I have a 81.10 Security gateway with two WAN interfaces, representing two ISPs:
eth1 - IP: x.x.x.97 (default route thru here)
eth5 - IP: x.x.x.103 (backup default route gets installed if eth1 peer goes down)
Behind this gateway I have 10.10.171.0/24
I have a remote 3rd party peer with one interface:
eth3 - IP: z.z.z.201
Behind this gateway I have 192.168.1.0/24
I have initially setup my tunnel like so:
Checkpoint Enc Domain: 10.10.171.0/24 VPN Peer with: z.z.z.201
Remote Enc Domain: 192.168.1.0/24 VPN Peer with x.x.x.97
.. and it is flowing thru eth1
I'm now attempting to test a failover scenario and on the 3rd party peer - I want to be able to switch the VPN Peer on the 3rd party device to use x.x.x.103, but I cannot get the Checkpoint to route of that interface. The best I've gotten is an initiated tunnel, 3rd party sends to eth5, but response packets seem to be still going out the default route (eth1)
I have done my best to read this doc: https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_SitetoSiteVPN_AdminGuide/Topics-VP...
And I'm also referencing these threads:
https://community.checkpoint.com/t5/General-Topics/How-to-create-a-IPSEC-VPN-tunnel-through-multiple...
https://community.checkpoint.com/t5/General-Topics/IPSec-VPN-Link-Selection/m-p/10724
This is how I have the general gateway cluster configured for IPSec VPN Link Selection:
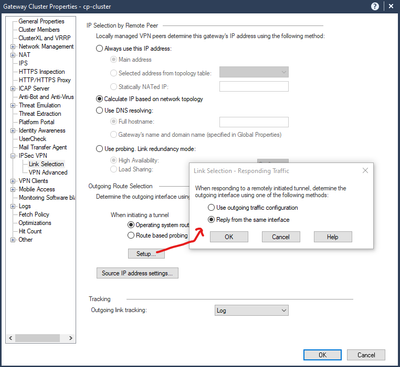
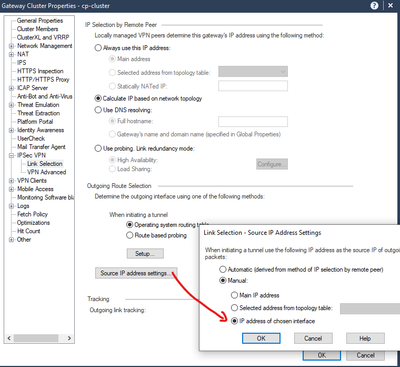
And on the "Interoperable Device" representing the 3rd party peer:
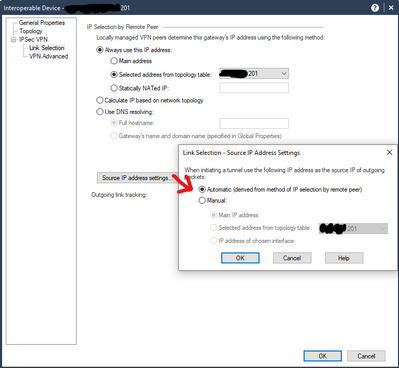
By all the other posts this seems to be doable but I'm not having any luck. Perhaps I'm misunderstanding something.
The only way I can get it to work is by:
- adding a static route back to z.z.z.201 to route through ISP at eth5
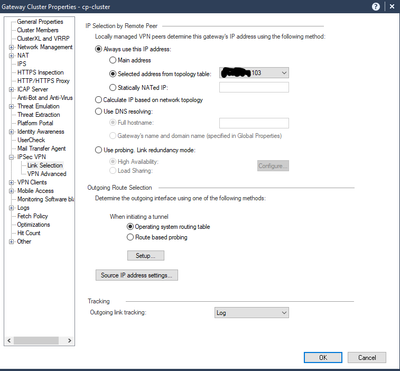
Could anyone shed some light?
For further reference, my default routing table:








