- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
Mastering Compliance
Unveiling the power of Compliance Blade
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Re: Is there SNI support for inbound HTTPS inspect...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Is there SNI support for inbound HTTPS inspection in R80.20?
Hi,
on gws R80.20 can I do HTTPS inspection on inbound connections that require SNI since on the server there are some virtual hosts with different certificates? If yes how?
Thanks in advance
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I checked with our experts in R&D and, provided you are on R80.30, you should be able to achieve it.
It should also work on R80.20 JHF 117 and above, but not sure it was tested there.
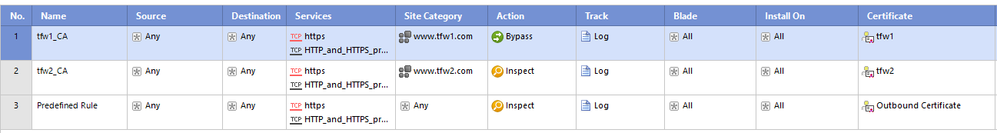
You can import the certificates into the gateway, create different custom application with each URL, and create an HTTPS Inspection rule with different certificate for each custom certificate similar to the following:
25 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure why it is necessary to inspect the SNI since the HTTPS Inspection sees the actual URL.
A more relevant question might be: do we duplicate the SNI from the client as part of the connection we made to the server?
Not sure.
A more relevant question might be: do we duplicate the SNI from the client as part of the connection we made to the server?
Not sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, maybe I was not clear enough. My question is: is there SNI support in R80.20?
What I would like to do is inspect HTTPS traffic that go toward some virtual hosts running on a server behind CP gws. Every virtual host has its own certificate.
Thanks
What I would like to do is inspect HTTPS traffic that go toward some virtual hosts running on a server behind CP gws. Every virtual host has its own certificate.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure is this your expect.
R80.30
State-of-the-Art HTTPS Inspection: New SSL Inspection Patent Pending Technologies. Delivering the power to inspect SSL-encrypted network traffic with secure SNI verification improvements.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Most of the requests for support for SNI are usually about Outbound Inspection.
More specifically, it's to see what site is really being accessed without resorting to HTTPS Inspection.
With inbound HTTPS Inspection, the connection will terminate on the gateway.
This requires the private certificate of the site in question.
We'll be able to see the exact URL the end user specifies in this case.
As such, we don't need SNI.
A network diagram would be very helpful to understand what you're trying to achieve.
More specifically, it's to see what site is really being accessed without resorting to HTTPS Inspection.
With inbound HTTPS Inspection, the connection will terminate on the gateway.
This requires the private certificate of the site in question.
We'll be able to see the exact URL the end user specifies in this case.
As such, we don't need SNI.
A network diagram would be very helpful to understand what you're trying to achieve.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"With inbound HTTPS Inspection, the connection will terminate on the gateway.
This requires the private certificate of the site in question.
We'll be able to see the exact URL the end user specifies in this case."
The URL is encrypted in the TLS sessions so the gateway needs to see the SNI, read what host the client needs to reach and select the right certificate to expose.
So in my opinion the SNI support it's necessary in inboud https inspection
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The URL being accessed is part of the HTTP request, which doesn't require SNI to see.
I've also never heard of anyone having inbound SNI issues.
In any case, we do SNI validation as part of R80.30.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What I do not understand is:
if I've a HTTPS server with only one IP and 10 virtual hosts, this server is behind a CP firewall how can I inspect traffic?
I cannot use HTTPS inspection because I've 10 certificates and only one IP, writing HTTPS inspection rule require to have one IP and one certificate, or am I wrong?
B-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
With 10 different certificates, it definitely would not work.
At a minimum, you'd have to create a new certificate that would be valid for all 10 hosts.
Specifically, it would have to list all 10 hosts in the Subject Alternate Name (SAN) field.
This will allow the remote browser to validate the certificate regardless of which of the 10 hosts you're ultimately accessing.
This certificate would then be used for Inbound SSL Inspection for all 10 sites.
Again, none of this has anything to do with SNI, which only matters when we're not terminating the TLS connection.
What I don't know is whether or not you can leave the certificate as-is on the other hosts.
Assuming the Security Gateway can validate those certificates as valid, I assume it would still work.
At a minimum, you'd have to create a new certificate that would be valid for all 10 hosts.
Specifically, it would have to list all 10 hosts in the Subject Alternate Name (SAN) field.
This will allow the remote browser to validate the certificate regardless of which of the 10 hosts you're ultimately accessing.
This certificate would then be used for Inbound SSL Inspection for all 10 sites.
Again, none of this has anything to do with SNI, which only matters when we're not terminating the TLS connection.
What I don't know is whether or not you can leave the certificate as-is on the other hosts.
Assuming the Security Gateway can validate those certificates as valid, I assume it would still work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have more than a hundred certificates in the same webserver (half of them are wildcards) and adding/replacing every month. To use only one certificate, even a SAN certificate, is not an option for us.
Do you know if it's there any chance to allow more than one certificate assigned to the same destination host for the https inbound analysis rules?
Regards!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is not possible because of how TLS works, i.e. it's not a Check Point specific limitation.
Specifically, the server must present its server certificate before the client can communicate what host it is connecting to via SNI.
As such, the server certificate must be valid for all possible servers accessible from that IP address.
Specifically, the server must present its server certificate before the client can communicate what host it is connecting to via SNI.
As such, the server certificate must be valid for all possible servers accessible from that IP address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @PhoneBoy,
Based on what you are saying here:
"Specifically, the server must present its server certificate before the client can communicate what host it is connecting to via SNI."
I don't believe that is true.
From: RFC 6066 3. Server Name Indication
TLS does not provide a mechanism for a client to tell a server the name of the server it is contacting. It may be desirable for clients to provide this information to facilitate secure connections to servers that host multiple 'virtual' servers at a single underlying network address. In order to provide any of the server names, clients MAY include an extension of type "server_name" in the (extended) client hello.
When the client supports SNI it will send the server name (in the extended field) in the client hello for the server (in our scenario the Check Point) to determine which certificate to send back.
The whole process of selecting which certificate to present / send is based on the SNI extension of the TLS protocol.
The reason that we use SNI is because with the use of TLS there is no way for the server to determine the HTTP host header because it is encapsulated in a TLS header.
So, without the use (support) of SNI the server cannot determine which certificate to send back to the client and if configured, it just throws "a" certificate which without the use of SAN would result in a "Untrusted Certificate" warning in your browser.
Regards,
Jelle
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I read that after I had posted my original message 😬
In any case, this should work in R80.30 with the configuration I've detailed elsewhere in the thread.
In any case, this should work in R80.30 with the configuration I've detailed elsewhere in the thread.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
For my case I need to block external user to access some website behide the gateway.
I have use custom application tool (sk103051) for custom SSL traffic with SNI. It works for blocked some website from same IP address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
When hosting different websites with different certificates (no wildcard) on the same IP address, it is not possible to configure this at the moment, so I guess this means there is no SNI support for inbound HTTPS?
Regards,
Erik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Again, this issue has nothing to do with (lack of) SNI support.
It's a function of how TLS works.
If a given IP serves multiple HTTPS websites, the certificate presented must be valid for all the websites.
It's a function of how TLS works.
If a given IP serves multiple HTTPS websites, the certificate presented must be valid for all the websites.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi PhoneBoy,
It is possible to configure multiple independent certificates (different domains, so no wildcard possible) on a single IP. This only works with browsers and webservers that support SNI. But since this is currently not configurable in the HTTPS inspection I suppose this feature is not supported.
Or will it work if we add multiple rules with the same source IP, destination IP and port number, but different inbound certificates?
Regards,
Erik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure it works that way, but you can try it on R80.30 or R80.20 JHF 117 or later.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I checked with our experts in R&D and, provided you are on R80.30, you should be able to achieve it.
It should also work on R80.20 JHF 117 and above, but not sure it was tested there.
You can import the certificates into the gateway, create different custom application with each URL, and create an HTTPS Inspection rule with different certificate for each custom certificate similar to the following:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You will also be able to achieve this on R80.20 JHF 118 and above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It does not work. policy installation fail because "“rule 1 si not valid because its site category column must contain only the any object (inbound rule)."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Michele,
This scenario has been tested in the QA department.
Please contact me and I'll try to help you.
Regards,
Danny
This scenario has been tested in the QA department.
Please contact me and I'll try to help you.
Regards,
Danny
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Danny, I am experiencing the same verification issue in the latest take R80.40
I've tried multiple variations of creating the https inspection policy using application (unified policy), can you expand on the above as I feel like I'm missing something. I can open a case with TAC otherwise but have not found much in the documentation to say this is supported.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Paolo_Francese ,
R80.20 with enabled HTTPS interception:
If the https interseption is enabled, the parameter host from http can be used for the url because the traffic is analyzed by active streaming. Check Point Active Streaming (CPAS) allow the changing of data, we play the role of “man in the middle”. CPAS breaks the connection into two parts using our own stack – this mean, we are responsible for all the stack work (dealing with options, retransmissions, timers etc.). An application is register to CPAS when a connection start and supply callbacks for event handler and read handler. Several protocols uses CPAS, for example: HTTPS, VoIP (SIP, Skinny/SCCP, H.323, etc.), Security Servers processes, etc. CPAS breaks the HTTPS connection into two parts using our own stack – this mean, we are responsible for all the stack work (dealing with options, retransmissions, timers etc.)
More read here: R80.x Security Gateway Architecture (Content Inspection)
R80.20 without enabled HTTPS interception:
If the https interseption is disabled, SNI is used to recognize the virtual URL for application control and url filtering.
More read here: URL Filtering using SNI for HTTPS websites.pdf
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Better use R80.30:-)
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.20 with JHF 117 and above apparently has the improved SNI support.
If you're on an earlier JHF, we are not looking at SNI.
If you're on an earlier JHF, we are not looking at SNI.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 14 | |
| 10 | |
| 8 | |
| 5 | |
| 5 | |
| 5 | |
| 3 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Thu 25 Apr 2024 @ 11:00 AM (CEST)
CheckMates in Russian - Возможности и риски искусственного интеллектаThu 25 Apr 2024 @ 11:00 AM (CEST)
CheckMates in Russian - Возможности и риски искусственного интеллектаThu 02 May 2024 @ 10:00 AM (CEST)
CheckMates Live BeLux: How Can Check Point AI Copilot Assist You?About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center