Hi all,
We recently released SandBlast Agent E81.40!
E81.40 introduces new features, stability and quality improvements. The complete list of improvements can be found in the version release’s Secure Knowledge sk162334.
New Engine – Machine Learning Static File Analysis
We are constantly working on improving our detection/prevention engines and on new technologies to mitigate new threats.
We are happy to introduce the availability of a new detection/prevention engine – Static File Analysis power by Check Point Machine Learning algorithms.
This new technology consists of examining the executable file, inspecting hundreds of static features which are processed by the Machine Learning algorithm to provide very quick verdicts.
The benefits are:
- Ultra-fast scans and verdicts are given in a few tens of milliseconds.
- No performance impact on the machine.
- Up-to-date Machine learning models – updates are pushed to the client when needed.
- Extremely low false positive rate.
- Complements SandBlast Agent security offering with no additional fee for threat prevention licensed customers.
Note that as of E81.40, Static File Analysis is enabled by default.
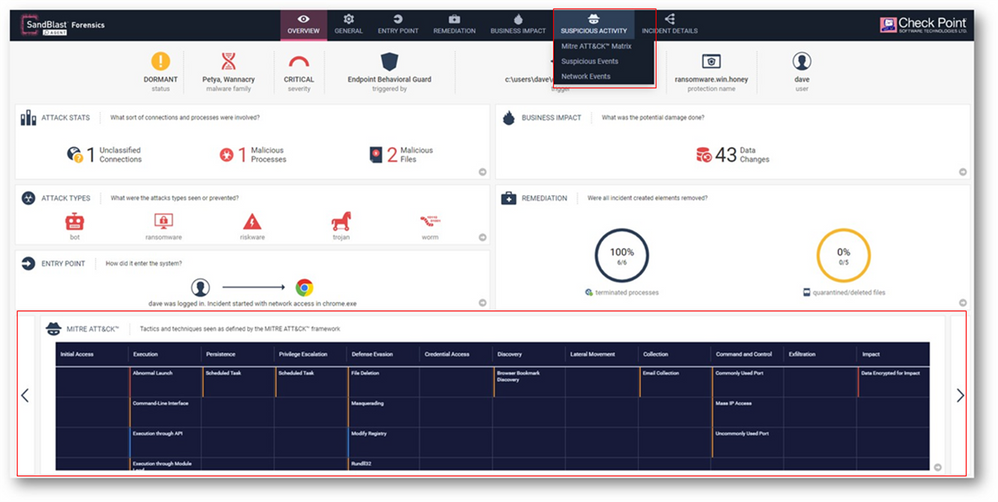
Mitre ATT&CK view in Forensic Report
The MITRE ATT&CK™ framework is a comprehensive matrix of tactics and techniques used by threat hunters, red teamers, and defenders to better classify attacks and assess an organization's risks.
The framework aim is to improve post-compromise detection behavior understanding in enterprises by illustrating the actions an attacker may have taken.
The E81.40 Forensics reports support the MITRE ATT&CK matrix which adds another layer of information to better understand the attack flow and technics/tactics used as defined in the framework.

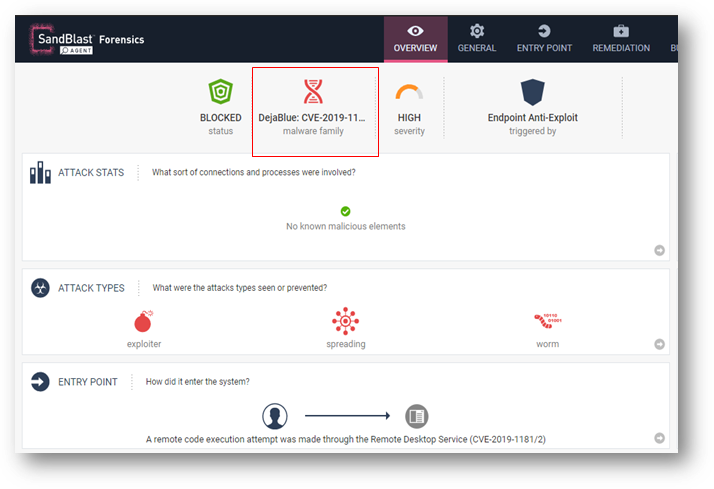
Anti-Exploit detection of DejaBlue CVE-2019-1181
DejaBlue is a pre-authentication remote code execution vulnerability in Remote Desktop Protocol, similar to recent BlueKeep CVE-2019-0708 vulnerability.
The SandBlast Agent Anti-Exploit engine is able to detect and prevent against DejaBlue attacks.
This improvement is a continuation of our rapid release of protection against Bluekeep vulnerability where SandBlast Agent was the first endpoint security to provide a real detection and mitigation for Bluekeep.
Behavioral Guard and Forensic Enhancements
E81.40 introduces the following enhancements to Behavioral Guard and Forensics:
- Remote Desktop Protocol identification – Forensics reports will present information such as remote users who log into the machine, machine name, IP address, and remote connection access (inside or outside the network).
- Injection identification – Forensics reports now showcase and highlight injections that happen during an incident.
- Privilege Escalation identification – Forensic report will present process integrity levels and privilege escalation.






