Hi,
We are running CheckPoint EndPoint as a cloud deployment and I have the following questions/issues.
We are using the default Firewall Policy
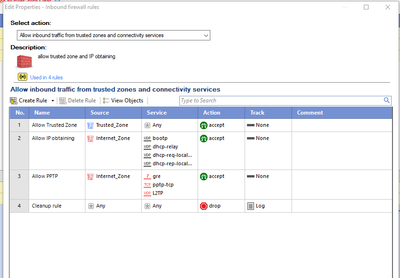
Does the “Trusted_Zone” objected correspond to the “Access Zones” policy “Trusted Zone Locations”
And if so then the “Internet_Zone” object would be everything not in the “Trusted Zones Location”.
Looking at the documentation this appears to be the case but it is not very clear
So the default Desktop/Laptop Firewall policy is completely open.
----------
Chapter 13 Access Zones Policies
Access Zones Definitions lets you to create discrete security zones for use in Application Control and Firewall Rules. For this reason, configure Access Zones before configuring Application Control and Firewall Rules. There are two Access Zones: The Internet Zone The Trusted Zone Network locations not placed in the Trusted Zone automatically belongs to the Internet Zone.
In This Chapter
Trusted Zone 83 Locations 84 Creating New Access Zones Definitions 87 Changing an Existing Access Zones Policy 88
Trusted Zone The Trusted Zone contains network objects that are trusted. Configure the Trusted Zone to include only those network objects with which your programs must interact.
Note - Objects not placed in the Trusted Zone are placed automatically in the Internet Zone.
The Endpoint Security Management Console contains an initial Access Zones policy. In the initial policy, these network elements are included in the Trusted Zone: All_Internet This object represents all legal IP addresses. In the initial policy, all IP addresses on the Internet are trusted. However, the Access Zones policy is not a policy that is enforced by itself but only as a component of the Application Control and Firewall Rules policies. For example, in the Application Control policy, access permissions are granted for each application or applications group when accessing the Trusted Zone or the Internet Zone. If the initial Access Zones policy is used in an Application Control policy , then the idea of an Internet Zone has no meaning. The Internet Zone is the same as the Trusted Zone.
------
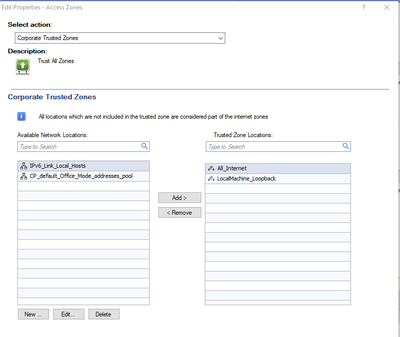
Following on from the above I need to populate the “Trusted Zone Location” with my internal network and remove “All_Internet”.
But what happens when a corporate laptop connects to a public wifi with the same network segment as corporate network, we will have no Firewall protection. How do I resolve this issue? Note we are using EndPoint in the cloud.
Thanks in advance.




