- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Mastering Compliance
Unveiling the power of Compliance Blade
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
May the 4th (+4)
Navigating Paradigm Shifts in Cyber
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: R80.x Security Gateway Architecture (Logical P...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.x Security Gateway Architecture (Logical Packet Flow)
| Introduction |
|---|
This document describes the packet flow (partly also connection flows) in a Check Point R80.10 and above with SecureXL and CoreXL, Content Inspection, Stateful inspection, network and port address translation (NAT), MultiCore Virtual Private Network (VPN) functions and forwarding are applied per-packet on the inbound and outbound interfaces of the device. There should be an overview of the basic technologies of a Check Point Firewall. We have also reworked the document several times with Check Point, so that it is now finally available.
| Chapter |
|---|
More interesting articles:
- R80.x Architecture and Performance Tuning - Link Collection
- Article list (Heiko Ankenbrand)
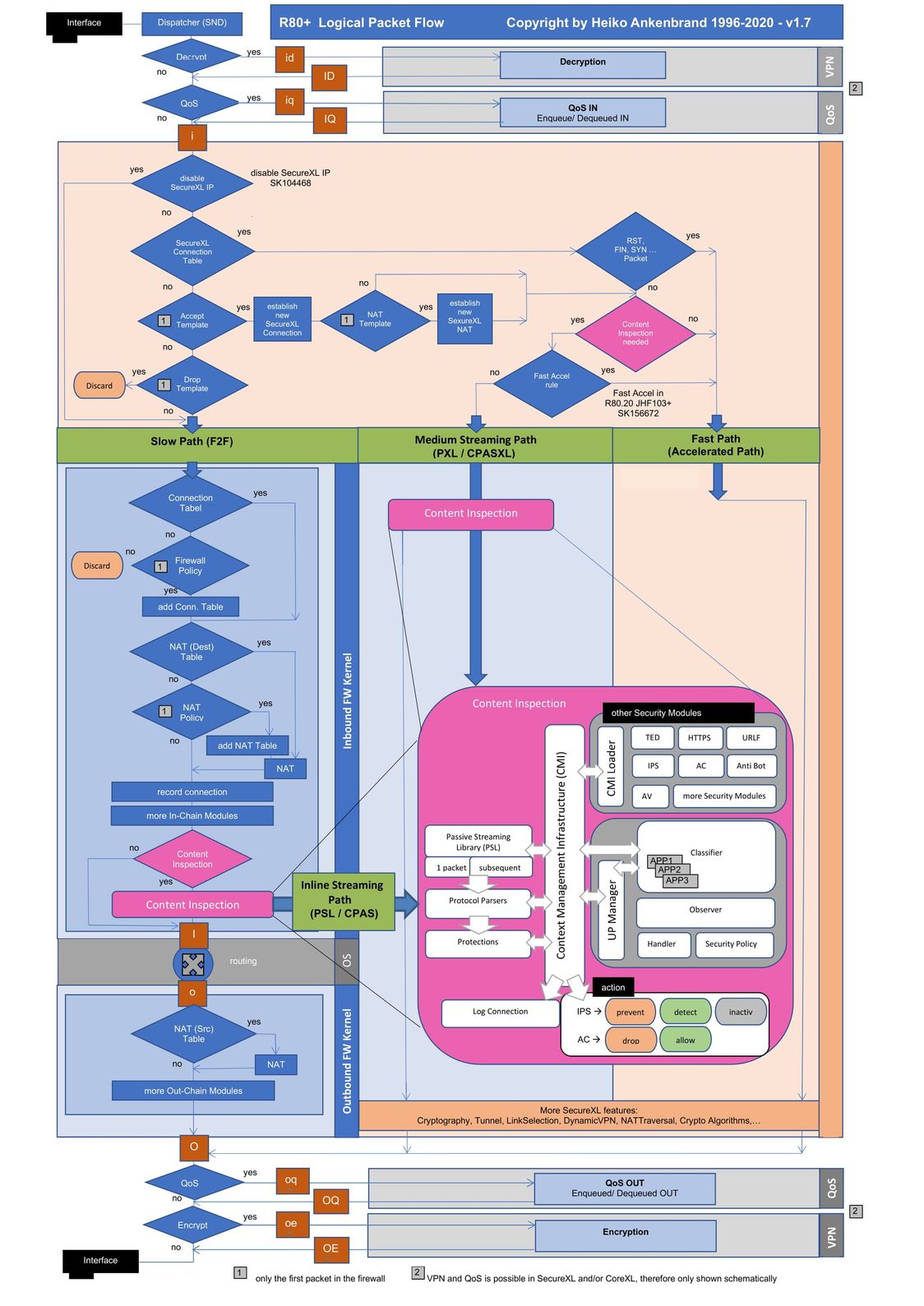
| Logical Packet Flow R80.10 |
|---|
Attention!
Starting with R80.20 the flows in the firewall have changed.
Therefore the flows can no longer be shown 100% in a drawing. This drawing can only be used as a schematic view. For example, correction flows are used to reinject packets. SecureXL parts are now executed in the inspection code. The processing of accept templates and rule based checks have also changed. A drawing is provided below in this article. If you want to know how the packets physically pass through the firewall, please open TAC tickets or use Check Point training. Please note that the content inspection is one unit and in this image it is divided into two parts to better explain the flows. Encryption, decryption and QoS are performed in SecureXL or CoreXL, depending on whether SecureXL is switched on or off. I have worked about 100 hours on this article and the pictures and am looking for a solution how to display it 100% in R80.40 or in future in R81.
| Download |
|---|
Download: R80.x Flowchart v1.6 PDF (new R80.10 version)
Download: R80.30 Flowchart v1.5 PDF (old R80.10 version)
| What's new in R80.10 and above |
|---|
R80.10 and above offer many technical innovations regarding R77. I will look at the following in this article:
- new fw monitor inspection points for VPN (e and E)
- new MultiCore VPN
- UP Manager
- Content Awareness (CTNT)
R80.20 and above:
- SecureXL has been significantly revised in R80.20. It now works in user space. This has also led to some changes in "fw monitor"
- There are new fw monitor chain (SecureXL) objects that do not run in the virtual machine.
- Now SecureXL works in user space. The SecureXL driver takes a certain amount of kernel memory per core and that was adding up to more kernel memory than Intel/Linux was allowing.
- SecureXL supportes now Async SecureXL with Falcon cards
- That's new in acceleration high level architecture (SecureXL on Acceleration Card): Streaming over SecureXL, Lite Parsers, Scalable SecureXL, Acceleration stickiness
- Policy push acceleration on Falcon cards
- Falcon cards for: Low Latency, High Connections Rate, SSL Boost, Deep Inspection Acceleration, Modular Connectivity, Multible Acceleration modules
- Falcon card compatible with 5900, 15000 & 23000 Appliance Series > 1G (8x1 GbE), 10G (4x10 GbE) and 40G (2x40 GbE)
R80.30 and above:
- In R80.30+, you can also allocate a core for management traffic if you have 8 or more cores licensed, but this is not the default.
- Active streaming for https with full SNI support.
R80.40 and above:
- Support for automatic allocation of CoreXL SNDs and Firewall instances that does not require a Security Gateway reboot.
- CoreXL and Multi-Queue: Improved out of the box experience - Security Gateway automatically changes the number of CoreXL SNDs and Firewall instances and the Multi-Queue configuration based on the current traffic load.
- Check Point's Security Gateway now support HTTP/2
- A new Policy Layer in SmartConsole dedicated to TLS Inspection and different TLS Inspection layers can be used in different policy packages.
- Enhanced NAT port allocation mechanism - on Security Gateways with 6 or more CoreXL Firewall instances, all instances use the same pool of NAT ports, which optimizes the port utilization and reuse.
- Multiple CoreXL Firewall instances handle the SIP protocol to enhance performance.
- Cluster Control Protocol encryption is now enabled by default.
R80.20 EA and above:
-
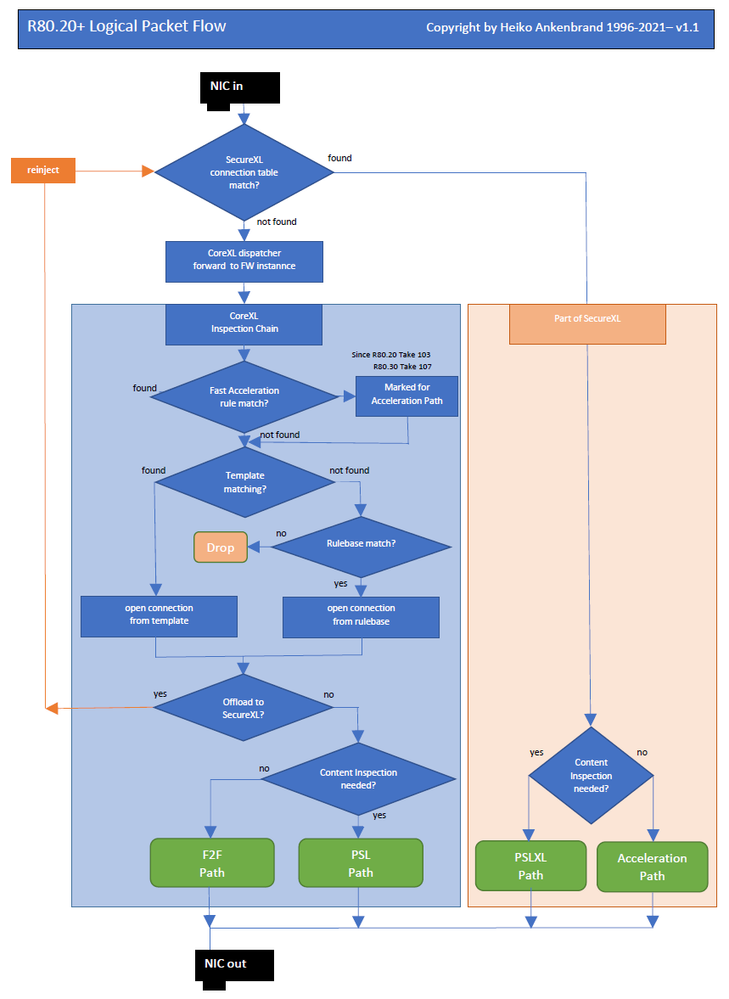
| Logical Packet Flow R80.20+ |
|---|
SecureXL has been significantly revised in R80.20. This has also led to some changes in "fw monitor". There are new fw monitor chain (SecureXL) objects that do not run in the virtual machine. Now SecureXL works in part in user space. The SecureXL driver takes a certain amount of kernel memory per core and that was adding up to more kernel memory than Intel/Linux was allowing. The packet flow in R80.20+ is a little bit different from the flow lower than R80.20. Now it is possible to use async SecureXL and other new functions. This figure shows the new features with the reinjection of SecureXL packages. SecureXL supportes now also Async SecureXL with Falcon cards. That's new in acceleration high level architecture (SecureXL on Acceleration Card): Streaming over SecureXL, Lite Parsers, Scalable SecureXL, Acceleration stickiness.
F2V - Describes "Forward to Virtual Machine" path. F2V stands for "Forward to Virtual Machine" from version R80.20 and above. These packets always belong to an existing connection, which are optimized via the SecureXL path. If a packet needs a new Rulbase look up in the SXL path, it is sent to the F2V path. When the rule base lookup is done, the packet is reinjected into the SXL path (accelerated path).
As a result, packets are reinjected with the new SecureXL ID into the correct SecureXL instance again after they have been allowed by access template or rule set. After the packet has been reinjected, the SecureXL ID is added to the SecureXL connetion table and the packet is forwarded to the correct SecureXL instance. Therefore the flow is slightly different to older version before R80.20. This new mechanism also offers the possibility to transfer packets into a new SecureXL instance on Falcon cards.
Whats new in R80.20/R80.30+:
Now there are several SecureXL instances possible. As a result, there are now eight pathes in R80.20/R80.30 and nine in R80.40 instead of six in R80.10. (I will make a drawing with the new paths in the near future).
|
Path |
R80.10 |
R80.20 |
R80.30 |
R80.40 |
R81.20 |
|
Firewall Path (F2F - slow path) |
X |
X |
X |
X |
|
|
F2V (Forward to Virtual Machine) |
|
X |
X |
X |
|
|
Accelerated Path (Fast Path) |
X |
X |
X |
X |
|
|
Accelerated VPN Path |
X |
X |
X |
X |
|
|
Medium Path (PXL/PSL)* |
X |
- |
- |
- |
|
|
Medium Streaming Path PXL/CPASXL* |
- |
X |
X |
X |
|
|
Inline Streaming Path PSL/CPAS* |
- |
X |
X |
X |
|
|
Buffer Path |
- |
- |
- |
X |
|
|
TLS Decrypt |
- |
- |
- |
X |
|
|
TLS Parser |
- |
- |
- |
X |
|
|
HTTP Disp |
- |
- |
- |
X |
|
|
ADVP - Advanced Patterns |
- |
- |
- |
X |
|
|
WS LITE |
- |
- |
- |
X |
|
|
FireWall QoS Path |
X |
X |
X |
X |
|
|
Accelerated QoS Path |
X |
X |
X |
X |
|
|
PSL inline Path |
- |
X |
X |
X |
- |
|
PSL Pipeline Path |
- |
- |
- |
- |
new |
*) Starting with version R80.20, the medium path is split into two paths "Medium Streaming Path" and "Inline Streaming Path"
PXL vs. PSLXL - Technology name for combination of SecureXL and PSL. PXL was renamed to PSLXL in R80.20. This is from my point of view the politically correct better term.
| Packet Flow with Falcon Cards |
|---|
R80.20 SecureXL adds support for offloading on Falcon cards from appliance to acceleration card leaving the appliance to do more. The following flowchart shows the new R80.20/r80.30 offloaded architecture in pink.
Host Path - For non acceleration connections (eg. local connections) and connections on non acceleration card interface.
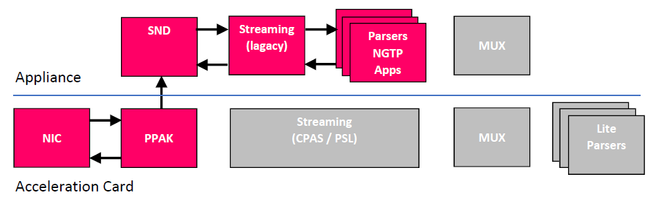 |
Buffer path - For HTTP requests, HTTP response headers and TLS handshakes.
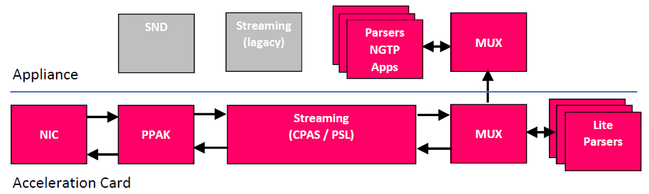 |
Inline path - For HTTP response body (until 1st tier match) and TLS bulk encryption/ decryption.
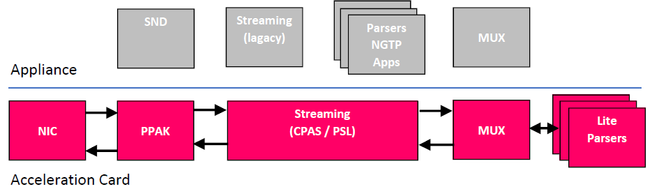 |
For the new acceleration Falcon card architecture with R80.20+ and SecureXL offloading read this article:
R80.x Security Gateway Architecture (Acceleration Card Offloading):
| VPN |
|---|
Decrypting a packet:
R80.10 and R80.20 introduced MultiCore support (it is new in R80 and above) for IPsec VPN. An IPSec packet enters the Security Gateway. The decrypted original packet is forwarded to the connection CoreXL FW instance for FireWall inspection at Pre-Inbound chain "i" from SND. The decrypted inspected packet is sent to the OS Kernel.
Encrypting a packet:
Encryption information is prepared at Post-Outbound chain "O". The vpnk module on the tunnel CoreXL FW instance gets the packet before encryption at chain "e". The encryption packet is forwarded to the connection CoreXL FW instance for FireWall from SND. The packet is encrypted by vpnk module at chain "E". Afterwards the IPsec packet is sent out on interface. This fw monitor inspection points "e" and "E" are new in R80.10 and "oe" and "OE" are new in R80.20.
Note: It's true, they only exist on the outbound side for encrypting packets not for decrypting packets on inbound side.
R80.20 VPN+SecureXL and above: (SK151114) Disabling acceleration by running fwaccel off will not have an immediate effect on IPsec acceleration, as it did before R80.20. Using fwaccel off, will cause every existing VPN connection to continue to be processed by the acceleration module (SecureXL), and only new connections will not be offloaded to the acceleration module. As long as there are accelerated VPN connections associated with the IPsec tunnel, all decryption/encryption operations will continue to be handled by the acceleration module.
VPN before R80.20, VPN connections could be migrated between acceleration module and Firewall-1 instances due to synchronous communication between those modules.
VPN since R80.20, fwaccel off does not stop the SecureXL device, and the communication between SecureXL and firewall-1 is now asynchronous. All connections that were accelerated will continue to be handled by PPAK. Furthermore, when new decryption/encryption keys are generated, the decision whether to accelerate the tunnel or not depends on whether there are accelerated connections associated with the tunnel. As a result, to disable VPN tunnel acceleration all outstanding related connections should be terminated. This behavior prevents disabling acceleration of tunnels as long as accelerated connections are associated with those tunnels.
| Firewall Core |
|---|
Inbound Stateless Check:
The firewall does preliminary “stateless” checks that do not require context in order to decide whether to accept a packet or not. For instance we check that the packet is a valid packet and if the header is compliant with RFC standards.
Anti-Spoofing:
Anti-Spoofing verifies that the source IP of each packet matches the interface, on which it was encountered. On internal interfaces we only allow packets whose source IP is within the user-defined network topology. On the external interface we allow all source IPs except for ones that belong to internal networks.
Connection Setup:
A core component of the Check Point R80.x Threat Prevention gateway is the stateful inspection firewall. A stateful firewall tracks the state of network connections in memory to identify other packets belonging to the same connection and to dynamically open connections that belong to the same session. Allowing FTP data connections using the information in the control connection is one such example. Using Check Point INSPECT code the firewall is able to dynamically recognize that the FTP control connection is opening a separate data connection to transfer data. When the client requests that the server generate the back-connection (an FTP PORT command), INSPECT code extracts the port number from the request. Both client and server IP addresses and both port numbers are recorded in an FTP-data pending request list. When the FTP data connection is attempted, the firewall examines the list and verifies that the attempt is in response to a valid request. The list of connections is maintained dynamically, so that only the required FTP ports are opened.
| SecureXL |
|---|
SecureXL is a software acceleration product installed on Security Gateways. Performance Pack uses SecureXL technology and other innovative network acceleration techniques to deliver wire-speed performance for Security Gateways. SecureXL is implemented either in software or in hardware:
- SAM cards on Check Point 21000 appliances
- ADP cards on IP Series appliances
- Falcon cards (new in R80.20) on different appliances
The SecureXL device minimizes the connections that are processed by the INSPECT driver. SecureXL accelerates connections on two ways.
New in R80.10:
In R80.10 SecureXL adds support for Domain Objects, Dynamic Objects and Time Objects. CoreXL accelerates VPN traffic by distributing Next Generation Threat Prevention inspection across multiple cores.
New in R80.20:
SecureXL was significantly revised in R80.20. It no longer works in Linux kernel mode but now in user space. In kernel mode resources (for example memory) are very limited. This has the advantage that more resources can be used in user space.
The SecureXL driver takes a certain amount of kernel memory per core and that was adding up to more kernel memory than Intel/Linux was allowing. On the 23900 in particular, we could not leverage all the processor cores due to this limitation. By moving all or most of SecureXL to user space, it's possible to leverage more processor cores as the firewall can entirely run in user space.It still doesn't by default in R80.20 in non-VSX mode, but it can be enabled.
It also means certain kinds of low-level packet processing that could not easily be done in SecureXL because it was being done in the kernel now can. For VSX in particular, it means you can now configure the penalty box features on a per-VS basis. It also improves session establishment rates on the higher-end appliances.
In addition, the following functions have been integrated in R80.20 SecureXL:
- SecureXL on Acceleration Cards (AC)
- Streaming over SecureXL
- Lite Parsers
- Async SecureXL
- Scalable SecureXL
- Acceleration stickiness
- Policy push acceleration
Throughput Acceleration - The first packets of a new TCP connection require more processing when processed by the firewall module. If the connection is eligible for acceleration, after minimal security processing the packet is offloaded to the SecureXL device associated with the proper egress interface. Subsequent packets of the connection can be processed on the accelerated path and directly sent from the inbound to the outbound interface via the SecureXL device.
Connection Rate Acceleration SecureXL also improves the rate of new connections (connections per second) and the connection setup/teardown rate (sessions per second). To accelerate the rate of new connections, connections that do not match a specified 5 tuple are still processed by SecureXL. For example, if the source port is masked and only the other 4 tuple attributes require a match. When a connection is processed on the accelerated path, SecureXL creates a template of that connection that does not include the source port tuple. A new connection that matches the other 4 tuples is processed on the accelerated path because it matches the template. The firewall module does not inspect the new connection, increasing firewall connection rates.
SecureXL and the firewall module keep their own state tables and communicate updates to each other.
- Connection notification - SecureXL passes the relevant information about accelerated connections that match an accept template.
- Connection offload - Firewall kernel passes the relevant information about the connection from firewall connections table to SecureXL connections table.
In addition to accept templates the SecureXL device is also able to apply drop templates which are derived from security rules where the action is drop. In addition to firewall security policy enforcement, SecureXL also accelerates NAT, and IPsec VPN traffic.
QXL - Technology name for combination of SecureXL and QoS (R77.10 and above).This has no direct association with PXL. It is used exclusively for QoS. But also here it is possible to use the QoS path in combination with PSL.
SAM card and Falcon card (R80.20 and above) - Security Acceleration Module card. Connections that use SAM/Falcon card, are accelerated by SecureXL and are processed by the SAM/Falcon card's CPU instead of the main CPU (refer to 21000 Appliance Security Acceleration Module Getting Started Guide)).
SecureXL use the following templates:
If templating is used under SecureXL, the templates are created when the firewall ruleset is installed.
Accept Template - Feature that accelerates the speed, at which a connection is established by matching a new connection to a set of attributes. When a new connection matches the Accept Template, subsequent connections are established without performing a rule match and therefore are accelerated. Accept Templates are generated from active connections according to policy rules. Currently, Accept Template acceleration is performed only on connections with the same destination port (using wildcards for source ports).
Accept Tamplate is enabled by default if SecureXL is used.
Drop Template - Feature that accelerates the speed, at which a connection is dropped by matching a new connection to a set of attributes. When a new connection matches the Drop Template, subsequent connections are dropped without performing a rule match and therefore are accelerated. Currently, Drop Template acceleration is performed only on connections with the same destination port (does not use wildcards for source ports).
Drop Template is disabled by default if SecureXL is used. It can be activated via smart Dashboard and does not require a reboot of the firewall.
NAT Templates - Using SecureXL Templates for NAT traffic is critical to achieve high session rate for NAT. SecureXL Templates are supported for Static NAT and Hide NAT using the existing SecureXL Templates mechanism. Normally the first packet would use the F2F path. However, if SecureXL is used, the first packet will not be forwarded to the F2F path if Accept Tamplate and NAT Template match. Enabling or disabling of NAT Templates requires a firewall reboot.
R80.10 and lower: NAT Template is disabled by default.
R80.20 and above: NAT Template is enabled by design.
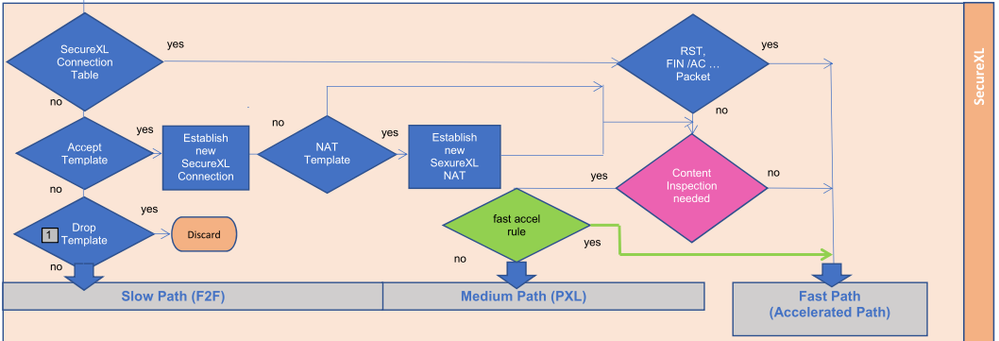
SecureXL path:
Fast path (Accelerated Path) - Packet flow when the packet is completely handled by the SecureXL device. It is processed and forwarded to the network.
Note: In many discusions and images, the SXL path is marked with the "accelerated path". This also happened to me by mistake in this flowchart.
Medium path (PXL) - The CoreXL layer passes the packet to one of the CoreXL FW instances to perform the processing (even when CoreXL is disabled, the CoreXL infrastructure is used by SecureXL device to send the packet to the single FW instance that still functions). When Medium Path is available, TCP handshake is fully accelerated with SecureXL. Rulebase match is achieved for the first packet through an existing connection acceleration template. SYN-ACK and ACK packets are also fully accelerated. However, once data starts flowing, to stream it for Content Inspection, the packets will be now handled by a FWK instance. Any packets containing data will be sent to FWK for data extraction to build the data stream. RST, FIN and FIN-ACK packets once again are only handled by SecureXL as they do not contain any data that needs to be streamed. This path is available only when CoreXL is enabled.
Packet flow when the packet is handled by the SecureXL device, except for:
- IPS (some protections)
- VPN (in some configurations)
- Application Control
- Content Awareness
- Anti-Virus
- Anti-Bot
- HTTPS Inspection
- Proxy mode
- Mobile Access
- VoIP
- Web Portals.
PXL vs. PSLXL - Technology name for combination of SecureXL and PSL. PXL was renamed to PSLXL in R80.20. This is from my point of view the politically correct better term.
Medium path (CPASXL) - Now also CPAS use the SecureXL path in R80.20. CPAS works through the F2F path in R80.10 and R77.30. Now CPASXL is offered in SecureXL path in R80.20. This should lead to a higher performance. Check Point Active Streaming active streaming allow the changing of data and play the role of “man in the middle”. Several protocols uses CPAS, for example: Client Authentication, VoIP (SIP, Skinny/SCCP, H.323, etc.), Data Leak Prevention (DLP) blade, Security Servers processes, etc. I think it's not to be underestimated in tuning.
Slow path or Firewall path (F2F) - Packet flow when the SecureXL device is unable to process the packet. The packet is passed on to the CoreXL layer and then to one of the Core FW instances for full processing. This path also processes all packets when SecureXL is disabled.
New in R80.20:
Inline Streaming path, Medium Streaming path, Host path and Buffer path - Are new SecureXL paths used in conjunction with Falcon cards. They are described in more detail in the following article "R80.x Security Gateway Architecture (Acceleration Card Offloading) ".
PSL inline - “PSL inline” refers to the legacy Falcon Cards. This flow is deprecated and the statistics will be removed in R81.20 and JHFs. This stat will always show as 0 as well.
New in R81.20:
PSL pipeline - PSL pipeline refers to packets passing through Pipeline processing path and handled by PSL. A connection which is handled by more than one CPU (unlike in other paths in which a connection is handled by a dedicated CPU). Preparations for this infra were first introduced over R80.40.
The project is targeted for R81.20 (would be also ported to several JHFs), its main goal is to allow better utilization of the systems resources to tackle elephant flows scenarios in NGTP env. at first stage (content would be expanding over future releases)
Project is due to start EA phase soon (refer to article PSL inline vs pipeline).
Note to Falcon Cards: Theoretically and practically there are even more than these three paths. This has to do with the offloading of SAM and Falcon cards (new in R80.20) and with QXL (Quality of Service) and other SecureXL technologies. It's beyond the scope of this one.
Fast Accelerator - The Fast Acceleration feature (green) lets you define trusted connections to allow bypassing deep packet inspection on R80.20 JHF103 and above gateways. This feature significantly improves throughput for these trusted high volume connections and reduces CPU consumption.
The CLI of the gateway can be used to create rules that allow you to bypass the SecureXL PSLXL path to route all connections through the fast path.
| SecureXL chain modules (new in R80.20 and above) |
|---|
SecureXL has been significantly revised in R80.20. It now works in user space. This has also led to some changes in "fw monitor"
There are new fw monitor chain (SecureXL) objects that do not run in the virtual machine.
The new fw monitor chain modules (SecureXL) do not run in the virtual machine (vm).
SecureXL inbound (sxl_in) > Packet received in SecureXL from network
SecureXL inbound CT (sxl_ct) > Accelerated packets moved from inbound to outbound processing (post routing)
SecureXL outbound (sxl_out) > Accelerated packet starts outbound processing
SecureXL deliver (sxl_deliver) > SecureXL transmits accelerated packet
There are more new chain modules in R80.20
vpn before offload (vpn_in) > FW inbound preparing the tunnel for offloading the packet (along with the connection)
fw offload inbound (offload_in) > FW inbound that perform the offload
fw post VM inbound (post_vm) > Packet was not offloaded (slow path) - continue processing in FW inbound
| CoreXL |
|---|
CoreXL is a performance-enhancing technology for Security Gateways on multi-CPU-core processing platforms. CoreXL enhances Security Gateway performance by enabling the processing CPU cores to concurrently perform multiple tasks. CoreXL provides almost linear scalability of performance, according to the number of processing CPU cores on a single machine. The increase in performance is achieved without requiring any changes to management or to network topology.
On a Security Gateway with CoreXL enabled, the Firewall kernel is replicated multiple times. Each replicated copy, or FW instance, runs on one processing CPU core. These FW instances handle traffic concurrently, and each FW instance is a complete and independent FW inspection kernel. When CoreXL is enabled, all the FW kernel instances in the Security Gateway process traffic through the same interfaces and apply the same security policy.
R80.20 CoreXL does not support these Check Point features: Overlapping NAT, VPN Traditional Mode, 6in4 traffic - this traffic is always processed by the global CoreXL FW instance #0 (fw_worker_0) and more (see CoreXL Known Limitations).
Secure Network Distributor (SND) - Traffic entering network interface cards (NICs) is directed to a processing CPU core running the SND, which is responsible for:
- Processing incoming traffic from the network interfaces
- Securely accelerating authorized packets (if SecureXL is enabled)
- Distributing non-accelerated packets among Firewall kernel instances (SND maintains global dispatching table - which connection was assigned to which instance)
SND does not really touch any packet. The decision to stick to a particular FWK core is done at the first packet of connection on a very high level before anything else. Depending on SXL settings and in most of the cases, SXL can be offloading decryption calculations. However, in some other cases, such as with Route-Based VPN, it is done by FWK.
Firewall Instance (fw_worker) - On a Security Gateway with CoreXL enabled, the Firewall kernel is replicated multiple times. Each replicated copy, or Firewall Instance, runs on one CPU processing core. These FW instances handle traffic concurrently, and each FW instance is a complete and independent Firewall inspection kernel. When CoreXL is enabled, all the Firewall kernel instances on the Security Gateway process traffic through the same interfaces and apply the same security policy.
Dynamic Dispatcher - Rather than statically assigning new connections to a CoreXL FW instance based on packet's IP addresses and IP protocol (static hash function), the new dynamic assignment mechanism is based on the utilization of CPU cores, on which the CoreXL FW instances are running. The dynamic decision is made for first packets of connections, by assigning each of the CoreXL FW instances a rank, and selecting the CoreXL FW instance with the lowest rank. The rank
for each CoreXL FW instance is calculated according to its CPU utilization. The higher the CPU utilization, the higher the CoreXL FW instance's rank is, hence this CoreXL FW instance is less likely to be selected by the CoreXL SND. The CoreXL Dynamic Dispatcher allows for better load distribution and helps mitigate connectivity issues during traffic "peaks", as connections opened at a high rate that would have been assigned to the same CoreXL FW instance by a static decision, will now be distributed to several CoreXL FW instances.
Multi Queue - Network interfaces on a security gateway typically receive traffic at different throughputs; some are busier than others. At a low level, when a packet is received from the NIC, then a CPU core must be “interrupted” to the exclusion of all other processes, in order to receive the packet for processing. To avoid bottlenecks we allow multiple buffers, and therefore CPU cores, to be affined to an interface. Each affined buffer can “interrupt” its own CPU core allowing high volumes of inbound packets to be shared across multiple dispatchers.
When most of the traffic is accelerated by the SecureXL, the CPU load from the CoreXLSND instances can be very high, while the CPU load from the CoreXL FW instances can be very low. This is an inefficient utilization of CPU capacity. By default, the number of CPU cores allocated to CoreXL SND instances is limited by the number of network interfaces that handle the traffic. Because each interface has one traffic queue, only one CPU core can handle each traffic queue at a time. This means that each CoreXL SND instance can use only one CPU core at a time for each network interface. Check Point Multi-Queue lets you configure more than one traffic queue for each network interface. For each interface, you can use more than one CPU core (that runs CoreXL SND) for traffic acceleration. This balances the load efficiently between the CPU cores that run the CoreXL SND instances and the CPU cores that run CoreXL FW instances.
Priority Queues - In some situations a security gateway can be overwhelmed; in circumstances where traffic levels exceed the capabilities of the hardware, either legitimate traffic or from a DOS attack, it is vital that we can maintain management communications and continue to interact with dynamic routing neighbors. The Priority Queues functionality prioritizes control connections over data connections based on priority.
Affinity - Association of a particular network interface / FW kernel instance / daemon with a CPU core (either 'Automatic' (default), or 'Manual'). The default CoreXL interface affinity setting for all interfaces is 'Automatic' when SecureXL is installed and enabled. If SecureXL is enabled - the default affinities of all interfaces are 'Automatic' - the affinity for each interface is automatically reset every 60 seconds, and balanced between available CPU cores based on the current load. If SecureXL is disabled - the default affinities of all interfaces are with available CPU cores - those CPU cores that are not running a CoreXL FW instance or not defined as the affinity for a daemon.
The association of a particular interface with a specific processing CPU core is called the interface's affinity with that CPU core. This affinity causes the interface's traffic to be directed to that CPU core and the CoreXL SND to run on that CPU core. The association of a particular CoreXL FW instance with a specific CPU core is called the CoreXL FW instance's affinity with that CPU core. The association of a particular user space process with a specific CPU core is called the process's affinity with that CPU core. The default affinity setting for all interfaces is Automatic. Automatic affinity means that if SecureXL is enabled, the affinity for each interface is reset periodically and balanced between the available CPU cores. If SecureXL is disabled, the default affinities of all interfaces are with one available CPU core. In both cases, all processing CPU cores that run a CoreXL FW instance, or defined as the affinity for another user space process, is considered unavailable, and the affinity for interfaces is not set to those CPU cores.
The default affinity setting for all interfaces is Automatic. Automatic affinity means that if SecureXL is enabled, the affinity for each interface is reset periodically and balanced between the available CPU cores. If SecureXL is disabled, the default affinities of all interfaces are with one available CPU core. In both cases, all processing CPU cores that run a CoreXL FW instance, or defined as the affinity for another user space process, is considered unavailable, and the affinity for interfaces is not set to those CPU cores.
Passive Streaming Library (PSL) - IPS infrastructure, which transparently listens to TCP traffic as network packets, and rebuilds the TCP stream out of these packets. Passive Streaming can listen to all TCP traffic, but process only the data packets, which belong to a previously registered connection.
PXL - Technology name for combination of SecureXL and PSL.
The maximal number of possible CoreXL IPv4 FW in kernel mode instances:
| Version | Check Point Appliance | Open Server |
| R80.10 (Gaia 32-bit) | 16 | 16 |
| R80.10 (Gaia 64-bit) | 40 | 40 |
| R77.30 (Gaia 32-bit) | 16 | 16 |
| R77.30 (Gaia 64-bit) | 32 | 32 |
USFW - In kernel-mode FW, the maximum number of running cores is limited to 40 because of the Linux/Intel limitation of 2GB kernel memory, and because CoreXL architecture needs to load a large driver (~40MB) dozens of times (according to the CPU number, and up to 40 times). Newer platforms that contain more than 40 cores (e.g., 23900) are not fully utilized. Now it is possible to use more then 40 CoreXL cores in R80.10+ user mode firewall. For more informations see sk149973,
Management Core - New in R80.30+, you can also allocate a core for management traffic if you have 8 or more cores licensed, but this is not the default. R80.30+ feature for separating management from data traffic via Routing Separation and Resource Separation as described in sk138672.
| CoreXL vs. SND |
|---|
CPU cores are divided into two groups: SND and Firewall instances (CoreXL). Each group handles different tasks.
Tasks distribution:
| Task | R80.10 | R80.20+ |
| Soft IRQ processing | SND | SND |
| Multi-Queue | SND | SND |
| TPUT acceleration & Path determination | SND | Firewall |
| Accept templates matching (new connection) & offload to SecureXL | SND | Firewall |
| Nat templates matching (new connection) & offload to SecureXL | SND | Firewall |
| SecureXL/Acceleration path packet handling | SND | SND |
| Dynamic dispatcher | SND | SND |
| Fragmentation - IP fragments always sent F2F | SND | N/A |
| Fragmentation - Virtual reassembly of IP fragments (non-accelerated) | Firewall | Firewall |
| Fragmentation - Virtual reassembly of IP fragments (accelerated) | Firewall | SND |
| QoS - Traffic handling (non-accelerated) | Firewall | Firewall |
| QoS - Traffic handling (accelerated) | Firewall | SND |
| Rule base matching (non-accelerated) | Firewall | Firewall |
| Rule base matching (accelerated) | N/A | SND |
| PSLXL path packets handling | Firewall | Firewall |
| F2F path (+CPAS) | Firewall | Firewall |
| PSLXL, CPASXL paths | Firewall | Firewall |
| Priority queue (when enabled) | Firewall | Firewall |
| R80.40+ (automatically changes CoreXL, SNDˋs and the Multi-Queue) |
|---|
New in R80.40+
Support for automatic allocation of CoreXL SNDs and Firewall instances that does not require a Security Gateway reboot.
CoreXL and Multi-Queue: Improved out of the box experience - Security Gateway automatically changes the number of CoreXL SNDs and Firewall instances and the Multi-Queue configuration based on the current traffic load. Changing CoreXL split between FW workers and SND on the fly based on CPU utilization
Deciding keys:
The average utilization of CoreXL SNDs and FWs are regularly sampled. If either CoreXL SNDs or FWs utilization is higher than the other, perform an estimate of utilization post “migrating” a CPU to the other group. Note when SMT is on, change is doubled.
Supported on OS 3.10 (USFW/Kernel). Check Point appliances with 8 cores or more and VSX is currently a limitation. Supported on Cluster HA and VSLS is currently a limitation.
Flows:
If more SNDs are needed:
- Find least utilized CoreXL FW instance
- Stop dispatching new connections to the least utilized CoreXL FW instance
- Move the CoreXL FW instance to the CPU of next least utilized CoreXL FW instance
- Turn on a new MQ queue on the “evicted” CPU
Note: Eligible CoreXL SNDs must have a MQ queue ready
If more FWs (CoreXL) are needed:
- Choose the last “stopped” CoreXL FW instance
- Turn off MQ queue from the CPU it originally occupied
- Move the chosen CoreXL FW instance to the original CPU it occupied
- Start dispatching new connections to that CoreXL FW instance
Note: No more than the maximum number of FWs can be added
| FW Monitor Inspection Points |
|---|
There are new fw monitor inspection points (red) when a packet passes through a R80.20+ Security Gateway:
| Inspection point | Name of fw monitor inspection point | Relation to firewall VM | Available since version |
|---|---|---|---|
| i | Pre-Inbound | Before the inbound FireWall VM (for example, eth1:i) |
always |
| I | Post-Inbound | After the inbound FireWall VM (for example, eth1:I) |
always |
| id | Pre-Inbound VPN | Inbound before decrypt (for example, eth1:id) |
R80.20 |
| ID | Post-Inbound VPN | Inbound after decrypt (for example, eth1:ID) |
R80.20 |
| iq | Pre-Inbound QoS | Inbound before QoS (for example, eth1:iq) |
R80.20 |
| IQ | Post-Inbound QoS | Inbound after QoS (for example, eth1:IQ) |
R80.20 |
| o | Pre-Outbound | Before the outbound FireWall VM (for example, eth1:o) |
always |
| O | Post-Outbound | After the outbound FireWall VM (for example, eth1:O) |
always |
|
e oe |
Pre-Outbound VPN |
Outbound before encrypt (for example, (for example, |
R80.10 R80.20 |
|
E OE |
Post-Outbound VPN |
Outbound after encrypt (for example, (for example, |
R80.10 R80.20 |
| oq | Pre-Outbound QoS | Outbound before QoS (for example, eth1:oq) |
R80.20 |
| OQ | Post-Outbound QoS | Outbound after QoS (for example, eth1:OQ) |
R80.20 |
The "Pre-Encrypt" fw monitor inspection point (e) and the "Post-Encrypt" fw monitor inspection point (E) are new in R80 and above.
Note: It's true, they only exist on the outbound side for encrypting packets not for decrypting packets on inbound side.
New in R80.20+:
In Firewall kernel (now also SecureXL), each kernel is associated with a key witch specifies the type of traffic applicable to the chain modul.
# fw ctl chain
| Key | Function |
|---|---|
| ffffffff | all packets |
| 00000001 | stateful mode |
| 00000002 | wire mode |
| 00000003 | all packets |
| 00000000 | SecureXL offloading |
| Content Inspection |
|---|
For more details see article: R80.x Security Gateway Architecture (Content Inspection)
Content inspection is a very complicated process, it is only shown in the example for R80.10 IPS and R80.10 App Classifier. It is also possible for other services. Please refer to the corresponding SK's. In principle, all content is processed via the Context Management Infrastructure (CMI) and CMI loader and forwarded to the corresponding daemon.
Session-based processing enforces advanced access control and threat detection and prevention capabilities. To do this we assemble packets into a stream, parse the stream for relevant contexts and then security modules inspect the content. When possible, a common pattern matcher does simultaneous inspection of the content for multiple security modules. In multi-core systems this processing is distributed amongst the cores to provide near linear scalability on each additional core.
Security modules use a local cache to detect known threats. This local cache is backed up with real-time lookups of an cloud service. The result of cloud lookups are then cached in the kernel for subsequent lookups. Cloud assist also enhances unknown threat detection and prevention. In particular a file whose signature is not known in a local cache is sent to our cloud service for processing where compute, disk and memory are virtually unlimited. Our sandboxing technology, SandBlast Threat Emulation, identifies threats in their infancy before malware has an opportunity to deploy and evade detection. Newly discovered threats are sent to the cloud database to protect other Check Point connected gateways and devices. When possible, active content is removed from files which are then sent on to the user while the emulation is done.
Passive Streaming Library (PSL) -Packets may arrive out of order or may be legitimate retransmissions of packets that have not yet received an acknowledgment. In some cases a retransmission may also be a deliberate attempt to evade IPS detection by sending the malicious payload in the retransmission. Security Gateway ensures that only valid packets are allowed to proceed to destinations. It does this with Passive Streaming Library (PSL) technology.
- PSL is an infrastructure layer, which provides stream reassembly for TCP connections.
- The gateway makes sure that TCP data seen by the destination system is the same as seen by code above PSL.
This layer handles packet reordering, congestion handling and is responsible for various security aspects of the TCP layer such as handling payload overlaps, some DoS attacks and others. - The PSL layer is capable of receiving packets from the firewall chain and from SecureXL module.
- The PSL layer serves as a middleman between the various security applications and the network packets. It provides the applications with a coherent stream of data to work with, free of various network problems or attacks
- The PSL infrastructure is wrapped with well defined APIs called the Unified Streaming APIs which are used by the applications to register and access streamed data.
Protocol Parsers -
The Protocol Parsers main functions are to ensure compliance to well-defined protocol standards, detect anomalies if any exist, and assemble the data for further inspection by other components of the IPS engine. They include HTTP, SMTP, DNS, IMAP, Citrix, and many others. In a way, protocol parsers are the heart of the IPS system. They register themselves with the streaming engine (usually PSL), get the streamed data, and dissect the protocol.
The protocol parsers can analyze the protocols on both Client to Server (C2S) and Server to Client (S2C) directions. The outcome of the protocol parsers are contexts. A context is a well defined part of the protocol, on which further security analysis can be made. Examples of such contexts are HTTP URL, FTP command, FTP file name, HTTP response, and certain files.
Context Management Infrastructure (CMI) and Protections - The Context Management Infrastructure (CMI) is the "brain" of the content inspection. It coordinates different components, decides which protections should run on a certain packet, decides the final action to be performed on the packet and issues an event log.
CMI separates parsers and protections. Protection is a set of signatures or/and handlers, where
- Signature - a malicious pattern that is searched for
- Handler - INSPECT code that performs more complex inspection
CMI is a way to connect and manage parsers and protections. Since they are separated, protections can be added in updates, while performance does not depend on the number of active protections. Protections are usually written per protocol contexts - they get the data from the contexts and validate it against relevant signatures Based on the IPS policy, the CMI determines which protections should be activated on every context discovered by a protocol parser. If policy dictates that no protections should run, then the relevant parsers on this traffic are bypassed in order to improve performance and reduce potential false positives. When a protection is activated, it can decide whether the given packet or context is OK or not. It does not decide what to do with this packet. The CMI is responsible for the final action to be performed on the packet, given several considerations.
The considerations include:
- Activation status of the protection (Prevent, Detect, Inactive)
- Exceptions either on traffic or on protection
- Bypass mode status (the software fail open capability)
- Troubleshooting mode status
- Are we protecting the internal network only or all traffic
CMI Loader - collects signatures from multiple sources (e.g. IPS, Application Control,...) and compiles them together into unified Pattern Matchers (PM) (one for each context - such as URL, Host header etc.).
Pattern Matcher -The Pattern Matcher is a fundamental engine within the new enforcement architecture.
- Pattern Matcher quickly identifies harmless packets, common signatures inmalicious packets, and does a second level analysis to reduce false positives.
- Pattern Matcher engine provides the ability to find regular expressions on a stream of data using a two tiered inspection process.
UP Manager - The UP Manager controls all interactions of the components and interfaces with the Context Management Infrastructure (CMI) Loader, the traffic director of the CMI. The UP Manager also has a list of Classifiers that have registered for “first packets” and uses a bitmap to instruct the UP Classifier to execute these Classifier Apps to run on the packet. The “first packets” arrive directly from the CMI. Parsing of the protocol and streaming are not needed in this stage of the connection. For “first packets” the UP Manager executes the rule base.
Classifier - When the “first packet” rule base check is complete Classifiers initiate streaming for subsequent packets in the session. The “first packet” rule base check identifies a list of rules that possibly may match and a list of classifier objects (CLOBs) that are required to complete the rule base matching process. The Classifier reads this list and generates the required CLOBs to complete the rule base matching. Each Classifier App executes on the packet and tells the result of the CLOB to the UP Manager. The CMI then tells the Protocol Parser to enable streaming.
In some cases Classifier Apps do not require streaming, e.g. the first packet information is sufficient. Then the rule base decision can be done on the first packet.
- Dynamic Objects
- Domain Objects
- Only the firewall is enabled
On subsequent packets the Classifier can be contacted directly from the CMI using the CMI Loader infrastructure, e.g. when the Pattern Matcher has found a match it informs the CMI it has found application xyz. The CMI Loader passes this information to the Classifier. The Classifier runs the Classification Apps to generate CLOBs required for Application Control and sends the CLOBs to the Observer.
Observer - The Observer decides if enough information is known to publish a CLOB to the security policy. CLOBs are observed in the context of their transaction and the connection that the transaction belongs to. The Observer may request more CLOBs for a dedicated packet from the Classifier or decides that it has sufficient information about the packet to execute the rule base on the CLOB, e.g. if a file type is needed for Content Awareness and the gateway hasn’t yet received the S2C response containing the file. Executing the rule base on a CLOB is called “publishing a CLOB”. The Observer may wait to receive more CLOBs that belong to the same transaction before publishing the CLOBs.
Security Policy - The Security Policy receives the CLOB published by the Observer. The CLOB includes a description of the Blade it belongs to so that matching can be performed on a column basis. The security policy saves the current state on the transaction Handle; either to continue the inspection or final match.
The first packets are received directly from the UP Manager. Subsequent packets are received by the rule base from the Observer.
Handle - Each connection may consist of several transactions. Each transaction has a Handle. Each Handle contains a list of published CLOBs. The Handle holds the state of the security policy matching process. The Handle infrastructure component stores the rule base matching state related information.
Subsequent Packets - Subsequent packets are handled by the streaming engine. The streaming engine notifies the Classifier to perform the classification. The Classifier will notify the UP Manager about the performed classification and pass the CLOBs to the Observer. The CLOBs will then be received by the Observer that will need to wait for information from the CMI. The CMI sends the information describing the result of the Protocol Parser and the Pattern Matcher to the Classifier. The Classifier informs the UP Manager and sends the CLOB to the Observer. The UP Manager then instructs the Observer to publish the CLOBs to the Rule Base.
The Rule Base is executed on the CLOBs and the result is communicated to the UP Manager. The CLOBs and related Rule Base state are stored in the Handle. The UP Manager provides the result of the rule base check to the CMI that then decides to allow or to drop the connection. The CMI generates a log message and instructs the streaming engine to forward the packets to the outbound interface.
Content Awareness (CTNT) - is a new blade introduced in R80.10 as part of the new Unified Access Control Policy. Using Content Awareness blade as part of Firewall policy allows the administrator to enforce the Security Policy based on the content of the traffic by identifying files and its content. Content Awareness restricts the Data Types that users can upload or download.
Content Awareness can be used together with Application Control to enforce more interesting scenarios (e.g. identify which files are uploaded to DropBox).
| Definitions |
|---|
Performance Pack is a software acceleration product installed on Security Gateways. Performance Pack uses SecureXL technology and other innovative network acceleration techniques to deliver wire-speed performance for Security Gateways. SecureXL is implemented either in software, or in hardware (SAM cards on Check Point 21000 appliances; ADP cards on IP Series appliances).
Affinity - Association of a particular network interface with a CPU core (either 'Automatic' (default), or 'Static' / 'Manual'). Interfaces are bound to CPU cores via SMP IRQ affinity settings (refer to sk61962 - SMP IRQ Affinity on Check Point Security Gateway). Note: on X-Series chassis, SIM Affinity must be set to Static mode (refer to sk99490).
FWACCEL - FireWall Accelerator (acceleration feature).
SIM - SecureXL Implementation Module (acceleration device).
Connection offload - Firewall kernel passes the relevant information about the connection from Firewall Connections Table to SecureXL Connections Table.
Note: In ClusterXL High Availability, the connections are not offloaded to SecureXL on Standby member.
Connection notification - SecureXL passes the relevant information about the accelerated connection from SecureXL Connections Table to Firewall Connections Table.
Accept Template - Feature that accelerates the speed, at which a connection is established by matching a new connection to a set of attributes. When a new connection matches the Accept Template, subsequent connections are established without performing a rule match and therefore are accelerated. Accept Templates are generated from active connections according to policy rules. Currently, Accept Template acceleration is performed only on connections with the same destination port (using wildcards for source ports).
Note: Size of SecureXL Connections Templates table (cphwd_tmpl, id 8111) is limited to 1/4 of the size of Firewall Connections Table (connections, id 8158).
Drop Template - Feature that accelerates the speed, at which a connection is dropped by matching a new connection to a set of attributes. When a new connection matches the Drop Template, subsequent connections are dropped without performing a rule match and therefore are accelerated. Currently, Drop Template acceleration is performed only on connections with the same destination port (does not use wildcards for source ports). Drop Templates are generated from policy rules by special algorithm:
- Analyze the rulebase
- Produce mutually exclusive ranges
- Offload the ranges to SecureXL
- Once a packet is dropped, offload a Drop Template
- All subsequent packets matching that range will be dropped by SecureXL
Accelerated path - Packet flow when the packet is completely handled by the SecureXL device. It is processed and forwarded to the network.
Medium path (PXL) - Packet flow when the packet is handled by the SecureXL device, except for IPS (some protections) / VPN (in some configurations) / Application Control / Content Awareness / Anti-Virus / Anti-Bot / HTTPS Inspection / Proxy mode / Mobile Access / VoIP / Web Portals. The CoreXL layer passes the packet to one of the CoreXL FW instances to perform the processing (even when CoreXL is disabled, the CoreXL infrastructure is used by SecureXL device to send the packet to the single FW instance that still functions).
Firewall path / Slow path (F2F) - Packet flow when the SecureXL device is unable to process the packet (refer to sk32578 - SecureXL Mechanism). The packet is passed on to the CoreXL layer and then to one of the Core FW instances for full processing. This path also processes all packets when SecureXL is disabled.
Active Streaming (CPAS) - Technology that sends streams of data to be inspected in the kernel, since more than a single packet at a time is needed in order to understand the application that is running (such as HTTP data). Active Streaming is Read- and Write-enabled, and works as a transparent proxy. Connections that pass through Active Streaming can not be accelerated by SecureXL.
Passive Streaming - Technology that sends streams of data to be inspected in the kernel, since more than a single packet at a time is needed in order to understand the application that is running (such as HTTP data). Passive Streaming is Read-only and it cannot hold packets, but the connections are accelerated by SecureXL.
Passive Streaming Library (PSL) - IPS infrastructure, which transparently listens to TCP traffic as network packets, and rebuilds the TCP stream out of these packets. Passive Streaming can listen to all TCP traffic, but process only the data packets, which belong to a previously registered connection. For more details, refer to sk95193 - ATRG: IPS.
PXL - Technology name for combination of SecureXL and PSL.
QXL - Technology name for combination of SecureXL and QoS (R77.10 and higher).
F2F / F2Fed - Packets that can not be accelerated by SecureXL (refer to sk32578 - SecureXL Mechanism) are Forwarded to Firewall.
F2P - Forward to PSL/Applications. Feature that allows to perform the PSL processing on the CPU cores, which are dedicated to the Firewall.
F2V - -Forward to VM. Packet which arrive to FW inbound and is reinjected back to SecureXL for further processing.
SAM card - Security Acceleration Module card (Acceleration Ready card). Connections that use SAM card, are accelerated by SecureXL and are processed by the SAM card's CPU instead of the main CPU (refer to 21000 Appliance Security Acceleration Module Getting Started Guide).
ADP card - Accelerated Data Path card. Connections that use ADP card, are accelerated by SecureXL and are processed by network processors (NP) instead of the main CPU (refer to sk60508 - How to Configure ADP & SecureXL on IPSO).
IRQ Swizzling - Traditionally, in a PCIe bus, all PCIe ports are mapped to one interrupt. Swizzling allows the PCIe slots to be balanced across four interrupts instead of one (enabling IRQ Swizzling requires a BIOS update).
| References |
|---|
SecureKnowledge: SecureXL
SecureKnowledge: NAT Templates
SecureKnowledge: VPN Core
SecureKnowledge: CoreXL
SecureKnowledge: CoreXL Dynamic Dispatcher in R77.30 / R80.10 and above
SecureKnowledge: Application Control
SecureKnowledge: URL Filtering
SecureKnowledge: Content Awareness (CTNT)
SecureKnowledge: IPS
SecureKnowledge: Anti-Bot and Anti-Virus
SecureKnowledge: Threat Emulation
SecureKnowledge: Best Practices - Security Gateway Performance
SecureKnowledge: MultiCore Support for IPsec VPN in R80.10 and above
SecureKnowledge: SecureXL Fast Accelerator (fw fast_accel) for R80.20 and above.
Download Center: R80.10 Next Generation Threat Prevention Platforms
Download Center: R77 Security Gateway Packet Flow
Download Center: R77 Security Gateway Architecture
Support Center: Check Point Security Gateway Architecture and Packet Flow
Checkmates: Check Point Threat Prevention Packet Flow and Architecture
Checkmates: fw monitor inspection point e or E
Infinity NGTP architecture
Security Gateway Packet Flow and Acceleration - with Diagrams
R80.x Security Gateway Architecture (Content Inspection)
| Questions and Answers |
|---|
Q: Why this diagram with SecureXL and CoreXL?
A: I dared to map both worlds of CoreXL and SecureXL in a diangram. This is only possible to a limited extent, as these are different technologies. It's really an impossible mission. Why!
- CoreXL is a mechanism to assign, balance and manage CPU cores. CoreXL SND makes a decision to "stick" particular connection going through to a specific FWK instance.
- SecureXL certain connections could avoid FW path partially (packet acceleration) or completely (acceleration with templates)
Q: Why both technologies in one flowchart?
A: There are both technologies that play hand in hand. The two illustrations become problematic, e.g. in the Medium Path.
Q: Why in the Medium Path?
A: Here, the packet-oriented part (SecureXL) cannot be mapped with the connection-based part (CoreXL). Therefore, the following note from an new Check Point article from Valeri Loukine (Security Gateway Packet Flow and Acceleration - with Diagrams - 08-07-2018) and original article from Moti Sagey (Check Point Threat Prevention Packet Flow and Architecture - 04-25-2017) :
When Medium Path is available, TCP handshake is fully accelerated with SecureXL. Rulebase match is achieved for the first packet through an existing connection acceleration template. SYN-ACK and ACK packets are also fully accelerated. However, once data starts flowing, to stream it for Content Inspection, the packets will be now handled by a FWK instance. Any packets containing data will be sent to FWK for data extraction to build the data stream. RST, FIN and FIN-ACK packets once again are only handled by SecureXL as they do not contain any data that needs to be streamed.
Q: What is the point of this article?
A: To create an overview of both worlds with regard to the following innovations in R80.x:
- new fw monitor inspection points in R80 (e and E)
- new MultiCore VPN with dispatcher
- new UP Manager in R80
Q: Why is there the designation "Logical Packet Flow"?
A: Since the logical flow in the overview differs from the real flow. For example, the medium path is only a single-logical representation of the real path. This was necessary to map all three paths (F2F, SXL, PXL) in one image. That is why the name "Logical Packet Flow".
Q: What's the next step?
A: I'm thinking about how to make the overview even better.
Q: Wording?
A: It was important for me that the right terms from Check Point were used. Many documents on the Internet use the terms incorrectly. Therefore I am grateful to everyone who still finds wording errors here.
Q: What's the GA version?
A: This version has approved by Check Point representative, and we agreed that this should be the final version.
| Versions |
|---|
Version R81.20:
2.0a - EA info PSL pipline - The project is targeted for R81.20 (24.08.2021)
Version R81.10:
1.9a - Now with R81.10 upgrade (29.07.2021)
1.9b - Fix error in "fw ctl chain" (30.07.2021)
Version R81:
1.8a - Bug fix R80.20+ packet flow (28.03.2021)
Version R80.40:
1.7c - Article with new pictures and text revised for R80.40 (07.09.2020)
1.7b - attention note to the flowchart (24.04.2020)
1.7a - after long discussions with Val_Loukine @, the R&D version has been changed back to an approved version 1.4d (24.04.2020)
1.6a - new R80.30+ flowchart with SK104468 and SK156672 (13.01.2020)
Version R80.30:
1.5a - added new R80.30+ flowchart picture and pdf, add QoS path in flowchart, added R80.30 new path names (16.12.2019)
1.4a - update - automatically changes the number of CoreXL SNDs and Firewall instances and the Multi-Queue (02.09.2019)
1.4b - update - http/2 support (03.09.2019)
1.4c - update - Host path, Buffer path, Inline path (04.09.2019)
1.4c - update - now eight firewall paths are possible (14.09.2019)
1.4d - R&D guys checks the logical packet flowchart for R80.20 and gives green lights (05.11.2019)
1.4e - add R80.20 JHF103 fast accelerator feature (15.11.2019)
1.4f - update flowchart with "Fast Accel" (16.11.2019)
1.4g - update R80.40 EA infos (27.11.2019)
1.4h - new table with R80.10/ R80.20/ R80.30/ R80.40 paths (15.12.2019)
1.3a - update R80.30 managment core ( 25.07.2019 )
1.3b - update R80.30 https SNI (28.07.2019)
1.3c - update R80.20 new async flowchart (15.08.2019)
1.3d - update R80.20 packet reinjection (20.08.2019)
Version R80.20:
1.2a - article update to R80.20 (16.11.2018)
1.2b - update inspection points id, iD and more (19.11.2018)
1.2c - update maximal number of CoreXL IPv4 FW instances (20.11.2018)
1.2d - update R80.20 new functions (05.11.2018)
1.2e - bug fix (06.01.2019)
1.2f - update fw monitor inspection points ie/ IE (23.01.2019)
1.2g - update sk 151114 VPN+SecureXL (20.04.2019)
1.2h - update fw monitor inspection points (10.07.2019)
Version R80.10:
1.1b - final GA version (08.08.2018)
1.1c - change words to new R80 terms (08.08.2018)
1.1d - correct a mistak with SXL and "Accelerated path" (09.08.2018)
1.1e - bug fixed (29.08.2018)
1.1f - QoS (24.09.2018)
1.1g - correct a mistak in pdf (26.09.2018)
1.1h - add PSLXL and CPASXL path in R80.20 (27.09.2018)
1.1i - add "Medium Streaming Path" and "Inline Streaming Path" in R80.20 (28.09.2018)
1.1j - add "new R80.20 chain modules" (22.10.2018)
1.1k - bug fix chain modules (04.11.2018)
1.1l - add "chaptures" (10.11.2018)
1.1m - add R80.20 fw monitor inspection points "oe" and "OE" (17.12.2018)
R80.10 EA Version:
1.0a - final version (28.07.2018)
1.0c - change colors (28.07.2018)
1.0d - add content inspection text (29.07.2018)
1.0e - add content inspection drawing (29.07.2018)
1.0f - update links (29.07.2018)
1.0g - update content inspection drawing flows and action (30.07.2018)
1.0h - change SecureXL flow (30.07.2018)
1.0i - correct SecureXL packet flow (01.08.2018)
1.0j - correct SecureXL names and correct "fw monitor inspection points" (02.08.2018)
1.0k - add new article "Security Gateway Packet Flow and Acceleration - with Diagrams" from 06.08.2018 to "References and links" (06.08.2018)
1.0l - add "Questions and Answers" (07.08.2018)
1.0m - R&D guys checks the logical packet flowchart for R80.10 and gives green lights (08.08.2018)
➜ CCSM Elite, CCME, CCTE
- Tags:
- accelerated path
- accept template
- affinity
- anti-spoofing
- antibot
- antivirus
- appli
- applicationcontrol
- av
- buffer path
- chain
- chain inspection point
- checkmates
- classifier
- cmi
- cmi loader
- connection setup
- content awareness
- context management infrastructure
- corexl
- correction path
- cpasxl
- ctnt
- decryption
- domain objects
- drop template
- dynamic dispatcher
- dynamic objects
- encryption
- f2f
- f2v
- f2w
- fast path
- firewall instance
- firewall path
- fw monitor inspection points
- fw offload inbound
- fw post vm inbound
- fw_worker
- gateway architecture
- hos*
- host pa*
- host pat*
- host path
- https
- inbound
- inline
- inline path
- inline streaming path
- inspect
- ips
- logical packet flow
- medium path
- medium streaming path
- multi queue
- nat
- nat template
- observer
- offload_in
- outbound
- package processing
- packet flow
- passive streaming
- passive streaming library
- pat
- pattern matcher
- performance
- performance tuning
- policy
- port address translation
- post-encrypt
- post_vm
- pre-encrypt
- protections
- protocol parsers
- psl
- pslxl
- pxl
- qos
- r80.10
- r80.20
- r80.40
- r80.x
- reinject
- secure network distributor
- securexl deliver
- securexl inbound
- securexl inbound ct
- securexl outbound
- security policy
- sexurexl
- slow path
- snd
- stateful inspection
- subsequent packet
- sxl
- sxl_ct
- sxl_deliver
- sxl_in
- sxl_out
- ted
- up manager
162 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great flowchart.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko Ankenbrand,there are still a couple of issues with this chart.
1. You have market a CoreXL section there. In fact, you cannot really put CoreXL as a part of the packet flow. It is a system of balancing sticky decisions per connection, not per packet, and that can't be visualized as such.
2. You are keeping Medium Path something independent while it is just a continuation of SecureXL flow into Content Inspection block.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
this is a very straightforward flowchart and a very good reference list.
Thanks,
Max
Max
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great work ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Questions and Answers:
Q: Why this diagram with SecureXL and CoreXL?
A: I dared to map both worlds of CoreXL and SecureXL in a diangram. This is only possible to a limited extent, as these are different technologies. It's really an impossible mission. Why!
- CoreXL is a mechanism to assign, balance and manage CPU cores. CoreXL SND makes a decision to "stick" particular connection going through to a specific FWK instance.
- SecureXL certain connections could avoid FW path partially (packet acceleration) or completely (acceleration with templates)
Q: Why both technologies in one flowchart?
A: There are both technologies that play hand in hand. The two illustrations become problematic, e.g. in the Medium Path.
Q: Why in the Medium Path?
A: Here, the packet-oriented part (SecureXL) cannot be mapped with the connection-based part (CoreXL). Therefore, the following note from an new Check Point article from Valeri Loukine (Security Gateway Packet Flow and Acceleration - with Diagrams - 08-07-2018) and original article from Moti Sagey (Check Point Threat Prevention Packet Flow and Architecture - 04-25-2017) :
When Medium Path is available, TCP handshake is fully accelerated with SecureXL. Rulebase match is achieved for the first packet through an existing connection acceleration template. SYN-ACK and ACK packets are also fully accelerated. However, once data starts flowing, to stream it for Content Inspection, the packets will be now handled by a FWK instance. Any packets containing data will be sent to FWK for data extraction to build the data stream. RST, FIN and FIN-ACK packets once again are only handled by SecureXL as they do not contain any data that needs to be streamed.
Q: What is the point of this article?
A: To create an overview of both worlds with regard to the following innovations in R80.x:
- new fw monitor inspection points in R80 (e and E)
- new MultiCore VPN with dispatcher
- new UP Manager in R80
Q: Why is there the designation "Logical Packet Flow"?
A: Since the logical flow in the overview differs from the real flow. For example, the medium path is only a single-logical representation of the real path. This was necessary to map all three paths (F2F, SXL, PXL) in one image. That is why the name "Logical Packet Flow".
Q: What's the next step?
A: I'm thinking about how to make the overview even better.
Q: Where does the information come from?
A: From References and links:
SecureKnowledge: NAT Templates
SecureKnowledge: CoreXL Dynamic Dispatcher in R77.30 / R80.10 and above
SecureKnowledge: Application Control
SecureKnowledge: URL Filtering
SecureKnowledge: Content Awareness (CTNT)
SecureKnowledge: Anti-Bot and Anti-Virus
SecureKnowledge: Threat Emulation
SecureKnowledge: Best Practices - Security Gateway Performance
Download Center: R80.10 Next Generation Threat Prevention Platforms
Download Center: R77 Security Gateway Packet Flow
Download Center: R77 Security Gateway Architecture
Support Center: Check Point Security Gateway Architecture and Packet Flow
Checkmates: Check Point Threat Prevention Packet Flow and Architecture
Checkmates: fw monitor inspection point e or E
Checkmates: Infinity NGTP architecture
Security Gateway Packet Flow and Acceleration - with Diagrams
Please help me to improve the flowchart. Therefore I am grateful for any Feefback.
Regards,
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, this is great stuff 🙂 I might be way off here - but would it be an idea to bring in routing ? When are the routing table checked related to nat / encrypt f.ex?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's a good question, DNAT/SNAT packet processing hook in relation to firewall rulebase evaluation must be in this diagram. My understanding is that in currently supported R80 versions, DNAT occurs before security rule evaluation, but only if "Perform Destination Translation on Client Side" is enabled in the Global Properties->Network Address Translation section (which is the default value).
What is also a good question is whether NAT table overrides the routing table when it comes to egress interface selection like it does in Cisco ASA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No the diagram is correct. On the first packet of a new connection, the Firewall rule base (Network Policy Layer) is consulted first so any address matching there must be for the original/pre-NAT addresses. If using the automatic NAT setup technique this detail is somewhat hidden, since a single object with NAT set represents both the original and NAT address in the single object used in the firewall policy rule. If the packet is accepted, next the NAT policy is checked and how NAT will be performed is set for the life of that connection and cannot be changed. If the destination IP address is subject to NAT the actual destination IP NAT operation is also performed (with the default "Translate destination on client side" checked). Everything discussed above happens between i and I in the F2F path. If the packet is dropped by the firewall policy the NAT rulebase is never consulted because it simply doesn't matter, and this is why you don't see any NAT rules referenced in a drop log.
The NAT operation on the source address (if applicable) happens between o and O.
NAT does not really override the routing table, most of the time the only thing IP routing considers is the destination IP address, so if the destination IP address is subject to NAT we want to perform that NAT operation between i and I prior to routing by IP.
There are exceptions to this with PBR and such but the above is how most traffic gets handled.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Both NAT and rulebase enforcement are happening at the same place. Agree with @Timothy_Hall , to that extent the diagram os okay.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko,
good that both components are shown (SecureXL and CoreXL) and a great reference list to other article.
Thanks,
Ali
Ali
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Heiko Ankenbrand I would like to reiterate once more that CoreXL markings on the diagram are problematic. I suggest you remove CoreXL notion from the diagram
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Valeri
I think this topic will trigger a fundamental discussion here and we have discussed this in the background with private messages over the last few days. I think we should open an article here to avoid confusing all users.
New discussion articel:
How does the Medium Path (PXL) and Content Inspection work with R80
To my point:
There is a SK98737 ( CoreXL ) describing exactly my picture. I will illustrate this with a picture:
| my flowchart | SK98737 - topic 5 |
|---|
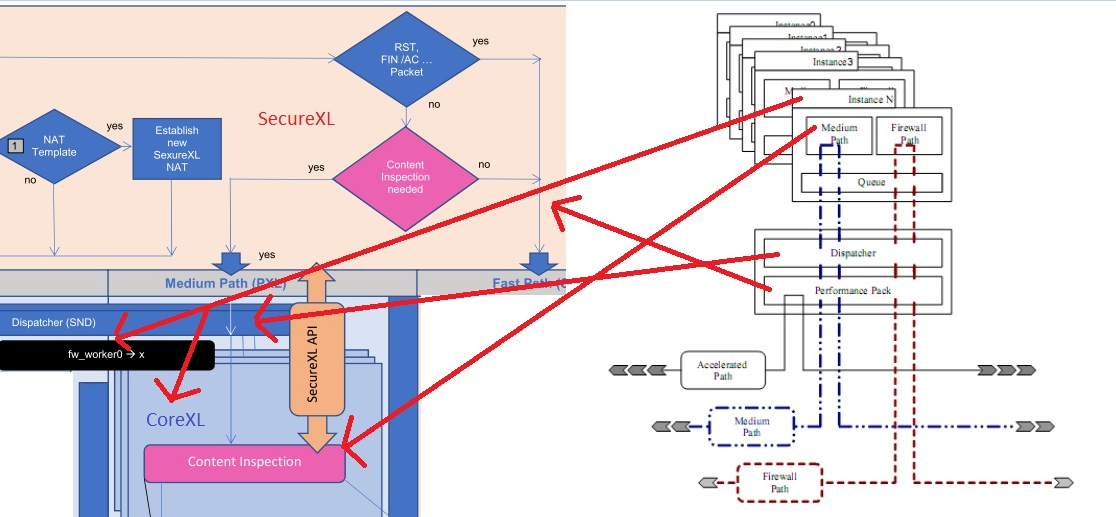
Here are the original text from SK:
[5] Packet flow
When SecureXL is enabled, a packet enters the Security Gateway and first reaches the SecureXL device. The packet will be handled in one of three ways:
- Accelerated path - The packet is completely handled by the SecureXL device. It is processed and forwarded to the network.
- Medium path (PXL) - Packet flow when the packet is handled by the SecureXL device, except for IPS (some protections) / VPN (in some configurations) / Application Control / Content Awareness / Anti-Virus / Anti-Bot / HTTPS Inspection / Proxy mode / Mobile Access / VoIP / Web Portals. The CoreXL layer passes the packet to one of the CoreXL FW instances to perform the processing.
This path is available only when CoreXL is enabled. - Firewall path / Slow path - The SecureXL device is unable to process the packet (refer to sk32578 (SecureXL Mechanism)). The packet is passed on to the CoreXL layer and then to one of the CoreXL FW instances for full processing.
This path also processes all packets when SecureXL is disabled.
If you still think this is not possible, the Check Point article would be wrong in your support center since 01-Jul-2014 and I think strongly that this article is right.
Let's all discuss this here in peace:
How does the Medium Path (PXL) and Content Inspection work with R80
Regards
Heiko
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do agree with you, this is a fundamental discussion.
My issue with your diagram is that you put Medium Path as something independent and different from SecureXL Path. It is not.
In essence, the difference between Fast Path and Medium Path is about whether Content Inspection has to be performed or not. If the answer is yes, after crossing SecureXL packets goes to a FWK instance to form a data stream for Content Inspection. If the answer no, it is fully accelerated, hence FW kernel is fully bypassed. So, in other words, both SecureXL and FW kernel are active in case of Medium Path.
I have made three different diagrams in Security Gateway Packet Flow and Acceleration - with Diagrams trying to make this point as clear as possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You say: If you still think this is not possible, the Check Point article would be wrong in your support center since 01-Jul-2014 and I think strongly that this article is right.
Well, the article is right and so am I. There is no contradiction between the diagram you have taken from the article and my statement. It is, in fact, very simple.
Medium path can be shown separately if you chart it per connection and not per packet. The SK you are quoiting does just that, it is a high level diagram for handling connections, not individual packets.
Your diagram, on the other hand, is for packet handling. The only way to show any Path, FW, Medium or Fast on a single packet flow diagram is to chart which modules (SecureXL, FW kernel, Content Inspection) are handling a packet in any particular case. As done here Security Gateway Packet Flow and Acceleration - with Diagrams
The argument we are having is not even about understanding of technology. Your understanding is all right. The support article is correct. I am correct and I also understand that you are too. 🙂
It is about presenting this understanding in graphics. This representation also has to be correct, and this is what I am aiming to.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Heiko Ankenbrand I also have other corrections to your diagram. I will send you a personal message, as those require some offline discussions. Let's stop doing it here till the issues are fixed.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Heiko Ankenbrand great work!! It simply warms my heart to the see the level of your dedication to this community (without getting a salary in return ;)) I think it's a great opportunity on behalf of the CheckMates team Amit Sharon Dameon Welch Abernathy myself and our "new Comer" Valeri Loukine to publically thank you for your great CONSISTENT contribution to CheckMates and keeping it constructive and civilized 🙂

See you in Israel soon 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One last comment here.
I will create a revised version with Valeri Loukine from Check Point in the next days.
Regards,
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Special thanks to Valeri Loukine who supported me here technically in the background.
And special thanks to CheckMates team Moti Sagey, Amit Sharon, Dameon Welch Abernathy who have executed organizational processes in the background.
Regards,
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Heiko Ankenbrand for your hard work and collaboration. We appreciate it, very well done indeed!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Which is already done 🙂
Now the diagram is perfect, thanks again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As the packet flow shows, there is no Fast path (SXL). It's called Accelerated path. This is important because Check Point puts attention to these little details in it's exams. Please update your diagram.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very good point, Danny Jung
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, just a note. There is a typo: UP Manger - at the beginning of the document
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The background story to this article:
It has been a lot of work over the last two weeks to create this flowchart and the text and I have used a lot of my holiday time for it. I also received very good support from Check Point (Valeri Loukine ). I have discussed a lot with Valeri in the background to improve this article. I was also able to gain some new experiences about the function of the firewall R80.
I would be happy to help you all with this Flowchart.
But now I have to take care of my family.
I think we should now have a final version that Check Point is satisfied with.
Thanks to all involved,
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are addicted ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 20 | |
| 18 | |
| 12 | |
| 11 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 05:00 PM (CEST)
SASE Masters: Deploying Harmony SASE for a 6,000-Strong Workforce in a Single WeekendAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center