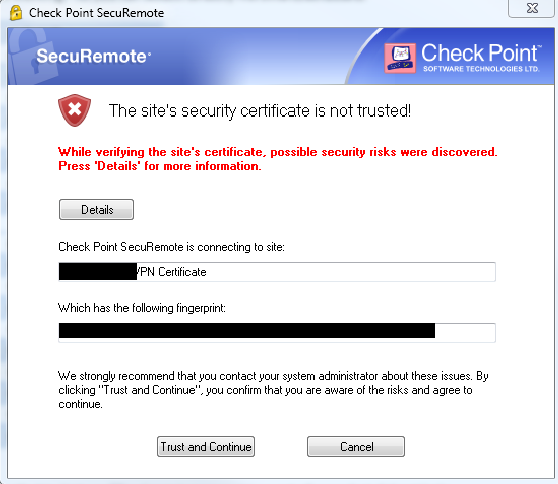
If you want to avoid seeing this alert, either distribute and install the self-signed certificate from your gateway or cluster to the users' PCs or define an A record in your external DNS for your gateway's public IP, buy the certificate issued by public CA and import it in your Gateway's or cluster's properties:
This is what I had to do, (the text between << and >> is my comments). The gw8010.mycompany.com<http://gw8010.mycompany.com> is my gateway, the “gw8010csrfile” and “gw8010privatekeyfile” and other references to particular file and certificate names, should be replaced with your own values:
<<
Original, from documentation: cpopenssl req -new -out <CSR file> -keyout <private key file> -config $CPDIR/conf/openssl.cnf
actual required: cpopenssl req -new -newkey rsa:2048 -out gw8010csrfile -keyout gw8010privatekeyfile -config $CPDIR/conf/openssl.cnf
>>
[Expert@GW8010:0]# cpopenssl req -new -newkey rsa:2048 -out gw8010csrfile -keyout gw8010privatekeyfile -config $CPDIR/conf/openssl.cnf Generating a 2048 bit RSA private key ......++++++++++++ .........++++++++++++ writing new private key to 'gw8010privatekeyfile'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:New Jersey Locality Name (eg, city) []:Wayne Organization Name (eg, company) [Internet Widgits Pty Ltd]:My Company Corp Organizational Unit Name (eg, section) []:IT Common Name (e.g. server FQDN or YOUR name) []:gw8010.mycompany.com<http://gw8010.mycompany.com>
Email Address []:myemail@mycompany.com<mailto:myemail@mycompany.com>
Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []:
An optional company name []:Higher Intelligence [Expert@GW8010:0]#
[Expert@GW8010:0]# ls
GW8010_config gw8010csrfile senderid_blue
expert gw8010privatekeyfile senderid_white
fw last_dump.log sessiond.elg
[Expert@GW8010:0]#
[Expert@GW8010:0]# chsh -s /bin/bash
Changing shell for admin.
Shell changed.
[Expert@GW8010:0]#
<<
Get the gw8010csrfile and gw8010privatekeyfile from the gateway to your PC using WinSCP Open gw8010csrfile in Notepad++ on windows or any editor on Mac and copy its content into clipboard In your CA's portal, paste the 2048 bit CSR into provided form and create a certificate Download the Certificate (works in TomCat format), with certificate chain included. It will typically be a .zip file containing .pem and two .crt files. The weirdly named file is, if you are using GoDaddy, the one assigned to your gateway/cluster.
cpopenssl pkcs12 -export -out <output file> -in <signed cert chain file> -inkey <private key file>
Example: cpopenssl pkcs12 -export -out gw8010.p12 -in e5472599cd25bd68.crt -inkey gw8010privatekeyfile
>>
[Expert@GW8010:0]# cpopenssl pkcs12 -export -out gw8010.p12 -in e5472599cd25bd68.crt -inkey gw8010privatekeyfile Enter pass phrase for gw8010privatekeyfile:
Enter Export Password:
Verifying - Enter Export Password:
[Expert@GW8010:0]# ls
GW8010_config gdig2.crt.pem gw8010privatekeyfile.old
e5472599cd25bd68.crt gw8010.p12 last_dump.log
expert gw8010csrfile senderid_blue
fw gw8010csrfile.old senderid_white
gd_bundle-g2-g1.crt gw8010privatekeyfile sessiond.elg
[Expert@GW8010:0]#
<<
Copy gw8010.p12 back to your PC using WinSCP
Create Alias for your gateway/cluster to include its FQDN (in this case gw8010.mycompany.com<http://gw8010.mycompany.com>)
Import gw8010.p12 certificate in these sections of your gateway's or cluster's properties:
Mobile Access > Portal Settings
Platform Portal
Data Loss Prevention
Identity Awareness > Captive Portal > Settings > Access Settings In the Certificate section, click Import or Replace.
>>