- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Mastering Compliance
Unveiling the power of Compliance Blade
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
May the 4th (+4)
Navigating Paradigm Shifts in Cyber
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Re: R80.x Ports Used for Communication by Various ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
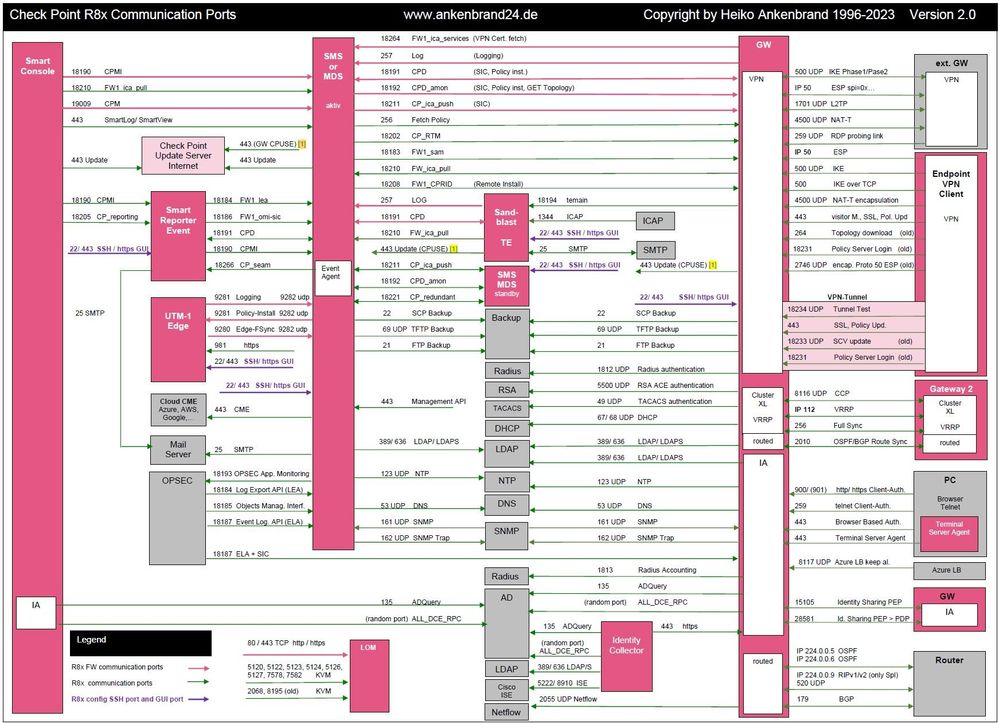
R8x Ports Used for Communication by Various Check Point Modules (new version 2.0)
| Introduction |
|---|
This drawing should give you an overview of the used R80, R81 ports respectively communication flows. It should give you an overview of how different Check Point modules communicate with each other. Furthermore, services that are used for firewall operation are also considered. These firewall services are also partially mapped as implied rules in the set on the firewall.
| Overview |
|---|
| Download PDF |
|---|
Download R8x version 2.0:
R8x Ports Used for Communication PDF
| SmartConsole Extention |
|---|
New!
Now I have developed a SmartConsole Extension so that you can view the overview directly in the SmartConsole.
In the Access Policy section in the upper area, there is a tab called "Ports for Modules". More infos here.
Extension URL: https://www.ankenbrand24.de/ex/ports.json
| References |
|---|
Support Center: Ports used by Check Point software
| Versions |
|---|
Version 2.0:
+ v2.0f new! now with SmartConsole Extension 02/13/2023
+ v2.0e add LOM port 2048 01/31/2023
+ v2.0d add LOM ports 01/23/2023
+ v2.0c new colors + design 01/22/2023
+ v2.0b best mistake 🙂 SmartDashboard versus SmartConsole 01/22/2023
+ v2.0a correct names : SMS, MDS, SmartConsole, ... 01/21/2023
old Version 1.9:
+ v1.9a add port 443 cloud CME 19.03.2022
+ v1.9b fix port issue 442 cloud CME 22.03.2022
old Version 1.8:
+ v1.8a R81.10 EA update 04.05.2021
+ v1.8b add port 18264 30.05.2021
+ v1.8c R81.10 upgrade 28.07.2021
old Version 1.7:
+ v1.7a R81 EA update 17.07.2021
+ v1.7b bug fix 20.08.2021
+ v1.7c bug fix + new download link 25.06.2021
old Version 1.6:
+ v1.6a add Azure ports 05.05.2020
+ v1.6b add all cloud ports 15.06.2020
old Version 1.5:
+ v1.5a typos corrected 18.09.2019
+ v1.5b port update 26.01.2020
old version 1.4:
+ v1.4a bug fix, update port 1701 udp L2TP 09.04.2018
+ v1.4b bug fix 15.04.2018
+ v1.4c CPUSE update 17.04.2018
+ v1.4d legend fixed 17.04.2018
+ v1.4e add SmartLog and SmartView on port 443 20.04.2018
+ v1.4f bug fix 21.05.2018
+ v1.4g bug fix 25.05.2018
+ v1.4h add Backup ports 21, 22, 69 UDP and ClusterXL full sync port 256 30.05.2018
+ v1.4i add port 259 udp VPN link probeing 12.06.2018
+ v1.4j bug fix 17.06.2018
+ v1.4k add OSPF/BGP route Sync 25.06.2018
+ v1.4l bug fix routed 29.06.2018
+ v1.4m bug fix tcp/udp ports 03.07.2018
+ v1.4n add port 256 13.07.2018
+ v1.4o bug fix / add TE ports 27.11.2018
+ v1.4p bug fix routed port 2010 23.01.2019
+ v1.4q change to new forum format 16.03.2019
old version 1.3:
+ v1.3a new designe (blue, gray), bug fix, add netflow, new names 27.03.2018
+ v1.3b add routing ports, bug fix designe 28.03.2018
+ v1.3c bug fix, rename ports (old) 29.03.2018
+ v1.3d bug fix 30.03.2018
+ v1.3e fix issue L2TP UDP port 1701
old version 1.1:
+ v1.1a - added r80.xx ports 16.03.2018
+ v1.1b - bug in drawing fixed 17.03.2018
+ v1.1c - add RSA, TACACS, Radius 19.03.2018
+ v1.1d - add 900, 259 Client-auth - deleted od 4.0 ports 20.03.2018
+ v1.1e - add OPSEC -delete R55 ports 21.03.2018
+ v1.1f - bug fix 22.03.2018
+ v1.1g - bug fix - add mail smtp -add dhcp - add snmp 25.03.2018
➜ CCSM Elite, CCME, CCTE
- Tags:
- ad
- backup
- blades
- ccp
- clusterxl
- cmi
- communication
- dashboard
- dhcp
- dns
- dynamic routing
- edge
- endpoint vpn
- esp
- event agent
- ftp
- gateway
- ha_info
- http
- ia
- icap
- identity awareness
- identity collector
- ike
- implied rules
- infrastructure
- ise
- ldap
- log
- lom
- modules
- nat-t
- nat-tranversal
- netflow
- ntp
- opsec
- ospf
- performance
- ports
- r80
- r80.10
- r80.10 gateway
- r80.10 management
- r80.20
- R81
- r81.10
- radius
- rdp
- route
- routed
- router
- routing
- rsa
- sandblast
- secure client
- secure gateway
- security management
- smart event
- smart reporter
- smartdomain manager
- smtp
- snmp
- software blades
- tacacs
- threat prevnetion
- threatemulation
- used ports
- utm-1
- vpn
- vrrp
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No. Security Management Server also needs TCP8211 to connect to log server.
This is not explained in sk52421 but this is what I noticed it on my R80.10 management platform ![]() . If I remember, if TCP8211 if not open, then SmartLog (on the management server) cannot browse logs stored on the log server.
. If I remember, if TCP8211 if not open, then SmartLog (on the management server) cannot browse logs stored on the log server.
294 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great stuff!
Thank you for the diagram. It will be helpful.
Maybe you can complement with the connections that are used to update services or signatures, like IPS is the SmartDashboard that goes online if it's a manual update, the application control is the smart center, etc, etc.
Regards,
Ivo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great job:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nicely done!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think it's great.
Maybe you can get a bigger overview with more balades. I think that's very helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have released a new version 0.9 with the following features:
- VPN connections
- Secure Client
- Update server Check Point
- Sandblast Appliance
- DNS/NTP
Regards,
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have released a new version 0.9b with the following features:
- Identity Awareness
- Smart Reporter + Smart Event + Event Agent
- bug fixed
Regards,
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This overview has been missing for a long time.
Keep up the good work!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
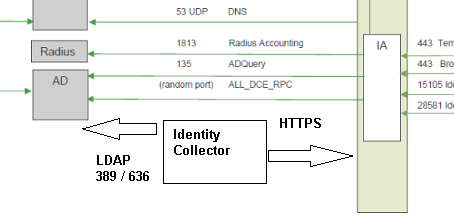
You may add Identity Collector in it ![]() sorry about the diagram "quality work"
sorry about the diagram "quality work"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I decided to rename the document.
Hope you don't mind ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Identity Collectors is completed!
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is ok!
![]()
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Awesome!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Thanks, usefull diagram for R77. Would be very interesting for R80.XX! ![]()
We tried to get such information from the Support for R80.10 after we found out that opening 19009 was mandatory between management servers and log servers (DBsync<->CPM).
As per our Diamond Engineer it seems that R&D think it's not necessary to add the information in sk52421... ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
THX for this info.
I checked this port 19009. See Wireshark:

I think this is the database query from the DashBoard to the Management Server.
Check Point KB SK says:
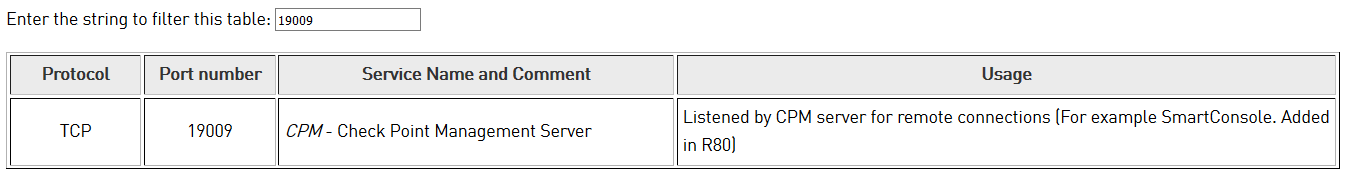
I will add the R80.xx ports in the next version.
Regards,
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Heiko, I know that SmartConsole R80.10 needs TCP19009 to connect to the management server, this is explained in the sk ![]()
But what the sk does not explains is that all management servers (including dedicated log servers) need to connect to each other using TCP19009. We noticed that when we noticed CPM packets dropped between our management servers (including dedicated log servers).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By the way thanks for the new diagram ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice R80 port update!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can add routing protokolls.
gateway <—-> bgp, ospf, rip,...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I add this in the next version. thx
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi heiko, such an overview, I have been looking for 10 years ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To be clear, we've had an SK with the this information for years.
Back in my books, I did have a diagram showing some of this.
This is definitely a more complete diagram.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think Dameon is right about his statement. This information has been available since version 4.0 FW-1 and I have been working with Check Point since version 3.
A very good overview of the ports can also be found in sk52421. This article is available since 12-Aug-2010 and longer. I have already seen this in version 4.0 at Check Point User Center.
Over the years I have also found many good diagrams in books.
Why do I make a diagram?
I think a picture says more than 1000 words!
Please help us with good ideas to expand the chart.
Thanks in advance.
Regards,
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A picture like this one is definitely saying much more than words ![]()
There is also TCP8211 between management servers and log servers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it me. Or am I missing RADIUS itself? And TACACS can also be used to authenticate.
Do you think you can squeze these into the drawing?
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thx
Port 8211 is from R80 Multi-Domain Security Management Server to the Log Server.
I have not yet drawn up any communication for multi-domain management, vsx and 41/61K SyncXL.
But I'll do that in another drawing.Unfortunately, no more objects fit on an A3 sheet. But it will come!
Regards,
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A picture like this one is definitely saying much more than words or port lists.![]()
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 13 | |
| 11 | |
| 8 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 05:00 PM (CEST)
SASE Masters: Deploying Harmony SASE for a 6,000-Strong Workforce in a Single WeekendAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center