- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Mastering Compliance
Unveiling the power of Compliance Blade
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
May the 4th (+4)
Navigating Paradigm Shifts in Cyber
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Management
- :
- Re: Azure AD Application Proxy - Updatable objects
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Azure AD Application Proxy - Updatable objects
We are experiencing problems trying to use Azure AD updatable objects to allow an Azure AD Application Proxy host to phone home.
Two issues:
- Is there a reference document somewhere that explains what the various updatable objects actually reference. Each comment is currently simply a copy & paste to the same statement 'This is a Microsoft object, blah blah https://www.microsoft.com/en-us/download/details.aspx?id=56519'
- We constantly have to supplement the updatable objects with additional IPs. I presume CheckPoint have contacts at Microsoft that they can address this with?
Two examples:
- We use 802.1X for both wireless and wired (port based) authentication where we want users to utilise Azure AD as a MFA method of registering their devices to the network. We subsequently created a rule that allows access to 'Azure Active Directory Domain Public Services' and 'Azure Active Directory Public Services' but many requests flow to destinations not covered by these.
- We drop requests to unknown or uncategorised sites and want to allow 'Azure AD Connect' and 'Azure AD Application Proxy' hosts to connect back to Microsoft. There are again never ending hosts that we have to continually manually add to allowed network group objects.
My impression is that the current implementation is really half baked and whilst it ticks some boxes isn't reliable. Herewith some of the IPs we've had to add:
Regards
David Herselman
Labels
- Labels:
-
SmartConsole
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All Updatable Objects are backed by a feed provided by the relevant vendor (MSFT in this case).
You use the Domains Tool to see what is covered in a given Updatable Object.
See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately doesn't help:
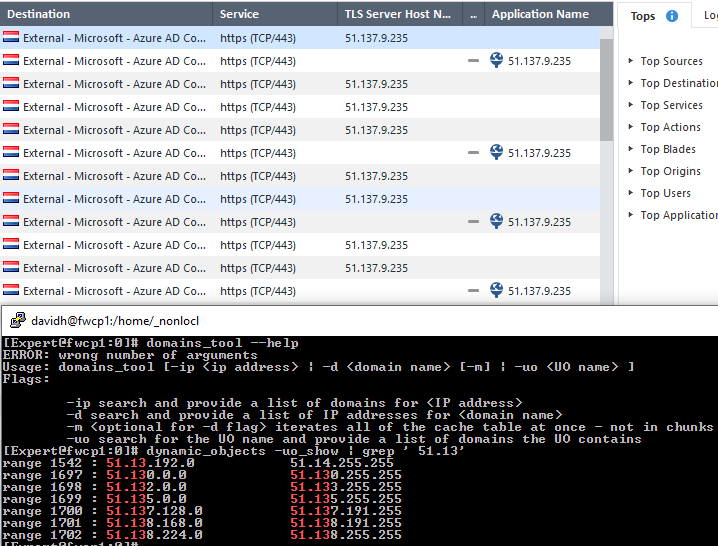
[Expert@fwcp1:0]# domains_tool -uo "Azure Active Directory Domain Public Services"
Domain tool looking for domains for 'Azure Active Directory Domain Public Services' and its children objects:
The updatable object Azure Active Directory Domain Public Services does not hold any domains
[Expert@fwcp1:0]# domains_tool -uo "Azure Active Directory Public Services"
Domain tool looking for domains for 'Azure Active Directory Public Services' and its children objects:
The updatable object Azure Active Directory Public Services does not hold any domains
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Digging into this a bit more, it looks like you can find the IPs in $CPDIR/database/ONLINE_SERVICES/1.0/<version>/azure.C on the gateway.
In any case, Microsoft is ultimately responsible for updating the feed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Undocumented switches and incomplete address lists. Does CheckPoint not have contact at Microsoft they could address this with?
My original question also hasn't been answered so I presume the answer is 'No, CheckPoint do not provide a clue anywhere at to what subnets are chosen from Microsoft's lists to create the updatable objects'.
ie: You can try figure out yourself what someone in R&D cooked together?
My impression is that functionality of this nature is of great interest, but unusable in it's current state = half baked...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like I said, Microsoft provide these lists, which are categorized.
There are, in fact, multiple lists.
For Azure US, it’s something like the following: https://www.microsoft.com/en-us/download/details.aspx?id=56519
See also: https://docs.microsoft.com/en-us/microsoft-365/enterprise/urls-and-ip-address-ranges?view=o365-world...
@Micky_Michaeli do we have a backchannel with Microsoft for matters like this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @PhoneBoy,
I had several meetings in the past with Microsoft people regarding multiple requests raised from our customers.
Unfortunately, almost all our requests were answered as "currently it's not in our roadmap".
As you wrote below, there are multiple objects for multiple services and the content can be viewed on the GW by running two commands, "dynamic_objects -uo_show" for getting the loaded IPs ranges and "domains_tool -uo <updatable objects name>" for getting the loaded domains.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
FYI, I just went through a similar exercise with a customer trying to troubleshoot an issue with Azure-related services and Updatable Objects.
We were able to confirm that the ranges specified in the JSON file available from Microsoft correspond to what shows when using the relevant object in the rulebase and you execute dynamic_objects -uo_show.
The trick in our case was figuring out which Updatable Objects to include based on the services they were trying to access.
Between the JSON file and looking at $CPDIR/database/downloads/ONLINE_SERVICES/1.0/<ver>/azure.C, I could see what objects needed to be included for this specific customer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
we have a similar issue.
We have a rule allowing http/https to "Office 365 Worldwide Services".
This rule also allows connection to IP 104.46.60.117 (kyocera.biz). This IP shouldn't be included in the O365 Services.
When I run a dynamic_objects -uo_show the range 379 : 104.46.24.0 104.46.127.255 is only included in the object CP_Azure_Azure. This object shouldn't be included in the object "Office 365 Worldwide Services".
Best regards,
Jan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Jan_Kleinhans,
The object "Office 365 Worldwide Services" contains IP addresses and domains as part of its content.
104.46.60.117 is not part of the IP addresses ranges of this object, this is correct, but it should be part of the domains associated to this object, that's why it's matched on it.
I tried to see the resolving responses of domains of kyocera.biz, all of them returned domains of cloudapp.net as their canonical name.
One of the domains of "Office 365 Worldwide Services" is *.cloudapp.net, that's why it's possible to have the same IPs for domains of cloudapp.net and kyocera.biz and that's why it's matched on this object.
few examples:
nslookup rfs-us.kyocera.biz
rfs-us.kyocera.biz canonical name = kfs-us02-devicerest.cloudapp.net.
Name: kfs-us02-devicerest.cloudapp.net
Address: 23.101.190.57
nslookup rfs.kyocera.biz
rfs.kyocera.biz canonical name = kfs-as02-devicerest.cloudapp.net.
Name: kfs-as02-devicerest.cloudapp.net
Address: 104.46.227.64
nslookup fs-us.kyocera.biz
fs-us.kyocera.biz canonical name = kfs-us02-userweb.cloudapp.net.
Name: kfs-us02-userweb.cloudapp.net
Address: 23.102.187.77
Best regards,
Micky
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Micky,
thanks for clarification. So the usage of "Microsoft O365 Worldwide Services" is a pain as it includes *.cloudapp.net which seems to be a bunch of websites which have nothing to do with O365. That is MS fault and not yours as I can see.
We will open a call with MS. Maybe they can remove *.cloudapp.net from the list.
Perhaps you could split the O365 services in categories as described here:
Best regards,
Jan
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 8 | |
| 6 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 05:00 PM (CEST)
SASE Masters: Deploying Harmony SASE for a 6,000-Strong Workforce in a Single WeekendAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center