- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Mastering Compliance
Unveiling the power of Compliance Blade
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
May the 4th (+4)
Navigating Paradigm Shifts in Cyber
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Management
- :
- ckpSSL ssl lib error
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ckpSSL ssl lib error
Hi all,
I was wondering whether anybody has either seen the error below before or know how to fix it.
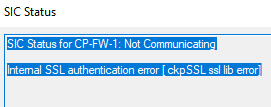
I have already consulted sk97691 but it doesn't seem to cover the error above.
Many thanks in advance.
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A couple questions:
- What version of Management is this? Assuming it was upgraded at some point, what version from?
- What version of Gateway are you attempting to manage?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for responding Dameon.
Both questions are valid.
The Management version is 80.20 while the gateway's version is R70.
It goes without saying that the above deployment is not recommended by any means but my team and I were interested in figuring out whether such an implementation would be feasible. The work I've done so far took place in a virtualized environment. Please see the steps taken below:
- Connectivity between the server and the gateway is successful.
- Time is set the same on both endpoints.
- License has been installed on both machines.
- The gateway has been configured with the right settings as far as I can see:
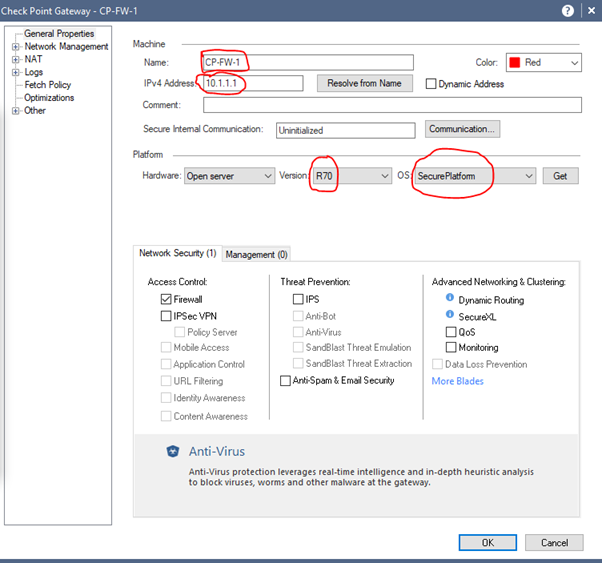
- The gateway’s initial policy has been uninstalled (with fw unloadlocal).
- The gateway is listening on port 18191 (with netstat -nap | grep 18191).
- Captured SIC traffic with the following:
- Tcpdump -i eth0 port 18191 -w SIC_traffic.pcap
- Clicked on “Test SIC status” button to capture the interesting traffic.
- Upon opening the captured traffic on Wireshark, the 3-way TCP handshake is visible, along with the Client/Server hello packets but it ends with a decrypt error:

Due to the “packet size limited during capture” messages seen on Wireshark, I re-run tcpdump with the following syntax to capture the full packet:
Tcpdump -vvvi eth0 port 18191 -s0 -w SIC_entirepacket.pcap
The result is the following:

The TLS-handshake is now more detailed but again the gateway resets the connection as it can’t decrypt the packet.
Any help or insight would be much appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Backwards compatibility for an R80.20 SMS only extends back to gateway version R75.20, so having your SMS attempt to communicate with an R70 gateway is not supported. Is there some special reason you are using a version of software on the gateway that has not been supported for several years?
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We only considered it due to a certain customer's production network though we were almost certain that the experiment wouldn't work anyway....
From a closer technical perspective however, would you say that it is the newer TLS ciphers that a gateway as old as R70 wouldn't support, hence being unable to decrypt the SIC traffic?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Possibly, a gateway that old will try to use 3DES instead of AES for SIC encryption, and may also try to use the deprecated SHA-1 algorithm instead of SHA-256 which the R80.20 SMS will definitely not like. A gateway that old may also try to use the deprecated SSL protocol instead of TLS. Just because you can set the version on the gateway object to something that old prior to R75.20 doesn't mean everything will still work. 🙂
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
True, thanks very much for your input!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What you're seeing is expected behavior.
The default hash used for certificates generated by the ICA is:
- Releases prior to R80: SHA1
- R80 and above: SHA256
R71 was the first release to support SHA256 certificates.
That means for any R80+ manager trying to gateway prior to R71, if you attempt to establish SIC, it will surely fail.
See: SHA-1 and SHA-256 certificates in Check Point Internal CA (ICA)
Now, if you were managing the gateway in R77.30 and then upgraded that manager to R80+, you could still push policy to the gateway.
In fact, I tested this myself by upgrading an R77.30 Manager to R80.10 and pushing policy to an R65 gateway.
While completely and totally unsupported, it worked. ![]()
However, if I ever regenerate the SIC certificate for this gateway, SIC would likely start failing because of this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmmm. Maybe you can help me with a block on rule 995 in my R65 gateway 😉
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yikes, that brings back some memories ![]()
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 05:00 PM (CEST)
SASE Masters: Deploying Harmony SASE for a 6,000-Strong Workforce in a Single WeekendAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center


