Tip 1
SecureXL has been significantly revised in R80.20. It now works in user space. This has also led to some changes in "fw monitor".
Since R80.20 "fw monitor" is able to show the traffic accelerated with SecureXL. Thus it is possible to see SecureXL (provide more performance) modules in fw monitor chain. For more informations revert to "SecureXL offloading chain modules" in this article. Now you can see that SecureXL is used, which increases the performance of the firewall.
SecureXL "fwaccel off" does not have to be disabled on R80.20 to run "fw monitor". This is good for performance, so "fw monitor" does not affect performance any more.
# fwaccel off > no longer necessary in R80.20 and above
# fw monitor -e "accept(...);"
| R77.30 and R80.10 - fw monitor |
On R77.30 and R80.10 only disabling SecureXL allows to see the complete connection in fw monitor, which may be required for troubleshooting purposes or revert to "How to disable SecureXL for specific IP addresses".
# fwaccel off
# fw monitor -e "accept(...);"
More interesting articles:
- R80.x Architecture and Performance Tuning - Link Collection
- Article list (Heiko Ankenbrand)
| New fw monitor inspection points in R80.20 |
Tip 2
Furthermore there are new fw monitor inspection points available:
| Inspection point |
Name of fw monitor inspection point |
Relation to firewall VM |
Available since version |
| i |
Pre-Inbound |
Before the inbound FireWall VM (for example, eth1:i) |
always |
| I |
Post-Inbound |
After the inbound FireWall VM (for example, eth1:I) |
always |
| id |
Pre-Inbound VPN |
Inbound before decrypt (for example, eth1:id) |
R80.20 |
| iD |
Post-Inbound VPN |
Inbound after decrypt (for example, eth1:ID) |
R80.20 |
| iq |
Pre-Inbound QoS |
Inbound before QoS (for example, eth1:iq) |
R80.20 |
| iQ |
Post-Inbound QoS |
Inbound after QoS (for example, eth1:IQ) |
R80.20 |
| o |
Pre-Outbound |
Before the outbound FireWall VM (for example, eth1:o) |
always |
| O |
Post-Outbound |
After the outbound FireWall VM (for example, eth1:O) |
always |
|
e
oe
|
Pre-Outbound VPN* |
Outbound before encrypt (for example, eth1:e) in R80.10
(for example, eth1:oe) in R80.20
|
R80.10
R80.20
|
|
E
OE
|
Post-Outbound VPN* |
Outbound after encrypt (for example, eth1:E) in R80.10
(for example, eth1:OE) in R80.20
|
R80.10
R80.20
|
| oq |
Pre-Outbound QoS |
Outbound before QoS (for example, eth1:oq) |
R80.20 |
| oQ |
Post-Outbound QoS |
Outbound after QoS (for example, eth1:OQ) |
R80.20 |
* The fw monitor inspection point is different in R80.10 ("e" or "E") and R80.20 ("oe" and "OE")
For more information, see sk30583, fw monitor or How to use FW Monitor.
| SecureXL offloading chain modules |
Tip 3
Like I said SecureXL has been significantly revised in R80.20. It now works in user space. This has also led to some changes in "fw monitor"
There are new fw monitor chain (SecureXL) objects that do not run in the virtual machine.
# fw ctl chain 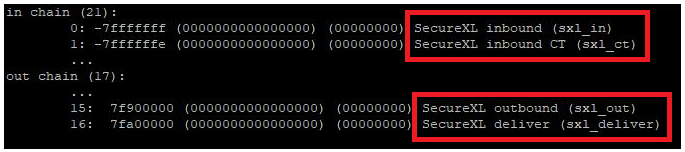
The new fw monitor chain modules (SecureXL) do not run in the virtual machine (vm).
SecureXL inbound (sxl_in) > Packet received in SecureXL from network
SecureXL inbound CT (sxl_ct) > Accelerated packets moved from inbound to outbound processing (post routing)
SecureXL outbound (sxl_out) > Accelerated packet starts outbound processing
SecureXL deliver (sxl_deliver) > SecureXL transmits accelerated packet
| New VM chain modules in R80.20 |
Tip 4
There are more new chain modules in R80.20
vpn before offload (vpn_in) > FW inbound preparing the tunnel for offloading the packet (along with the connection)
fw offload inbound (offload_in) > FW inbound that perform the offload
fw post VM inbound (post_vm) > Packet was not offloaded (slow path) - continue processing in FW inbound
# fw ctl chain 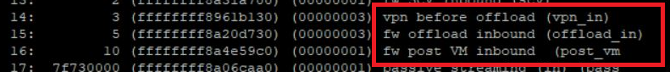
| New fw monitor chain key (00000000) |
Tip 5
In Firewall kernel (now also SecureXL), each kernel is associated with a key (red) witch specifies the type of traffic applicable to the chain modul.
# fw ctl chain 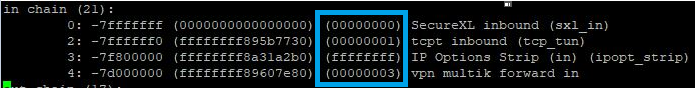
| Key |
Function |
| ffffffff |
IP Option Stip/Restore |
| 00000001 |
new processed flows |
| 00000002 |
wire mode |
| 00000003 |
will applied to all ciphered traffic (VPN) |
| 00000000 |
SecureXL offloading (new in R80.20+) |
R&D meeting Israel
➜ CCSM Elite, CCME, CCTE






