Scope: 10.101.30.101
Source User Name: ADuser2 Two (aduser2@higherintelligence.com)
Source Machine Name: win10net30@higherintelligence.com
User: ADuser2 Two (aduser2@higherintelligence.com)
Action: Prevent
Type: Log
Policy Name: Clean_Slate
Policy Management: SMS8030EA
Db Tag: {BAC69145-F44A-4148-9603-7CEBB47B7A42}
Policy Date: 2019-04-30T14:32:16Z
Blade: Anti-Virus
Origin: GW8030EA
Service: TCP/80
Product Family: Threat
Resource: gmail.net-login.com
Marker: @A@@B@1556596801@C@31302
Log Server Origin: 192.168.7.30
Orig Log Server Ip: 192.168.7.30
Index Time: 2019-04-30T19:19:54Z
Lastupdatetime: 1556651989000
Lastupdateseqnum: 1
Rounded Sent Bytes: 0
Rounded Bytes: 0
Stored: true
Rounded Received Bytes: 0
Suppressed Logs: 21
Sent Bytes: 0
Received Bytes: 0
Interface: eth3
Description: 10.101.30.101 performed malicious network activity that was prevented with DNS Trap
Threat Profile: Go to profile
Bytes (sent\received): 0 B \ 0 B
Trying to exempt the traffic by negating the destination group in the TP rules, creating manual exemptions with either "Detect" or "Inactive", doing same by creating the exemptions from the logs, does not change the behavior. DNS trap is activated every time.
Searching for the Protection Name: "Phishing_website.mzle" in either "Protections" or IPS Protections, does not help. The thing is not there.
Even creating a Categorization Exception:
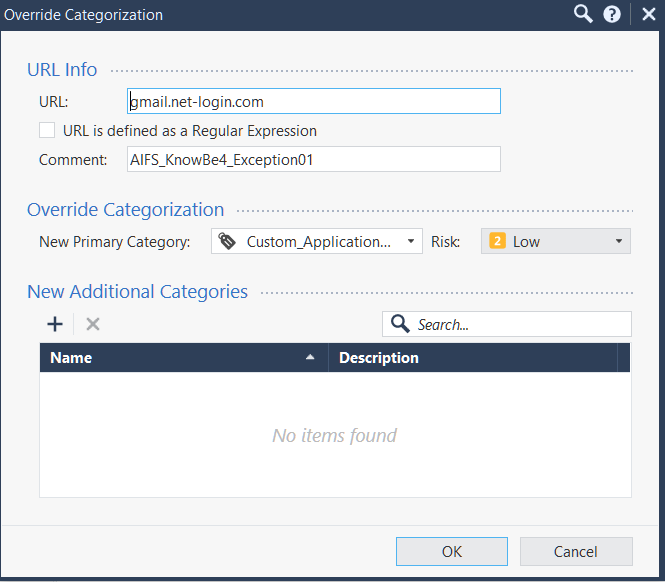
As unfeasible as it is for this particular task, still does not work.
HELP!!!




