- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
Mastering Compliance
Unveiling the power of Compliance Blade
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Threat Prevention
- :
- IPS policy installation timestamp
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
IPS policy installation timestamp
Hi All,
I'm looking for a way within R80.10 to see a timestamp for when the last Threat Prevention (but more specifically, IPS) policy was installed. I know I can see firewall through fw stat. IPS stat only shows me that it is enabled and the signature update number which doesn't help for my use case. Is there a way to see when IPS or Threat Prevention policy was installed last? Thanks!
- Tags:
- ips update
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is in an easy way:
# fw stat -b AMW
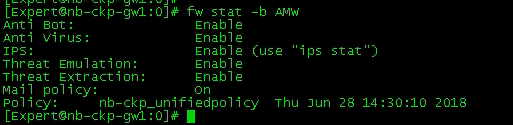
This is the information from cpview:
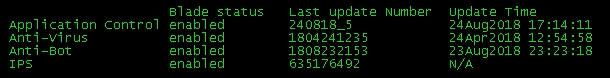
So to compare, the fw stat -b AMW shows the "Threat Prevention Policy Install Time", but in cpview you see the Online Updates of the services updating automatically.
There is not something like "IPS Policy" as you call it. IPS Signatures are applied via Threat Prevent Policy, but Core-Protections and Inspection-Setttings are applied via Access Policy. So both are relevant for you!
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can check this in installation history under Threat Tools in Threat Prevention policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply. I should've mentioned I need a way to verify this from the gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why?
The Check Point way is to use the centralized management for that.
MGMT also has this with REST API.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Think of it as a troubleshooting/trust but verify step ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Exactly! I need a way to verify outside of the management what policy is running on the gateway.
If it is the Check Point way, then why did Check Point build a command to view the firewall policy name and install time into the gateway?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It looks like cpstat will show this.
However, on my gateway (R80.10), the "update time" is N/A...
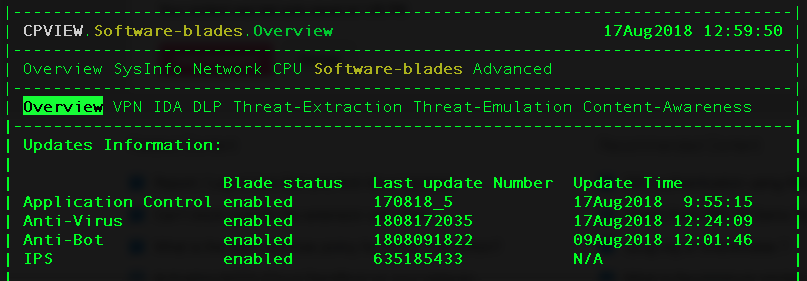
I also checked with cpstat -f ips blades (which should theoretically also show it) but I get an error on my system.
Maybe it works for you, though?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My gateway shows the same behavior, NA in CPVIEW and cpstat -f ips blades gives me an invalid flavour error. Works if I do cpstat -f fw blades but for some reason doesn't recognize the ips flavour.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
'ips stat' will also show the IPS version installed on the gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When I run ips stat it only shows me that IPS is enabled and the signature being used. No timestamp of install time
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct. Like I mentioned before, it will show the IPS version, which you could match to management.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So the problem is this shows me the current version of the signature database. I need to see the last time the policy was installed. So for example, if I go make a change within my IPS policy, say setting a signature from detect to prevent, or even changing the complete profile from strict to optimized it still shows me the same IPS signature database version. I need a way to show when the last policy was installed. I know it seems overly picky but I need to be able to show a reference for the IPS policy was last installed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I understand what you are trying to do. While I agree with others that SmartConsole would be best for getting this data or using the API to track this, I get there should be a way from the CLI. This is in no way an approved or verified method and please use at your own risk. The following command seems to return the date/time of the last IPS install.
ls -l /var/opt/CPsuite-R80/fw1/state/<gw_or_cluster_name>/AMW/* | grep IPS | awk '{print $6" "$7" "$8}'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is in an easy way:
# fw stat -b AMW

This is the information from cpview:

So to compare, the fw stat -b AMW shows the "Threat Prevention Policy Install Time", but in cpview you see the Online Updates of the services updating automatically.
There is not something like "IPS Policy" as you call it. IPS Signatures are applied via Threat Prevent Policy, but Core-Protections and Inspection-Setttings are applied via Access Policy. So both are relevant for you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Norbert,
Thanks for the reply, that was exactly what I needed! Just tested it out and it shows the Threat Prevention policy install separate from the Firewall policy install.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All.
Please advise do I need read/write account to run such command or I could do it with read-only?
Thank you.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 1 | |
| 1 |
Upcoming Events
Thu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center


