- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
Mastering Compliance
Unveiling the power of Compliance Blade
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Management
- :
- Re: problem with proxy arp
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
problem with proxy arp
I need to perform a simple operation to publish the server to the Internet.
For this:
1. I create a manual static nat
2. Add the address in the proxy arp via WEB-UI (85.21.100.105 - Public server IP)
3. I turn on the global settings option "Merge manual proxy ARP configuration"
4. install policy.
But unfortunately, the firewall does not respond to arp requests for the published server
What did not I finish?
FW-r80.10, MNG-r80.10
show arp proxy all
IP Address MAC Address / Interface Real IP Address
85.21.100.105 eth8 85.21.100.111
85.21.100.111 - ext ip
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You may not have the ClusterXL box checked on the firewall object in the SmartConsole, but I can pretty much guarantee that clustering is enabled in cpconfig which is the problem.
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What does the output of "fw ctl arp" show from expert mode?
What is the subnet mask of 85.21.100.X? Are you SURE that 85.21.100.105 and 85.21.100.111 exist in the same subnet? Proxy ARP will only be performed by the firewall for NAT addresses plucked from what it thinks is a directly-attached IP range.
Is a firewall cluster involved?
Also make sure it is a *proxy* ARP you added via the Gaia web interface, not a *static* ARP.
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
[]# fw ctl arp
(85.21.100.105) at 00-1c-7f-83-b7-7f interface 85.21.100.111
Yes this one subnet
This is not a cluster
This is not statics ARP, you can see from the output of commands
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you run "tcpdump -eni eth8 arp" from expert mode, are you seeing an inbound ARP request for 85.21.100.105 from your perimeter router?
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are queries, no answers
17:12:15.468575 6c:c2:17:78:7c:2a > Broadcast, ethertype ARP (0x0806), length 60: arp who-has 85.21.100.105 tell 85.21.100.112 - my test PC
17:12:16.384090 d4:6d:50:6b:c5:61 > Broadcast, ethertype ARP (0x0806), length 60: arp who-has 85.21.100.105 tell 85.21.100.97
17:12:16.468832 6c:c2:17:78:7c:2a > Broadcast, ethertype ARP (0x0806), length 60: arp who-has 85.21.100.105 tell 85.21.100.112
17:12:24.468699 6c:c2:17:78:7c:2a > Broadcast, ethertype ARP (0x0806), length 60: arp who-has 85.21.100.105 tell 85.21.100.112
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
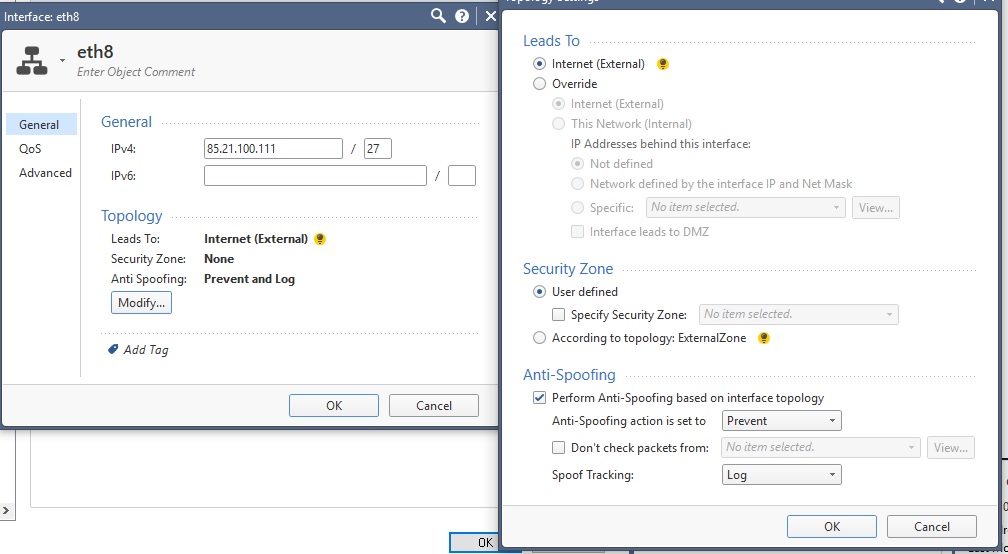
I'm suspecting that the firewall object topology definition for eth8 does not match the underlying Gaia interface configuration. Please provide a screenshot of eth8's topology in the SmartConsole, and the output from following expert mode commands:
ifconfig eth8
fw stat
arp -an | grep 85.21.100.
netstat -rn | grep 85.21.100.
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ifconfig eth8
eth8 Link encap:Ethernet HWaddr 00:1C:7F:83:B7:7F
inet addr:85.21.100.111 Bcast:85.21.100.127 Mask:255.255.255.224
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:60326 errors:0 dropped:0 overruns:0 frame:0
TX packets:42250 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:34872545 (33.2 MiB) TX bytes:10041607 (9.5 MiB)
fw stat
HOST POLICY DATE
localhost CO_test 9Oct2017 15:45:59 : [^eth1] [^eth1] [^eth8] [^eth8]
arp -an ^ grep 85.21.100.
? (85.21.100.97) at D4:6D:50:6B:C5:61 [ether] on eth8
netstat -rn ^ grep 85.21.100.
85.21.100.96 0.0.0.0 255.255.255.224 U 0 0 0 eth8
0.0.0.0 85.21.100.97 0.0.0.0 UGD 0 0 0 eth8
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well everything looks correct here, has anything in the config of the underlying Gaia eth8 interface been changed on the fly at all since the last boot? Try tcpdump again, but this time with the -p option to suppress promiscuous mode as shown below, do you still see the ARP requests for 85.21.100.105 coming in:
tcpdump -p -eni eth8 arp
If you don't seem them coming in any more it is a network problem. If you do still see them coming in, try running
fw ctl zdebug drop
Is it logging any kind of drop or other difficulty handling ARP in the zdebug?
Next try reinstalling policy, then try this next from expert mode:
ifdown eth8;ifup eth8
If that still doesn't work only thing I can suggest at this point is a reboot, lame as that sounds.
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very interesting, this firewall is not a cluster
;[cpu_1];[fw4_0];fw_log_drop_ex: Packet proto=-1 ?:0 -> ?:0 dropped by fwha_process_incoming_arp Reason: The packet is designated to an ip address that is proxied, but I'm not an active member
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You may not have the ClusterXL box checked on the firewall object in the SmartConsole, but I can pretty much guarantee that clustering is enabled in cpconfig which is the problem.
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you were right! I disabled clustering - the proxy arp earned. It's great, thanks a lot, excellent troubleshooting!!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Glad to hear, as it turns out there is actually a SK documenting this that I'll link here for future reference:
sk34453: Automatic Static NAT does not work on Security Gateway
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello All,
Andrey, try move your NAT rules above implied rules.
regards,
--
ak.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
These are the highest rules, there is nowhere to go ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can configure the below configuration on the CLI of each cluster member.
- Modify the $CPDIR/tmp/.CPprofile.sh script:
- Back up the current $CPDIR/tmp/.CPprofile.sh script:
[Expert@HostName:0]# cp -v $CPDIR/tmp/.CPprofile.sh $CPDIR/tmp/.CPprofile.sh_ORIGINAL
- Edit the current $CPDIR/tmp/.CPprofile.sh script:
[Expert@HostName:0]# vi $CPDIR/tmp/.CPprofile.sh
- Before the last line, add:
_cpprof_add CP_AUTO_ARP_FOR_MANUAL_NAT_RULES "1" 0 0
- Save the changes and exit the Vi editor.
- Modify the $CPDIR/tmp/.CPprofile.csh script:
- Back up the current $CPDIR/tmp/.CPprofile.csh script:
[Expert@HostName:0]# cp -v $CPDIR/tmp/.CPprofile.csh $CPDIR/tmp/.CPprofile.csh_ORIGINAL
- Edit the current $CPDIR/tmp/.CPprofile.csh script:
[Expert@HostName:0]# vi $CPDIR/tmp/.CPprofile.csh
- Before the last line, add:
setenv CP_AUTO_ARP_FOR_MANUAL_NAT_RULES "1"
- Save the changes and exit from Vi editor.
- Reboot the Security Gateway.
- Verify that the relevant environment variable was set:
- In the Bash shell:
- Log into the Expert mode.
- Check the value of the variable:
[Expert@HostName:0]# echo $CP_AUTO_ARP_FOR_MANUAL_NAT_RULES
Output should show a value of 1.
- In the Csh shell:
- Log into the Expert mode.
- Log into the Csh shell:
[Expert@HostName:0]# csh
- Check the value of the variable:
[admin@HostName ~]# echo $CP_AUTO_ARP_FOR_MANUAL_NAT_RULES
Output should show a value of 1.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 6 | |
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 |
Upcoming Events
Thu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center


