Check Point R80 Security Management provides the most advanced security management platform for enterprises to consolidate all aspects of their security so they can be more efficient at deploying the strongest protections across their organizations.
1. One platform, One policy

We believe the key to managing security complexity is to bring all security protections and functions under one umbrella. With R80, security consolidation is fully realized:
- One Console: a single platform manages the entire IT infrastructure – from the data center to private/public cloud deployments – for security efficiency and consistency.
- Unified Policy: Policy management is unified so you can create and monitor these policies harmoniously. One single access policy manages your users, devices, applications, data and networks. IPS, anti-virus, anti-bot and Threat Emulation policies are unified under a single threat prevention policy. With this unified policy, you also get unparalleled granular control over policy.
2. Layered Policy Management
Today’s cloud environments enable extreme agility in the delivery of applications and services and security must be equally adaptable to keep up. Our unified policy is easily segmented into manageable sections, or policy layers:
- Policy can be segmented into layers for seamless network segmentation.
- Policy layers can be easily delegated to, and managed by different administrators.
- Tasks can be automated by policy layer, providing better control over processes.
3. Extensible, Scalable Platform
R80 makes it easy to align security to IT processes and systems:
- Trusted integrations: The R80 API makes it easy to integrate securely with orchestration, change management and ticketing systems. With the ability to control exactly what that integration can and cannot do, organizations have the confidence to embed security into their IT ecosystem.
- Automated operations: Routine tasks can be automated and delegated, freeing up security teams from repetitive tasks to focus on strategic security tasks like incidence response.
4. Task-Oriented Management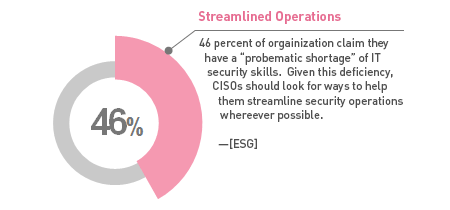
A security management system should anticipate the daily tasks of a security administrator. To that end, we have simplified interfaces and built-in numerous features into our management interface to streamline processes and make it as efficient as possible for security teams to do their work.
- Concurrent administration now allows multiple administrators to work simultaneously on the same policy without conflict.
- Productivity tools such as installation history and integrated logs help streamline policy troubleshooting.
- Policy best-practice features such as policy validation provide security intelligence to help administrators make better policy decisions.
5. Integrated Threat Management

All those who manage security, from systems administrators to senior managers, need a succinct understanding of the company’s security posture and its ability to respond to threats. R80 consolidates logging, monitoring, event correlation and reporting, so you can find the information you need, all in one place.
- Fully integrated threat management speeds incidence response and event investigations.
- A single view into security status provides comprehensive visibility across the network.
- Integrated compliance validates policy and configuration changes in real-time, against a library of 300+ security best practices and industry standards.
- Easily customizable dashboards and reports let security teams monitor what's important to them and their stakeholders.






