Hi,
We are having an issue with DLPUD process which is pending for weeks (TAC involved)
We found that some CAB files from Microsoft & Office update are passing through the Threat Prevention Layer and some AV action are done on the file. Files are written to the disk for inspection.
This process is causing high Disk utilization and increase CPU on our Gateways
Here is an example of log from dlpud.elg
[28962][3 Mar 10:01:20] Start [1A] umsess=0x8ecb9a0 (x.x.x.x:52535 -> 87.248.222.128:80) initiator=0x8 partial=1(4194304-5242879/68673795) strict_hold_skip_active=0 orig_file=windows10.0-kb5010472-x64-ndp48_07d328da3e495d688287607c0c4748cb4a327b90.cab tmp_file=/opt/CPsuite-R81.10/fw1/tmp/dlp/{E645F264-B9F1-3ECE-F3F6-D2A5A6C2C855} file_unique_id=
This directeory is full of file that are sometimes not cleaned du to a DLPUD crashed - /opt/CPsuite-R81.10/fw1/tmp/dlp/
This lead to full disk utilization are require at the moment manual cleanup...
If we look at the Firewall logs based on filename windows10.0-kb5010472-x64-ndp48_07d328da3e495d688287607c0c4748cb4a327b90.cab. We can see that:
Time: 2022-03-03T09:01:12Z
Interface Direction: outbound
Connection Direction: Outgoing
Id: c0a80101-6a65-0000-6220-83d80000001c
Sequencenum: 46
Hll Key: 13342166036668581550
Duration: 60
Last Update Time: 2022-03-03T09:01:16Z
Update Count: 2
Creation Time: 2022-03-03T09:01:12Z
Connections: 2
Aggregated Log Count: 2
Source Country: United States
Source: x.x.x.x
Destination Country: Unknown Location in Europe/SW Asia
Destination: 87.248.222.128
Destination Port: 80
IP Protocol: 6
Client Type: Other: Microsoft-Delivery-Optimization/10.0
User Agent: Microsoft-Delivery-Optimization/10.0
Protocol: HTTP
Sig Id: 0
Service ID: http
Application ID: 10074906
Application Signature ID:10074906:3
Method: GET
Action: Accept
Type: Session
Db Tag: {23137267-A306-D44E-8AA2-D0EF42FA9BA1}
Policy Date: 2022-02-25T10:21:19Z
Blade: Application Control
Service: TCP/80
Product Family: Access
Logid: 288
Application Name: Windows Update
Application Description: Windows Update is a Microsoft tool that enables users to setup automatic updates for their products.
Primary Category: Software Update
Matched Category: Software Update
Additional Categories: Very Low Risk, Microsoft & Office365 Services, Software Update, Web Services Provider
Application Risk: Very Low
Resource: http://au.download.windowsupdate.com/d/msdownload/update/software/updt/2022/01/windows10.0-kb5010472...
Access Rule Name: App_Updates
Access Rule Number: 242.11
Policy Rule UID: 79aa6811-dc90-4e5b-b300-6c4c0b0d62bf
Marker: @A@@B@1646289832@C@4404630
Index Time: 2022-03-03T09:02:11Z
Lastupdatetime: 1646298132000
Lastupdateseqnum: 46
Severity: Informational
Confidence Level: N/A
Stored: true
URLs: 1
Layer Uuid Rule Uuid: ca2438ac-7706-4b85-ac70-eb7a63e55f34_3285e8df-63e0-48ca-94e6-d986b2c10da6, a6a6961d-6d63-4169-9d12-7e0eca58f093_79aa6811-dc90-4e5b-b300-6c4c0b0d62bf
From what we know there is 2 options to do a correct bypass in Threat Prevention (Updatable Objects or Custom App with URL). Unfortunately there is no object for Windows Update / Office in Updatable objects (that would be very helpfull...)
We then implemented URL Regex exceptions that should match or URL
^windowsupdate\.com
\/windowsupdate\.com
\.windowsupdate\.com
However files are still inspected by TP and cause our daily crashes
Any recommandation to bypass Windows Update & Office update from TP are welcomed 🙂 Please note it's HTTP and not HTTPS traffic so no option to do a more global bypass with HTTPS...
I guess we are not the only one in this situation. Gateways are in R81.10
Last option is to bypass CAB from TP profile but as we don't want to cause more issue than we have today we need to stick the custom profile with default options but there is no doc about this
- It’s now defined as « Process files types known to contain malware
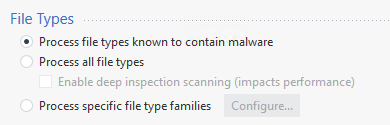
- We can migrate to « Process specific file type families but we first need to configure this settings with similar option that applied at the moment – Please provide the match between both settings
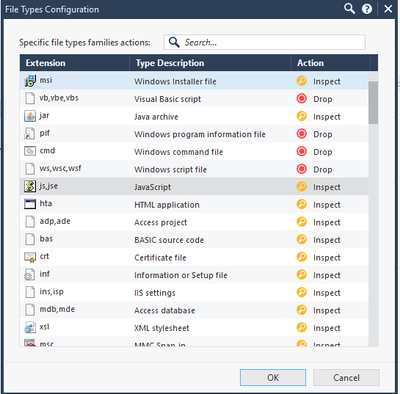
Thank you




