From my original article https://medium.com/@jaydenaung/securing-kubernetes-environments-with-check-point-cloudguard-cspm-ea2... )
Many organizations are proactively moving their developments and application workloads to cloud, wholeheartedly embracing the rise of cloud-native applications. From virtualized machines in physical data centers, to Infrastructure-as-a-service, to containers, to serverless compute platforms — the innovation has come a long way. We’ve also been completely mesmerized by immense potentials of cloud-native applications and microservices architectures, and what they can offer to us.
Now that you’ve also decided to go cloud-native, and implemented kubernetes clusters for your containers and cloud native applications. Kubernetes is really awesome, there is no doubt about that. However, how can you be sure that the kubernetes clusters you’ve created are in line with security best practices? Misconfigurations in Kubernetes clusters can introduce tons of serious security challenges for development, test and production environments. Be it self-hosted or cloud provider-managed, misconfigurations in Kubernetes happen all the time for various reasons. For example, if you explicitly allow containers with allowPrivilegeEscalation flag set to true, that’s a misconfiguration. This kind of misconfiguration introduces both security and compliance challenges.
It’s time to put “Sec” in DevOps
It is time to instill “security” into your DevOps methodology. In this article, I’ll share how to take the first step in securing your Kubernetes environments. IT security also should play an integrated role in the full lifecycle of cloud-native applications, and that also means applying security on container orchestration tool such as Kubernetes. We’ll start with “compliance”, and you can explore more once you’ve taken the first step.
Check Point CloudGuard
Check Point’s CloudGuard secures your Kubernetes environments by assessing the clusters for misconfigurations and policy violations, scanning your container images for vulnerabilities, and keeping you informed of the security posture of your Kubernetes environments. CloudGuard can provide the same security for your cloud assets on public cloud service providers such as AWS, Azure, and GCP. But let’s focus on Kubernetes for now.
Let’s secure your Kubernetes clusters
And here is how you can start securing your Kubernetes environments in less than 30 minutes.
First, get your free CloudGuard CSPM account — go to https://secure.dome9.com/v2/register/invite and register for a 15-days trial account with your business email.
Then you’ll need to Onboard your Kubernetes clusters to CloudGuard Cloud Security Posture Management platform. You can do the onboarding on CloudGuard web console in less than 15 minutes, following a few simple steps below.
- Go to “Asset Management”, and “Onboarding”.
- Choose “Get started with Kubernetes”
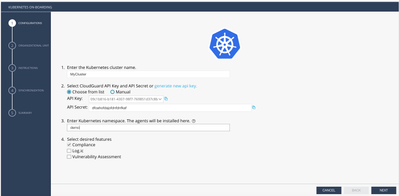
(You’ll need CloudGuard API Key and API secret, which you can generate on CloudGuard web console.)
Enter the following:
- Cluster Name
- API Key
- API Secret
- Enter namespace
- Select desired features — choose “Compliance”
(If you’d like to explore vulnerability assessment and network traffic analysis, feel free to choose all.)
Click “Next”.
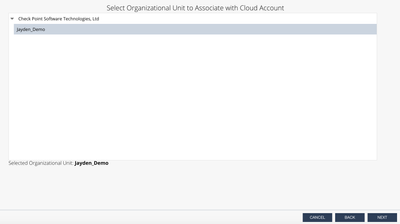
Choose an organization if there is one. And click “Next”.
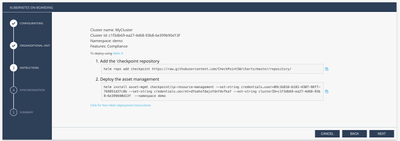
And basically execute the Helm commands as instructed by the onboarding Wizard.
You’ll see that onboarding process is in progress, and finally see that you’ve a Kubernetes cluster onboarded to CloudGuard!
Automate onboarding
If you don’t prefer the manual onboarding, you can completely automate the onboarding process using python or bash shell scripts. I’ve developed both python and bash shell scripts which basically do the same thing. The python version was improved and contributed by my Check Point colleague from Spain. Check out my Github URL here for more details. https://github.com/jaydenaung/cloudguardk8s
You can use either way to onboard your Kubernetes clusters to CloudGuard. Once the cluster is onboarded, you can then go to “Posture Management”, “Compliance Rulesets”, and Search the Kubernetes-related compliance rulesets. (Use “Add filter”.)
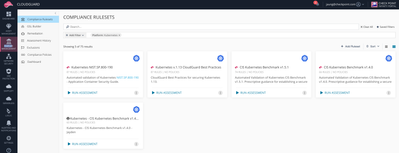
Choose one ruleset that you prefer . I’m using CloudGuard Best Practices. Click “Run Assessment” , and choose the cluster that you’ve just onboarded. The compliance engine will start running the assessment.
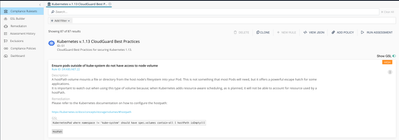
And in a couple of minutes, you will get a complete compliance and security report! This is only on-demand assessment. This compliance assessment can be automated by using “Continuous compliance” feature. The idea is to remain compliance at all times.
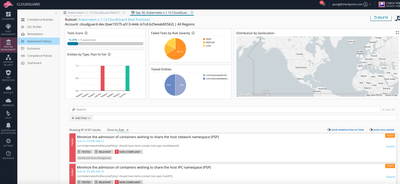
Now you can view how secure your Kubernetes environment is, and analyze the report! You can basically dive into each assessment result, see which entities are not compliant, and read the recommended actions to address the misconfigurations. (We have plans to add auto-remediation feature which automates the responses to address misconfigurations.)
You should also explore GSL builder. GSL stands for Global Security Language, which is a simple, easy-to-use yet very powerful query language which can allow you to easily find any misconfiguration or even create your own custom compliance rule.
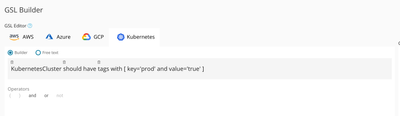
Check Point CloudGuard is 100 percent API-driven and you can integrate CloudGuard into your CICD pipeline with ease. Your automation tool can call CloudGuard API to run the assessment, and CloudGuard can then send the findings to third party systems such as SIEM as well.
Congratulations! You’ve taken the first step in securing your Kubernetes environment — using CloudGuard posture management. We still need to talk about container image vulnerabilities, workload runtime security and pods network access control. Maybe for another time!