• The full list of IPS protections migrated to other blades in R80.10 is documented here: sk103766: List of IPS Protections removed in R80.x. There is also an informative discussion at CheckMates titled “Where did all my IPS Protections go?” https://community.checkpoint.com/message/6315
• There are FOUR different types of exceptions related to IPS, make sure you add the right one to address your issue! The most
reliable way to add an Exception is directly from a log entry referencing the IPS Protection itself.
• The four types of Exceptions are below and presented roughly in the order that they are applied by the gateway:
◦ Geo Policy Exceptions
◦ Inspection Settings Exceptions
◦ ThreatCloud Exceptions
◦ Core Activations Exceptions
Exceptions Tips & Tricks
• There are two levels of Exceptions that can be defined in IPS: per–signature & global. If a particular signature is causing false–
positives with a certain system, always create an Exception for that specific signature first. If you are still having numerous
false–positive issues with many signatures for a single IP address or network, only then should you consider adding a global
Network Exception.
• In an IPS exception rule for R77.XX gateways, the Action is always Inactive. For other Threat Prevention blades you can select
the Action; normally the actions would be Detect or Inactive, but it can also be Prevent which is an interesting option.
• Although they were part of the IPS blade in R77.XX and earlier, Inspection Settings are now part of the Access Control policy
layers and no longer part of IPS/Threat Prevention in R80+ management. They perform protocol inspection that is inherent in
the gateway’s stateful inspection process, and have the following attributes:
◦ As shown above Inspection Settings are part of the Access Control policy layers, so if any changes are made to them, the
Access Policy needs to be installed to the gateway.
◦ Similarly to Core Activations, all Inspection Settings are included with a new software release, and are not updated via IPS
Updates from the Check Point ThreatCloud.
◦ Inspection Settings Exceptions are specified separately from Threat Prevention Exceptions, so the main Threat Prevention
Global exceptions DO NOT apply.
◦ One, some, or all Inspection Settings signatures can be specified in a single Inspection Setting Exception rule for an R80.10
gateway. For an R77.30 gateway, Inspection Settings Exceptions must be specified in the IPS layer under Threat Prevention.
◦ Each gateway has exactly one Inspection Settings Profile assigned to it.
• Note that creating an Exception simply changes the final decision (usually from Prevent to Detect or Inactive) but does not stop
the relevant blades from still expending CPU overhead to inspect the traffic.
• IPS Exceptions (whether for R77.XX gateways or R80.10+ gateways) will not exempt traffic from IPS inspection completely
and allow the traffic to take a more efficient path. An Exception only changes the decision made about whether to Prevent the
traffic or not; the traffic still must pass through the same processing path it would have even if there was no Exception at all.
• However for an R80.10+ gateway one can define a “null” IPS Profile like this:
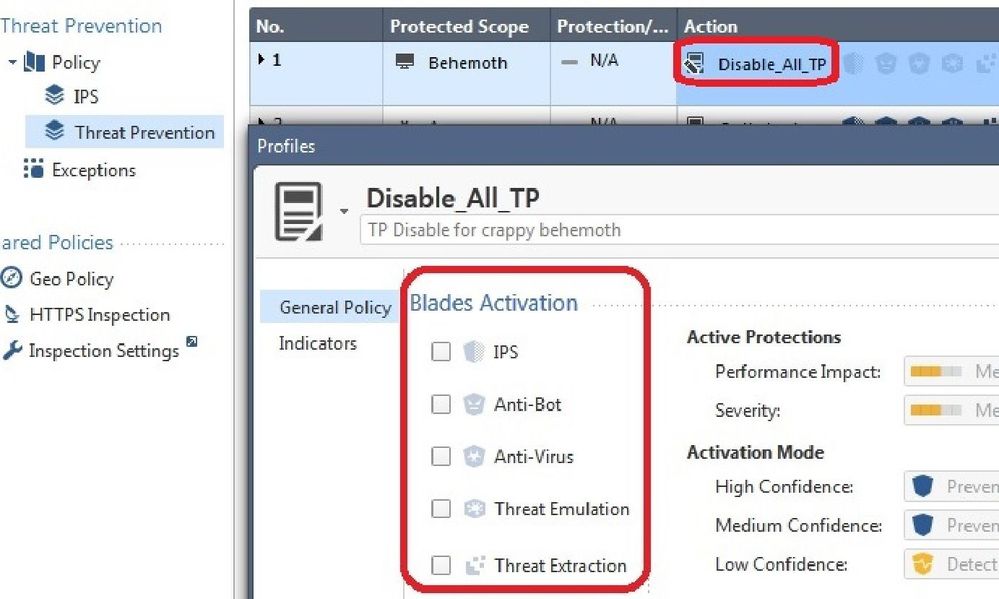
• For traffic traveling to and from the system Behemoth, no IPS inspection (or any other Threat Prevention inspection in this
example) will occur at all, and the traffic may now be eligible to be handled in the fastpath (SXL path). However if some other
blade such as Application Control is also inspecting the traffic, it will still need to take the Medium Path (PXL). But even if that
is the case, significant CPU overhead will be saved by avoiding IPS inspection of this traffic completely in PXL. This “null”
profile’s positive effect on performance is significantly larger than that of an IPS Exception.



