- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
Mastering Compliance
Unveiling the power of Compliance Blade
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Management
- :
- Re: Packet Mode, a new way of searching through yo...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Packet Mode, a new way of searching through your security policy in R80.10
R80.10 introduces a new feature called Packet Mode. This is a search mode that searches through a security policy as if a packet is traveling through it. Take a look at this video and see how this can help you in your daily tasks working with R80.10.
Let us know what other topics you would like to see addressed.
23 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Awesome video!! thx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Didn't know about this. Thanks for sharing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do you export the access-rules after filtering with packet mode ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
API tools should assist for this. use the "filter" and "filter-settings" parameters to perform packet mode search. then export the results to desired files.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you please help me where exactly filter option exist in API tools, i searched through it, but I could not found it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
the following reference page should show you the command "show access-rulebase": Check Point - Management API reference
it demonstrates running it with packet mode filter:
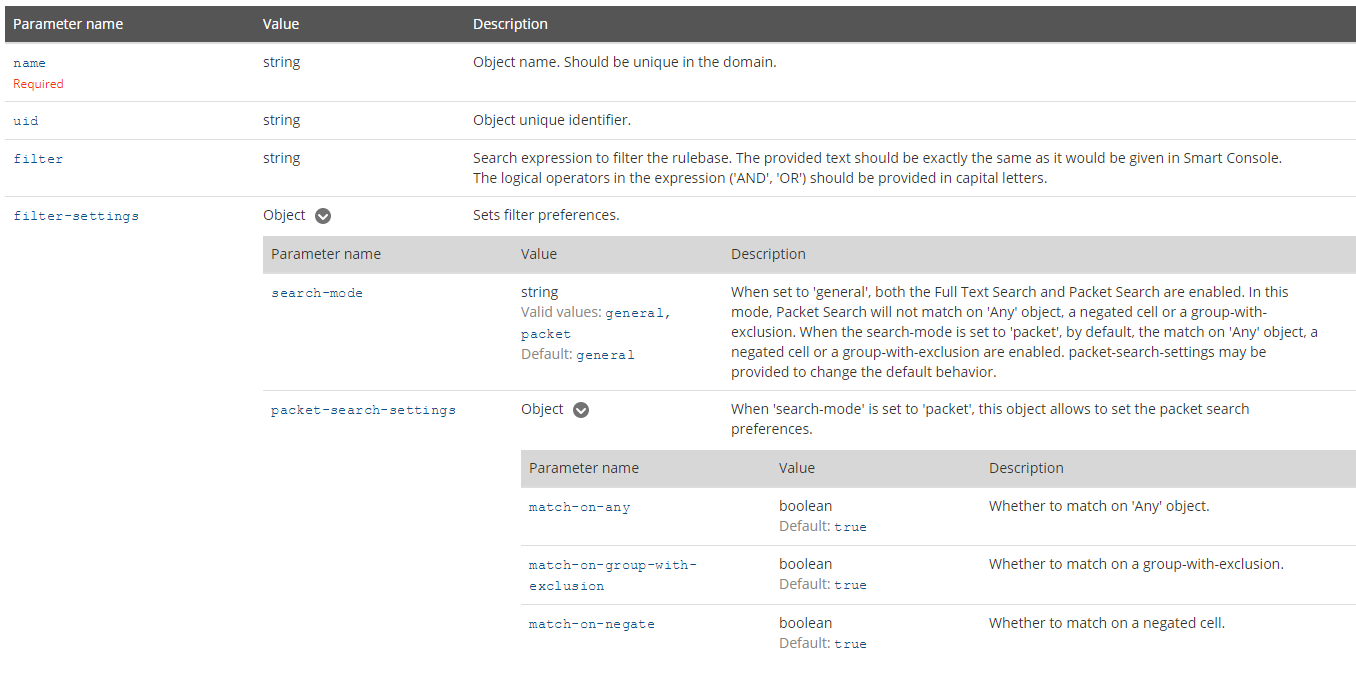
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tomer,
This link was incredibly helpful but I think I found a bug. When I run packet mode in the console I get the expected result. But when I run through the API it seems like the object ANY has the same uid as several services including http, dns, ftp, icmp, and probably more. So when I do the API call with packet mode, if I have dns, http, https, ftp, etc in the service column it will match ANY service and return the associated rule which is not correct. It works in the console which is the perplexing part. Any ideas??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How are you doing the API call?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So far just using either the CLI or with the API interface in the console. No external tools yet...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok then example CLI command you're using with the different results ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SmartDashboard:
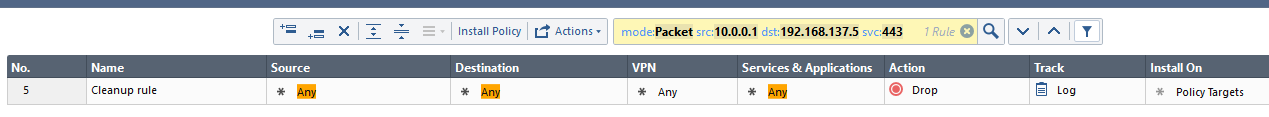
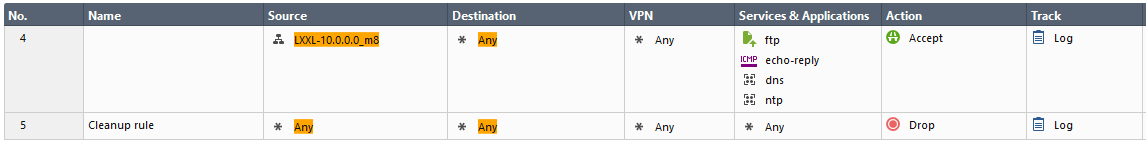
So upon closer inspection they're not all the same uid, just very close. But not sure why rule 4 shows up as a possible in CLI vs in UI
You'll also notice at the bottom that it is showing it matched on two rules for the same filter, the other being rule 4. Snip with rule 4 below included so you can see there is no https in the service column
CLI:
> show access-rulebase name network filter "src:10.0.0.1 dst:192.168.137.5 svc:443" filter-settings.search-mode packet
uid: "8a5e96fb-c793-457f-b78f-c667074223a5"
name: "Network"
rulebase:
- uid: "14568d6e-eb4d-4f84-9bca-0ebe438c67e6"
type: "access-rule"
domain:
uid: "41e821a0-3720-11e3-aa6e-0800200c9fde"
name: "SMC User"
domain-type: "domain"
rule-number: 4
filter-match-details:
- column: "source"
objects:
- "432f5a1a-1eb0-45cd-b860-261c984e377d"
track:
type: "598ead32-aa42-4615-90ed-f51a5928d41d"
per-session: false
per-connection: true
accounting: false
alert: "none"
source:
- "432f5a1a-1eb0-45cd-b860-261c984e377d"
source-negate: false
destination:
- "97aeb369-9aea-11d5-bd16-0090272ccb30"
destination-negate: false
service:
- "97aeb3d0-9aea-11d5-bd16-0090272ccb30"
- "97aeb406-9aea-11d5-bd16-0090272ccb30"
- "97aeb46b-9aea-11d5-bd16-0090272ccb30"
- "97aeb470-9aea-11d5-bd16-0090272ccb30"
service-negate: false
vpn:
- "97aeb369-9aea-11d5-bd16-0090272ccb30"
action: "6c488338-8eec-4103-ad21-cd461ac2c472"
action-settings:
enable-identity-captive-portal: false
content:
- "97aeb369-9aea-11d5-bd16-0090272ccb30"
content-negate: false
content-direction: "any"
time:
- "97aeb369-9aea-11d5-bd16-0090272ccb30"
custom-fields:
field-1: ""
field-2: ""
field-3: ""
meta-info:
lock: "unlocked"
validation-state: "ok"
last-modify-time:
posix: 1533138381161
iso-8601: "2018-08-01T08:46-0700"
last-modifier: "admin"
creation-time:
posix: 1533138052702
iso-8601: "2018-08-01T08:40-0700"
creator: "admin"
comments: ""
enabled: true
install-on:
- "6c488338-8eec-4103-ad21-cd461ac2c476"
- uid: "0f62cb69-736a-4559-a6d0-a54048abb3eb"
name: "Cleanup rule"
type: "access-rule"
domain:
uid: "41e821a0-3720-11e3-aa6e-0800200c9fde"
name: "SMC User"
domain-type: "domain"
rule-number: 5
filter-match-details:
- column: "source"
objects:
- "97aeb369-9aea-11d5-bd16-0090272ccb30"
track:
type: "598ead32-aa42-4615-90ed-f51a5928d41d"
per-session: false
per-connection: true
accounting: false
alert: "none"
source:
- "97aeb369-9aea-11d5-bd16-0090272ccb30"
source-negate: false
destination:
- "97aeb369-9aea-11d5-bd16-0090272ccb30"
destination-negate: false
service:
- "97aeb369-9aea-11d5-bd16-0090272ccb30"
service-negate: false
vpn:
- "97aeb369-9aea-11d5-bd16-0090272ccb30"
action: "6c488338-8eec-4103-ad21-cd461ac2c473"
action-settings: {}
content:
- "97aeb369-9aea-11d5-bd16-0090272ccb30"
content-negate: false
content-direction: "any"
time:
- "97aeb369-9aea-11d5-bd16-0090272ccb30"
custom-fields:
field-1: ""
field-2: ""
field-3: ""
meta-info:
lock: "unlocked"
validation-state: "ok"
last-modify-time:
posix: 1533138382512
iso-8601: "2018-08-01T08:46-0700"
last-modifier: "admin"
creation-time:
posix: 1513308839753
iso-8601: "2017-12-14T19:33-0800"
creator: "System"
comments: ""
enabled: true
install-on:
- "6c488338-8eec-4103-ad21-cd461ac2c476"
objects-dictionary:
- uid: "6c488338-8eec-4103-ad21-cd461ac2c472"
name: "Accept"
type: "RulebaseAction"
domain:
uid: "a0bbbc99-adef-4ef8-bb6d-defdefdefdef"
name: "Check Point Data"
domain-type: "data domain"
- uid: "97aeb369-9aea-11d5-bd16-0090272ccb30"
name: "Any"
type: "CpmiAnyObject"
domain:
uid: "a0bbbc99-adef-4ef8-bb6d-defdefdefdef"
name: "Check Point Data"
domain-type: "data domain"
- uid: "97aeb46b-9aea-11d5-bd16-0090272ccb30"
name: "dns"
type: "service-group"
domain:
uid: "a0bbbc99-adef-4ef8-bb6d-defdefdefdef"
name: "Check Point Data"
domain-type: "data domain"
- uid: "6c488338-8eec-4103-ad21-cd461ac2c473"
name: "Drop"
type: "RulebaseAction"
domain:
uid: "a0bbbc99-adef-4ef8-bb6d-defdefdefdef"
name: "Check Point Data"
domain-type: "data domain"
- uid: "97aeb406-9aea-11d5-bd16-0090272ccb30"
name: "echo-reply"
type: "service-icmp"
domain:
uid: "a0bbbc99-adef-4ef8-bb6d-defdefdefdef"
name: "Check Point Data"
domain-type: "data domain"
- uid: "97aeb3d0-9aea-11d5-bd16-0090272ccb30"
name: "ftp"
type: "service-tcp"
domain:
uid: "a0bbbc99-adef-4ef8-bb6d-defdefdefdef"
name: "Check Point Data"
domain-type: "data domain"
port: "21"
- uid: "598ead32-aa42-4615-90ed-f51a5928d41d"
name: "Log"
type: "Track"
domain:
uid: "a0bbbc99-adef-4ef8-bb6d-defdefdefdef"
name: "Check Point Data"
domain-type: "data domain"
- uid: "432f5a1a-1eb0-45cd-b860-261c984e377d"
name: "LXXL-10.0.0.0_m8"
type: "network"
domain:
uid: "41e821a0-3720-11e3-aa6e-0800200c9fde"
name: "SMC User"
domain-type: "domain"
subnet4: "10.0.0.0"
mask-length4: 8
subnet-mask: "255.0.0.0"
- uid: "97aeb470-9aea-11d5-bd16-0090272ccb30"
name: "ntp"
type: "service-group"
domain:
uid: "a0bbbc99-adef-4ef8-bb6d-defdefdefdef"
name: "Check Point Data"
domain-type: "data domain"
- uid: "6c488338-8eec-4103-ad21-cd461ac2c476"
name: "Policy Targets"
type: "Global"
domain:
uid: "a0bbbc99-adef-4ef8-bb6d-defdefdefdef"
name: "Check Point Data"
domain-type: "data domain"
from: 1
to: 2
total: 2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SmartConsole UI search uses by default an "AND" operator between the operands, while API uses an "OR" operator.
Therefore the mismatch between the results.
If you run API command with "AND" between the operands, you will get the same results.
We will fix the API documentation to state this fact clearly.
Robert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Robert! That was the issue, definitely would be good to have the documentation reflect that.
The current document reads:
"Search expression to filter the rulebase. The provided text should be exactly the same as it would be given in Smart Console. The logical operators in the expression ('AND', 'OR') should be provided in capital letters."
The "exactly the same as it would be given in Smart Console" is what was throwing me off since I wasn't using any of the operators in the Console.
Thanks again for the help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dutch_Arling,
I have problems, when working with NSX-Security-Groups:
- mode: Packet src:1.2.3.4 dst:4.3.2.1 svc:12345
does not match the corresponding security-group, even though destination 4.3.2.1 is included in <My_Sec_Group>
I have to filter for:
- mode: Packet src:1.2.3.4 dst:"My_Sec_Group" svc:12345
to find the corresponding rule.
The other way round (I search for a Group but have a rule with a fix IP) neither works.
Is there a fix on this?
Best regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a somewhat old post, but this behaviour seems to still be the case in API 1.9 and the latest smart console. When using packet mode it doesn't include the data center objects. When using general, it will, but then rules with any won't show up in the results, so both situations won't reflect what will actually happen with the packet. I carefully looked through the API settings, but I can't get it to work. I could try to combine both results in my Checkpoint rule search webinterface, but I'm not sure what kind of trouble I'll then run into. 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
I reproduced the issue in my lab and opened an issue for relevant R&D owner.
Will monitor to see when it is fixed.
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Any news from the developers? I can also start a ticket through our Diamond support contract, if it's useful. But I guess the missing data center objects in the results when using packet mode is simply a bug, the developer probably will see the need to fix this anyway. The missing any objects when not using packet mode and also not having the option to include them anyway is a weird missing feature to me, but I don't have the whole overview, maybe a performance thing.
Regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Recommend opening a TAC case in parallel.
@Tal_Paz-Fridman can you provide the bug ID you opened?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Any news on this?
Just had another issue with it, some any rule accepted my packages while not found when searching for it...
Regards Niek
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The fix is currently targeted to our next major release.
I'll see if it can be pushed into the next JHF.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds good! Has this happened by now? If so, which release or version? We have 64k devices...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have another question about this; packet mode search does not seem to work overhere on the standby node from a active/passive MDS setup. I have not tried many usecases. It this is a bug or a feature?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 6 | |
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 |
Upcoming Events
Thu 25 Apr 2024 @ 11:00 AM (CEST)
CheckMates in Russian - Возможности и риски искусственного интеллектаThu 25 Apr 2024 @ 11:00 AM (CEST)
CheckMates in Russian - Возможности и риски искусственного интеллектаThu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center


