- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Mastering Compliance
Unveiling the power of Compliance Blade
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
May the 4th (+4)
Navigating Paradigm Shifts in Cyber
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
Introducing Quantum Force
Accelerated AI-Powered Firewalls
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Management
- :
- Re: R77.30 First Time Wizard stuck after definitio...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R77.30 First Time Wizard stuck after definition of Management Connection.
Has anyone encountered this before: during FTW, after management interface is defined with the same IP as the WebUI is using, the buttons are grayed-out and the process cannot progress further:
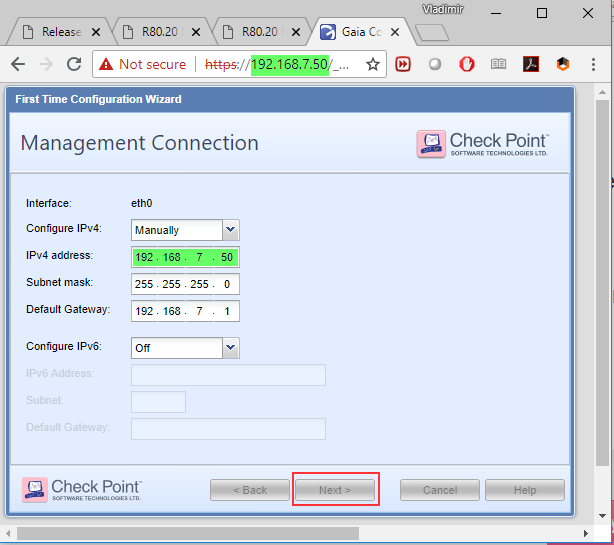
The image is Check_Point_R77.30_Install_and_Upgrade_T5.Gaia.iso and I have tried it with multiple browsers (Chrome required a one-liner to work, but IE was working from the start).
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Gateway or Management?
If management, it might be this: Cannot Connect with SmartConsole to R77.30 or Earlier Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It was not yet defined: I am in the process of running FTW and did not get to specify what it'll be yet.
The sequence goes:
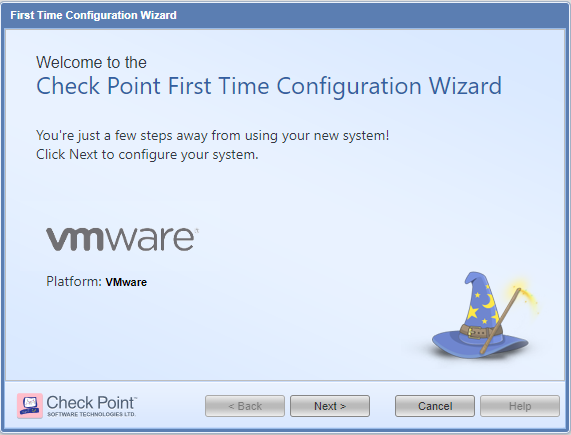
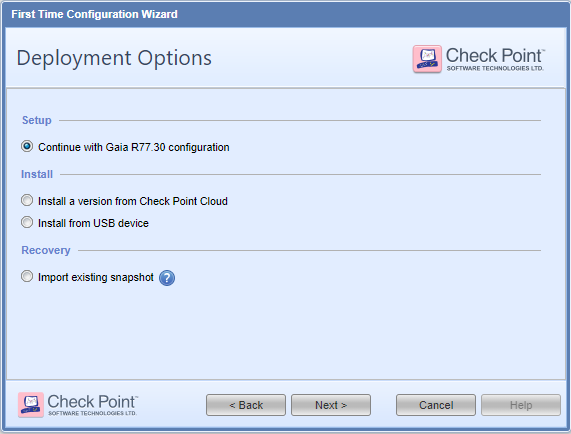

...and we're stuck.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You most probably tried it, but have you got the smae result after page refresh or clear cache and page refresh?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tried emptying the cache, refresh, different browsers and rebooted the VM.
Same results. Cannot exclude possibility of corrupted installation, unless there is some other gremlin at work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if you make changes to the interface page, what interface are you connected to when you start the FTW?
As you are stating that "after management interface is defined with the same IP as the WebUI is using"
To that rings a bell that says you were connected to another interface? You normally do not change the interface you are connected to during the running of the FTW.
You set the interface upfront through CLI if you want and then connect to that interface and run the FTW.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nope: same interface. That’s what’s puzzling. Nothing changes, simply clicking through the FTW stop responding after this page.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you backdate the system as indicated just to makes sure the Certificate issue is not bothering you here?
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hugo,
Haven't tried the backdating yet, as the epoch issue manifests itself later in the process, when we try to connect to the management via SmartDashboard.
I am curious to know if the Check_Point_R77.30_Install_and_Upgrade_T5 already contains the fixes from JHF 143 that addressing it.
As I am going through the FTW, the self-signed cert is a valid one:
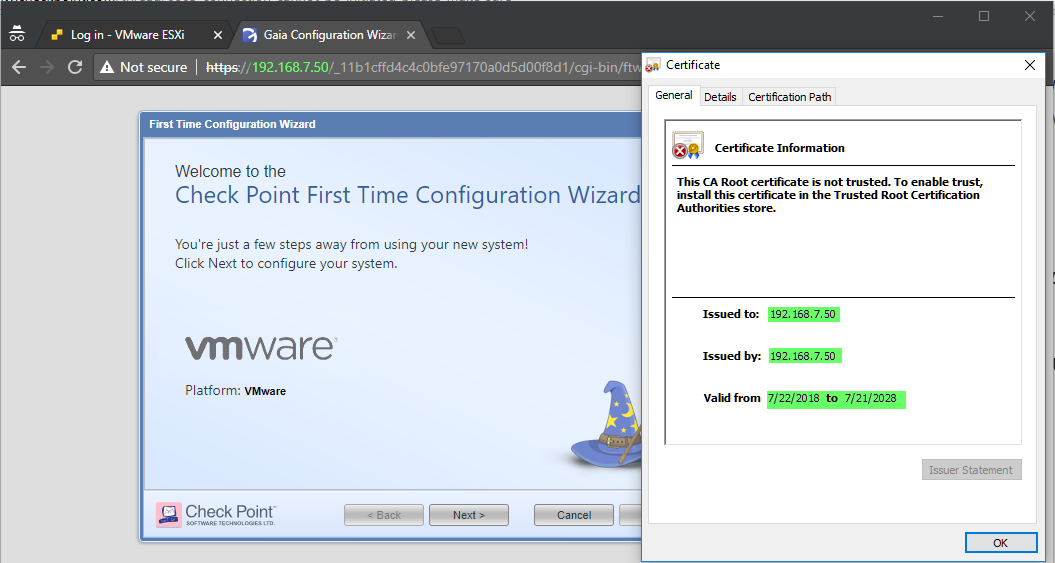
And since I have not yet defined this system as a management server, (planing to do that later in the setup), the internal CA is not yet in play.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've reinstalled the VM and the issue is no longer present. Must've been a corrupt installation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good to hear it doesn't repeat after reinstall. I was thinking about corrupted installation package at all. If are checksums ok.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had similar issue, finally sorted by recreating VM with the spec mentioned below. Main reason for this issue I found was due to ram and hard disk allocation on VM. Once I allocated 25gb hard disk space and 1.6 gb of ram the issue was fixed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Raaj. I'll keep it in mind, but I typically provision HDD space, RAM and CPU fairly generously for VMs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pretty sure even 25gb of disk and 1.6gb of RAM are below the minimum requirements for R77.x.
At the very least you should allocate the amounts specified in the release notes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The OVF for R77.30 is packed with a 10GB disc. you cannot really run standalone on it with more than 1 GB of log data. Upgrade is impossible and even running a jumbo can be challenging.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maarten,
The OVF is explicitly provisioned for Gateways.
The management VM was always supposed to be deployed from ISO.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 8 | |
| 6 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Wed 17 Apr 2024 @ 05:00 PM (CEST)
Mastering Compliance: Unveiling the power of Check Point Compliance BladeThu 18 Apr 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Sicherheit auf neuem Niveau: Risikoanalyse und SchutzstrategienThu 18 Apr 2024 @ 11:00 AM (CDT)
Central US: Network Security Troubleshooting - Part 3 - ClusterXLWed 17 Apr 2024 @ 05:00 PM (CEST)
Mastering Compliance: Unveiling the power of Check Point Compliance BladeThu 18 Apr 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Sicherheit auf neuem Niveau: Risikoanalyse und SchutzstrategienThu 18 Apr 2024 @ 11:00 AM (CDT)
Central US: Network Security Troubleshooting - Part 3 - ClusterXLAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center


