- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
Mastering Compliance
Unveiling the power of Compliance Blade
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Threat Prevention
- :
- Re: Suspicious Activity Monitoring (SAM) Rules
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Suspicious Activity Monitoring (SAM) Rules
The challenge was to block a lot of pub IPs. Allocated via Mgmt-Server.
Example to allocate on all SGW's I do following on Mgmt Server (CP R80.30)
fw sam -I subdst 2.237.76.249 255.255.255.255
Everything is fine and this IP is blocked on all our SGW's R80.10 til R80.30.
Problem is to check which IPs are in kernel table in this "blocking modus".
-----
So I did on the SGW:
----
[Expert@SGW:0]# fw tab -t sam_blocked_ips
localhost:
-------- sam_blocked_ips --------
dynamic, id 8141, num ents 1175, load factor 2.29, attributes: keep, , hashsize 512, limit 50000
<a7567bb0; 00000000, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
->Example: a7=167 .56=186 .7b= 123 .b0=176 von HeX nach dEz !!!
IPv4= 167.186.123.176 !!!!
Actually 1175 entries are on this SGW active.
- How can I see all this entries ? ?
- Is there a table to copy and to relocate to IPv4 (all this 1175 IPs ) ??
---
My output is following:
[Expert@SGW:0]# fw tab -t sam_blocked_ips
localhost:
-------- sam_blocked_ips --------
dynamic, id 8141, num ents 1175, load factor 2.29, attributes: keep, , hashsize 512, limit 50000
<a7567bb0; 00000000, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<46a935ea; 00000000, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<9a78e3ce; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<68efafd3; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<2d5094a8; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<830067c8; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<ba926e6c; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<be8ec86c; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<18b57d3e; 00000000, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<d44996e9; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<02ed4cf9; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<ba54ad99; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<92b9fdaf; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<59bc7c91; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<566240bd; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
<4845632f; 00000001, 00000001, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000, 00000000>
...(16434 More)
3 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is better - for performance reasons - to block this on SecureXL level.
The SecureXL penalty box is a mechanism that performs an early drop of packets arriving from suspected sources.
Why not sam policy rules?
The SAM policy rules consume some CPU resources on Security Gateway. We recommend to set an expiration that gives you time to investigate, but does not affect performance. The best practice is to keep only the SAM policy rules that you need. If you confirm that an activity is risky, edit the Security Policy, educate users, or otherwise handle the risk. Or better use SecureXL penalty box from a performance point of view.
The purpose of this feature is to allow the Security Gateway to cope better under high load, possibly caused by a DoS/DDoS attack. These commands „fwaccel dos“ and „fwaccel6 dos“ control the Rate Limiting for DoS mitigation techniques in SecureXL on the local security gateway or cluster member.
In version R80.20, the penalty box feature is now supported in VSX mode and each virtual system can be independently configured for penalty box operation.
Attention!
In R80.20, all "sim erdos" commands are no longer supported. They have been replaced with equivalent commands which can be found under "fwaccel dos". Penalty box is configured separately for IPv4 and IPv6. IPv4 configuration is performed using the "fwaccel dos" command. IPv6 configuration is performed using the "fwaccel6 dos" command.
More read here: R80.x - Performance Tuning Tip - DDoS „fw sam“ vs. „fwaccel dos“
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw tab -t sam_blocked_ips -u will dump all the table entries.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pretty sure the "fw tab" command is documented in SK and in regular documentation as it's been around since the beginning of Check Point time. 😁
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You may try with "-f" prameter.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, the -f parameter don't show me all 1125 entries ! Only a lot of actually session.
I did SAM rules via CLI !!!! That's important !!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
One below command is there to see the IP address other than you mentioned.
fw sam_policy get
But, you can check all the IP addresses in SmartView Monitor -->Suspicious Activity Rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi , sorry but fw sam_policy get output is:
Get operation succeeded
no corresponding SAM policy requests
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
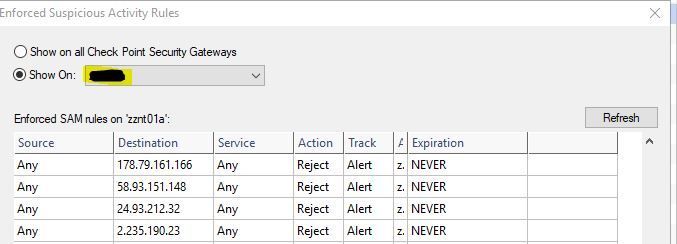
On SmartViewTracker I can see in a table following
..but how can I export or edit it for "CLI" Administration ? I have more than 1000 entries to check .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is better - for performance reasons - to block this on SecureXL level.
The SecureXL penalty box is a mechanism that performs an early drop of packets arriving from suspected sources.
Why not sam policy rules?
The SAM policy rules consume some CPU resources on Security Gateway. We recommend to set an expiration that gives you time to investigate, but does not affect performance. The best practice is to keep only the SAM policy rules that you need. If you confirm that an activity is risky, edit the Security Policy, educate users, or otherwise handle the risk. Or better use SecureXL penalty box from a performance point of view.
The purpose of this feature is to allow the Security Gateway to cope better under high load, possibly caused by a DoS/DDoS attack. These commands „fwaccel dos“ and „fwaccel6 dos“ control the Rate Limiting for DoS mitigation techniques in SecureXL on the local security gateway or cluster member.
In version R80.20, the penalty box feature is now supported in VSX mode and each virtual system can be independently configured for penalty box operation.
Attention!
In R80.20, all "sim erdos" commands are no longer supported. They have been replaced with equivalent commands which can be found under "fwaccel dos". Penalty box is configured separately for IPv4 and IPv6. IPv4 configuration is performed using the "fwaccel dos" command. IPv6 configuration is performed using the "fwaccel6 dos" command.
More read here: R80.x - Performance Tuning Tip - DDoS „fw sam“ vs. „fwaccel dos“
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
fw tab -t sam_blocked_ips -u will dump all the table entries.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello PhoneBoy,
many thanks.
fw tab -t sam_blocked_ips -u works and show all entries.
AddOn: Please add this cli command to a SK Articel - because I can't found it on any manuel /description.
Danke👏
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pretty sure the "fw tab" command is documented in SK and in regular documentation as it's been around since the beginning of Check Point time. 😁
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center