- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Mastering Compliance
Unveiling the power of Compliance Blade
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
May the 4th (+4)
Navigating Paradigm Shifts in Cyber
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
Introducing Quantum Force
Accelerated AI-Powered Firewalls
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Harmony
- :
- Endpoint
- :
- EndPoint Management in R80.20
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
EndPoint Management in R80.20
I am trying to figure out if in R80.20+ the function of the Endpoint Management server is now integrated with general Management server and does not require any additional servers.
Since I am not very familiar with the EndPoint managment, please let me know if the products refered to as EndPoint Security, EndPoint Security Management and EndPoint Management refer to the same thing.
The client has R77.30 Management server with R75.XX Endpoint Security (or management) and they are looking to upgrade the whole shebang to R80.20.
So what I am trying to determine is what the best upgrade path is and if the policies, packages etc.. from the old EndPoint Management/Security server should and could be migrated to a new consolidated Management server.
Thank you,
Vladimir
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a very important question. I know that R80.20 SMS supports both gateway and endpoint management.
Have a Look at Endpoint Homepage in the Detail per release section......
But I can‘t found any usefull information for an upgrade and experience from a migration of an real environment. We had a customer running both managements on R77.30 and want to upgrade.
Any information woud be very helpfull.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To my understanding R80.20 is fully supported running both gateway management and endpoint management om the same server.
in that way you can correlate both gateway logs with endpoint logs side by side. Quite cool feature actual
Best Regards
Kim
Kim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Domain Admin account for Endpoint Management is mentioned only once in the "Endpoint Security Management Server R80.20 Administration Guide" After the service account is created:
"Enter (and confirm) the password of the Active Directory Domain Admin user you created for Endpoint Security use."
I do not see the Domain Admin rights as a prerequisite earlier in the documentation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The reason R77.30.0x existed was because Endpoint features were evolving faster than Network Management.
In R80.20, the management changes from R77.30.03 were merged in, so you can theoretically run them on the same appliance.
Whether you should do this is a different question.
Likewise, merging (or splitting) Network and Endpoint Management currently requires Professional Services (I.e. No automated process for this currently)
In R80.20, the management changes from R77.30.03 were merged in, so you can theoretically run them on the same appliance.
Whether you should do this is a different question.
Likewise, merging (or splitting) Network and Endpoint Management currently requires Professional Services (I.e. No automated process for this currently)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, so it is still advisable, from your point of view, to maintain the EndPoint management on a separate instance of the Management Server? Is it simply deployed as a "Secondary Management" and the Endpoint Management blade and Logging and Reporting enabled on it? Or is there a different ISO or FTW option for standalone Endpoint Management?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To @PhoneBoy' s point, we found a few compelling reasons to keep the management for the two separate. In our case, some of it was a matter of our primary SMS being located on a segment of the network that we don't allow everyone to reach. It made it easier to put the management for Endpoint on a LAN that was easily accessible by all our client machines.
We also found that the features in Endpoint have been evolving at a different, faster pace than most CP products. For that reason, we also liked the idea of keeping them separate. We have the flexibility to move the two between versions at different paces if necessary. The one tricky thing of doing it this way is getting the logs merged with the GW logs, but there are some good SK articles to help with that.
As far as setting it up, you wouldn't define it as a secondary management server. You would just use the R80.20 Management ISO and build a new SMS instance with Endpoint and Logging enabled.
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you @Daniel_Taney . Can you tell me about the integration of the SmartConsole and SmartEndpoint? In a Demo Mode, once you are in SmartConsole, you can drop down the menu in the top-left corner and start he SmartEndpoint from there without being prompted for logon and similar to the SmartDashboard for "unevolved" applications.
Is there a SIC established between SmartEndpoint and the Management Server? If so, how, if it is installed as another primary?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, you don't establish SIC per se... it is a little confusing. I believe this SK helps explain ways to import logs from an externally managed Management Server.
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you. From the looks of it, CP has some work to do in terms of integrating EP with Management in the same security domain. If the common wisdom is still to keep EP on a separate machine, as in the past, what is the justification of jumping through so many hoops to get them working together? That is a rhetorical question 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Some help here please...
I am looking at the client with CPSM-P1003 (blades NPM, EPM, LOGS) and the CPEP-C1-VPN-F-VSI-25 license.
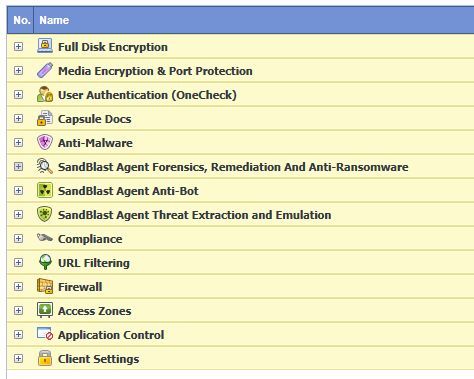
And am trying to figure out what, if anything, the EndPoint could manage on this client? I do not believe there is a dedicated VPN management section in the EndpoinPolicy and the only things that come to mind without additional licenses are the "Client Settings" and perhaps "User Authentication", even that one I am not sure about.
Also, can someone tell me if these features:
Require EndPoint Firewall and Compliance blade to be taken advantage of?
If so and if this is the only goal for the client, do they actually need an EndPoint Management server? What other functionality would they be able to utilize with only VPN and Compliance blades licensed?
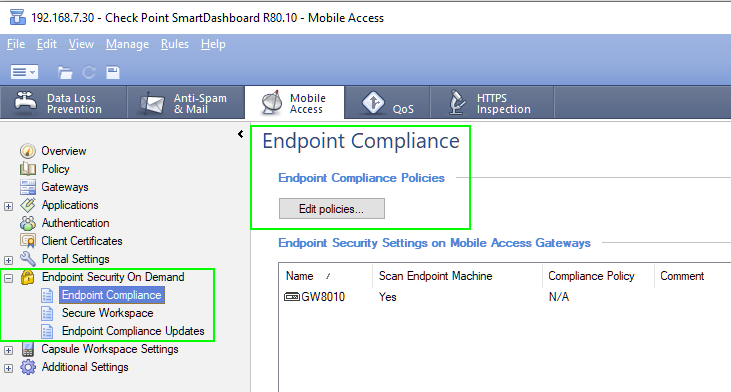
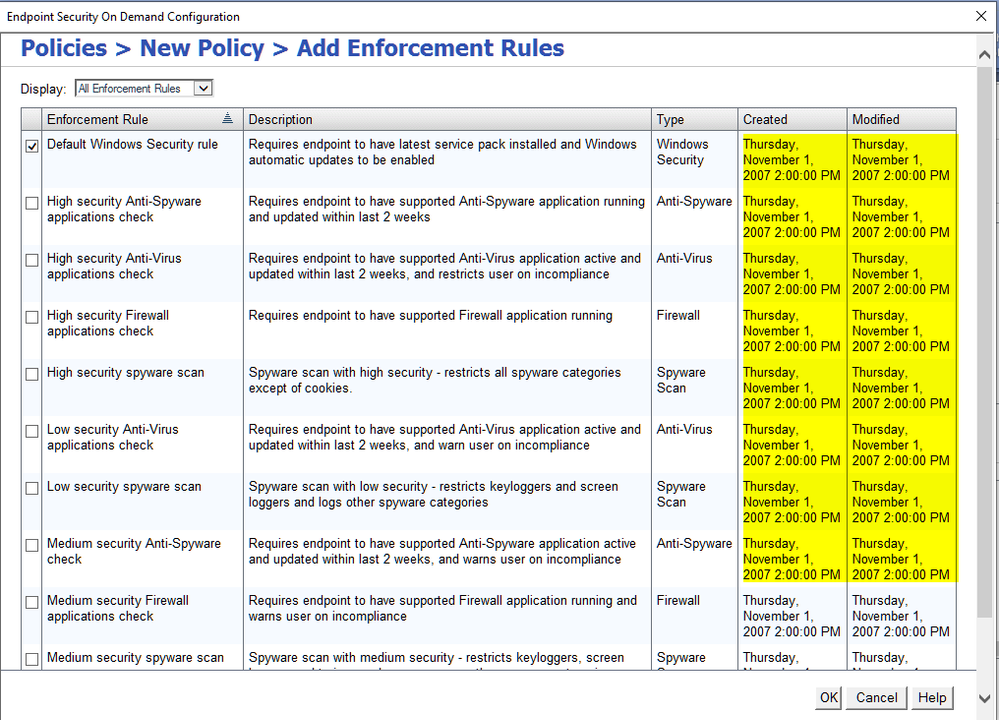
In Compliance section there are two options:

What relation do they have to EndPoint Security on Demand?
Thank you,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe that going forward, the SmartEndpoint is the management tool of choice. That is the tool where all the policy for the SandBlast, Disk Encryption, Capsule Docs, Firewall, etc.. blades resides. I'll be honest, I'm no expert on the "legacy" Endpoint; which I think its more what is illustrated in your screen shot, but Check Point has so many VPN / Remote Access options, it is almost dizzying 🙂 sk67820 gives you all the possible options!
I actually don't use the Endpoint Client for VPN. So I really can't comment too much on that piece of it. However, I believe that the settings and controls for that are still a part of the Mobile Access blade, which would be in the Legacy SmartDashboard. None of that changes in R80.20. You still have you use SmartDashboard to manage DLP, Anti-Spam, QoS, Mobile Access and HTTPS.
I'm not sure if that helps answer your questions or not?
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you. It still eludes me as to what the client is licensed for and what possible advantage they are getting from their EPM blade, given that they are only licensed for VPN and the EP container.
Since EP itself does not appear to have a dedicated VPN section in its policy, I have to only speculate that the "legacy" or "On Demand" is the option they have to use.
Really would like to get more clarity on the subject.
As you have mentioned there is an overabundance of EndPoint clients and Remote Access solutions. This makes life quite complicated, especially if we are not dealing with those on regular bases.
Regards,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
None of the VPN solutions require Endpoint Management to manage, which can be done with regular IPSec or Mobile Access Blade.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And if client is looking to enforce compliance with Microsoft Patches and AV signatures, is this something that is achievable by using these rules to create a policy or choosing one of the three baked-in policies?
And the CPEP-C1-VPN-F-VSI-25 license covers this use case?
If this is the case, I am trying to figure out what is the reason for this client to maintain the EPM server if that's the only license for the endpoint that they are using.
Am I missing something?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For Endpoint Compliance features, you definitely need SmartEndpoint.
ESOD is for access via the Mobile Access Portal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Got it. Looking through the Endpoint Security R80.20 Management Server Administration Guide, I see that:
Container license -One license for each endpoint client (seat). This license is attached to the Endpoint Security Management Server.
Software Blade licenses -Network Protection - Bundle license that includes Endpoint Security Firewall, Compliance, Application Control, and Access Zones.
*Note - This license automatically comes with the Container License
And since client already has CPEP-C1-VPN-F-VSI-25 license, they should be able to enforce compliance on the VPN Endpoints using EPM.
Thank you for sticking with this thread!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 17 Apr 2024 @ 05:00 PM (CEST)
Mastering Compliance: Unveiling the power of Check Point Compliance BladeThu 18 Apr 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Sicherheit auf neuem Niveau: Risikoanalyse und SchutzstrategienThu 18 Apr 2024 @ 11:00 AM (CDT)
Central US: Network Security Troubleshooting - Part 3 - ClusterXLWed 17 Apr 2024 @ 05:00 PM (CEST)
Mastering Compliance: Unveiling the power of Check Point Compliance BladeThu 18 Apr 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Sicherheit auf neuem Niveau: Risikoanalyse und SchutzstrategienThu 18 Apr 2024 @ 11:00 AM (CDT)
Central US: Network Security Troubleshooting - Part 3 - ClusterXLAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center