- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Check Point
for Beginners
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Educational Resources
- :
- Check Point for Beginners
- :
- Part 11 - Threat Prevention
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
OPEN OTHER ARTICLES
 Part 1 - The Architecture
Part 1 - The Architecture
 Part 2 - Preparing the Lab
Part 2 - Preparing the Lab
 Part 3 - Installing Security Management Server
Part 3 - Installing Security Management Server
 Part 4 - Installing Security Gateway
Part 4 - Installing Security Gateway
 Part 5 - Gaia WebUI and CLI
Part 5 - Gaia WebUI and CLI
 Part 6 - Working with SmartConsole
Part 6 - Working with SmartConsole
 Part 7 - Managing Security Policies
Part 7 - Managing Security Policies
 Part 8 - Network Address Translation
Part 8 - Network Address Translation
 Part 9 - Application Control, URL Filtering and Content Awareness
Part 9 - Application Control, URL Filtering and Content Awareness
 Part 10 - Identity Awareness
Part 10 - Identity Awareness
 Part 12 - Logs and Reporting
Part 12 - Logs and Reporting
 Site to Site VPN in R80.x - Tutorial for Beginners
Site to Site VPN in R80.x - Tutorial for Beginners
 Absolute Beginner’s Guide to R80.x
Absolute Beginner’s Guide to R80.x
 Handling Traffic in the Access Policy - Knowledge Nuggets
Handling Traffic in the Access Policy - Knowledge Nuggets
 Video - Security Administration Experience
Video - Security Administration Experience
 Video - Securing Hybrid Cloud Environment
Video - Securing Hybrid Cloud Environment
 Video - Smart-1 Cloud - Cloud Based Security Management
Video - Smart-1 Cloud - Cloud Based Security Management
 Video - Container Security
Video - Container Security
 Video - Identity Based Segmentation
Video - Identity Based Segmentation
 Video - Securing Public Cloud Environment
Video - Securing Public Cloud Environment
 Video - Threat Hunting, Detection, and Monitoring
Video - Threat Hunting, Detection, and Monitoring
 Video - Firewall as a Service (FWaaS)
Video - Firewall as a Service (FWaaS)
 Video - Application Control and URL Filtering
Video - Application Control and URL Filtering
 Video - TLS Inspection
Video - TLS Inspection
 Video - Hyper Scale Clustering with Quantum Maestro
Video - Hyper Scale Clustering with Quantum Maestro
 Video - Check Point R81.X - Crash Course - Introduction
Video - Check Point R81.X - Crash Course - Introduction
 Video - Check Point R81.X - Crash Course - Admin GUI
Video - Check Point R81.X - Crash Course - Admin GUI
 Video - Check Point R81.X - Crash Course - SmartConsole
Video - Check Point R81.X - Crash Course - SmartConsole
 Check Point Jump Start - Product Deployment
Check Point Jump Start - Product Deployment
 Network Security
Network Security
PREVIOUS ARTICLE
TO READ THE FULL POST
it's simple and free
NEXT ARTICLE
Part 11 - Threat Prevention
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2020-06-11
04:58 AM
In Lecture 7, we mentioned different types of Security Policies, such as Access Control, Threat Prevention, and Desktop Security. Previous lectures have been primarily focused on Access Control, which uses the Firewall, Application Control, URL Filtering, and Content Awareness Software Blades to reduce the attack surface by allowing only authorized traffic to cross the security system.
In this lecture, we discuss the Threat Prevention policy, which deals with the traffic which is already allowed through Access Control policy.
Threat Prevention Software Blades
Threat Prevention includes the following Software Blades:
- IPS – Intrusion Prevention System provides protection against malicious and unwanted network traffic including known exploits and vulnerabilities, protocol misuse, outbound malware communication, and tunneling attempts.
- Anti-Bot – Detects bot-infected machines and prevents bot damages by blocking bot Command and Control communications.
- Anti-Virus – Provides real-time virus signatures and anomaly-based protections
- Threat Emulation – Prevents infections from undiscovered exploits, zero-day and targeted attacks and is based on sandboxing malware detection.
- Threat Extraction – Removes exploitable content from documents, including active content and embedded objects, reconstructs files to eliminate potential threats, and promptly delivers sanitized content to users to maintain business flow.
Each of the mentioned Software Blades would be fascinating topics on their own. However, the CP4B format does not enable us to review them in depth. You can use other spaces of CheckMates to learn more.
In this lecture, we will focus on building and applying a Threat Prevention Policy.
Assessing Security Status with CheckMe
Before we start building our Threat Prevention policy, we’ll use the Check Point CheckMe service to assess the initial status.
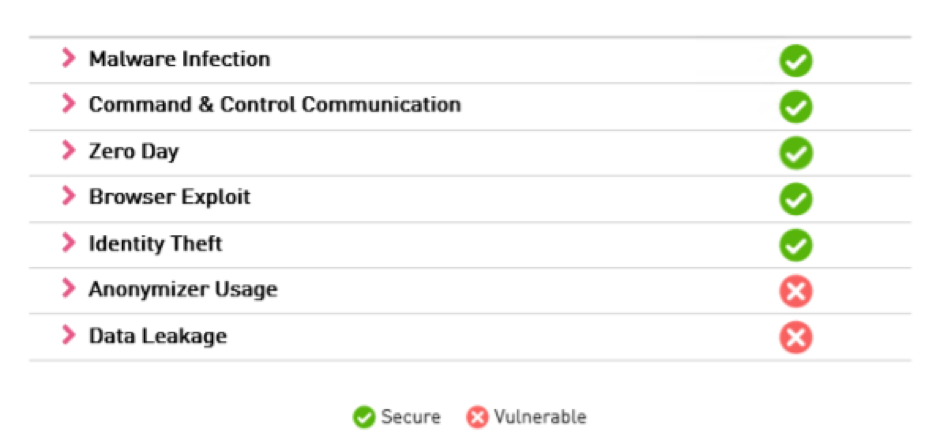
CheckMe service simulates many types of attacks that can compromise your computer and the information on your network. This service includes series of tests that checks your vulnerability of your network, endpoint, cloud and mobile to Ransomware, Phishing, Zero-Day, Bot communication, Browser Exploit, Anonymize usage and Data leakage. For more details about the test and methodology, look into SecureKnowledge article sk115236 describing the tool.
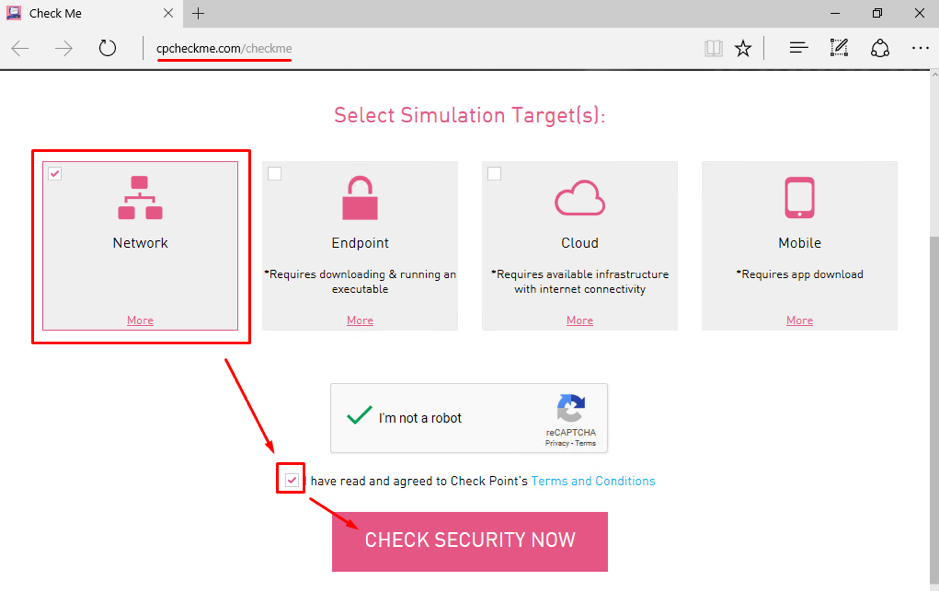
Open CheckMe link from Lab User PC virtual machine. Chose Network as a Simulation Target and click on CHECK SECURITY NOW.
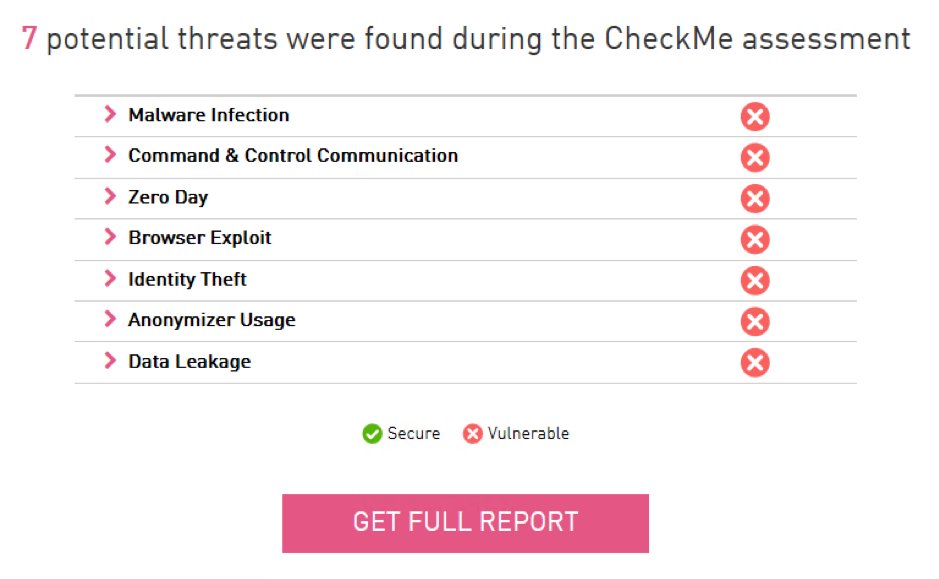
You can see the test results shortly:
As you can see, the machine is vulnerable. To mitigate the risks, we will build a Threat Prevention policy.
Setting up the Threat Prevention Policy
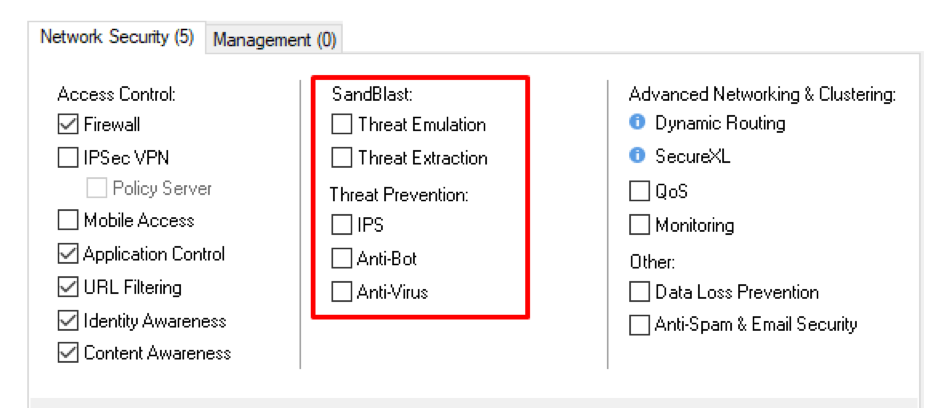
First, we’ll need to activate the appropriate Software Blades. To do so, open your Security Gateway object and start by checking the IPS checkbox:
Choose “According to the Threat Prevention policy” and press OK.
Similarly, activate Anti-Virus and Anti-Bot.
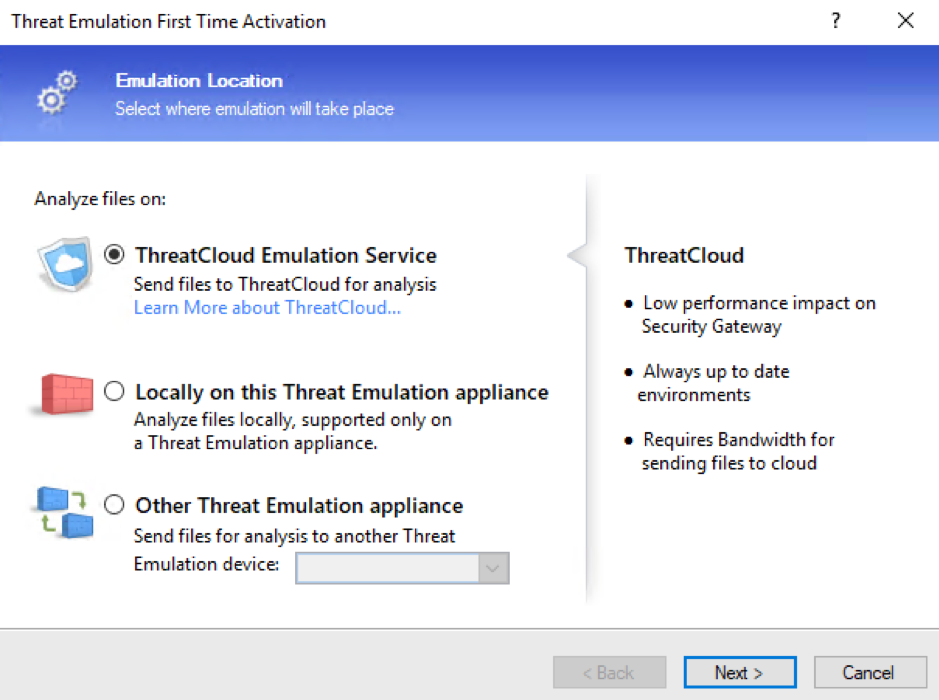
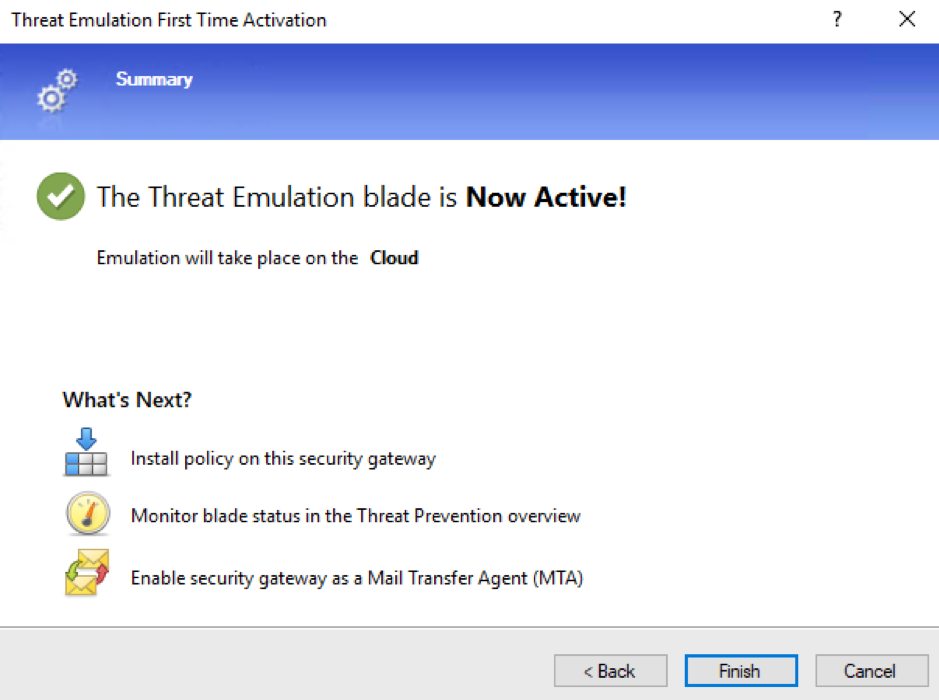
When activating Threat Emulation, choose “ThreatCloud Emulation Service” and then press Next:
After a moment, you will see the activation message. Press Finish:
Now, enable Threat Extraction blade and choose “Skip this configuration now”, because we do not use MTA in our setup:
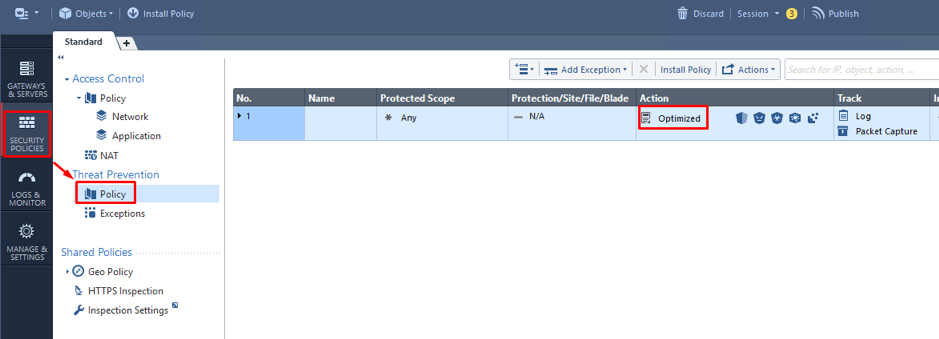
Once the software blades we need are activated, go to Security Policies > Policy. By default, we have there a single protection profile named “Optimized”:
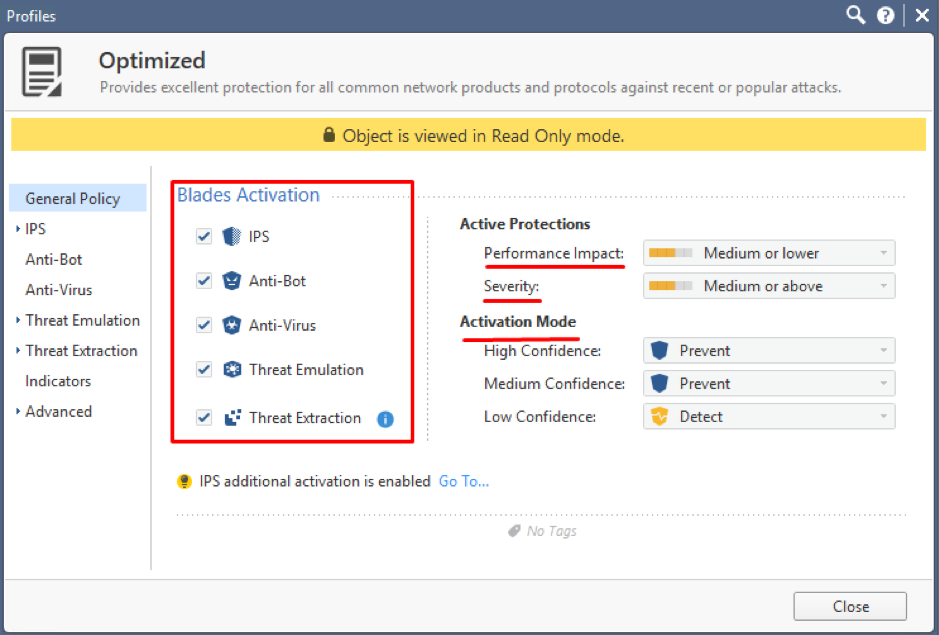
Let’s take a look in the Profile settings. Right-click on the profile and choose View:
You can see the activated blades included in the profile and also the key settings:
- Performance Impact;
- Severity;
- Confidence Level.
This profile will automatically activate all protections with medium or lower performance impact, and medium or higher severity.
There are various actions available for protection groups with different confidence level:
- Detect;
- Prevent;
- Inactive;
- Ask.
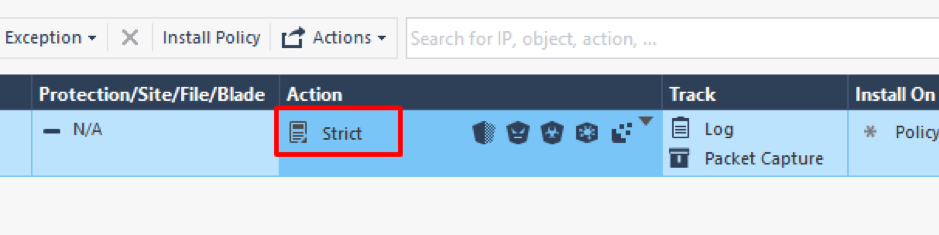
You cannot change the default profile settings, but you can clone a profile, if necessary. In our case, we will change the active profile from Optimized to Strict.
This profile has more active protections in it.
Now, take a look on additional settings in the down left corner of SmartConsole:
Threat Tools allow advanced management of IPS settings. It is also advisable to update IPS signatures. To do so, click on Updates.
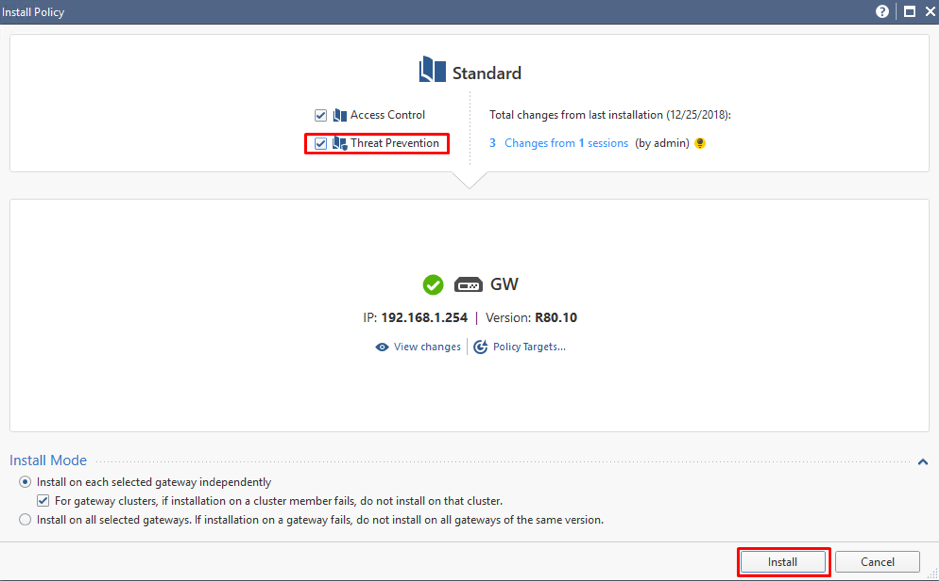
We have activated different Threat Prevention blades and changed the profile to Strict. It is now time to install Threat Prevention Policy. Mark “Threat Prevention” in the policy installation pop-up for that.
Press Install and wait for the end of policy installation process.
The Second CheckMe Assessment
Once more, go to the CheckMe portal from Lab User CP virtual machine. The results are looking much better now:
Yet, as you can see, there is still room to improve the security posture.
Threat Prevention Logs
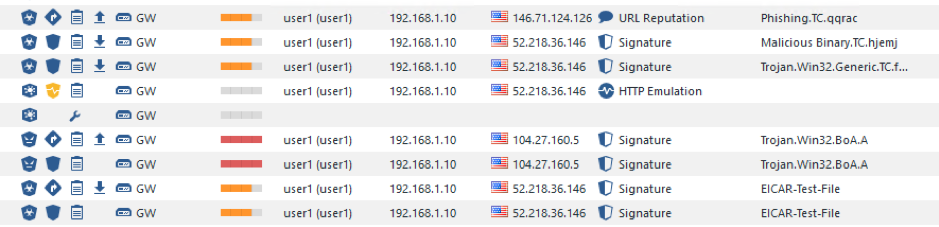
Let’s look at the logs. Go to Logs & Monitor, then to Queries > Threat Prevention > All:
Here, you can see the latest Threat Prevention logs. Go over them to see the entries for various blades.
This lecture is just an introduction into Threat Prevention software blades and their functions.
To master the topic, we invite you to follow Threat Prevention Space in our CheckMates community. You will find there lots of interesting topic related to the subject.
In the next lecture, we will talk about Logs and Event Analysis.
----------------------------
Authors and Contributors
Author - Evgeniy Olkov, CTO at TS Solution.
Founded in 2010, the TS Solution is a fast growing Russian company, focused on integrating high-tech networking, security and server virtualization systems and technologies, along with maintenance and professional services.
Translation and editing - Valeri Loukine
Review and editing - Dameon Welch-Abernathy
Labels
In Lecture 7, we mentioned different types of Security Policies, such as Access Control, Threat Prevention, and Desktop Security. Previous lectures have been primarily focused on Access Control, which uses the Firewall, Application Control, URL Filtering, and Content Awareness Software Blades to reduce the attack surface by allowing only authorized traffic to cross the security system.
In this lecture, we discuss the Threat Prevention policy, which deals with the traffic which is already allowed through Access Control policy.
Threat Prevention Software Blades
Threat Prevention includes the following Software Blades:
- IPS – Intrusion Prevention System provides protection against malicious and unwanted network traffic including known exploits and vulnerabilities, protocol misuse, outbound malware communication, and tunneling attempts.
- Anti-Bot – Detects bot-infected machines and prevents bot damages by blocking bot Command and Control communications.
- A
4 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center