- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Mastering Compliance
Unveiling the power of Compliance Blade
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
May the 4th (+4)
Navigating Paradigm Shifts in Cyber
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
Introducing Quantum Force
Accelerated AI-Powered Firewalls
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- Re: problem adding interoperable device via web AP...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
problem adding interoperable device via web API
Hello Guys
I am trying to create interoperable device via python web API (I have v1.1)
I have this payload to put into commend 'add-generic-object'
object = {
'create': 'com.checkpoint.objects.classes.dummy.CpmiGatewayPlain',
'name': deviceName,
'ipaddr': deviceIP,
'thirdPartyEncryption': True,
'osInfo': {
'osName': 'Gaia'
},
'vpn': {
'create': 'com.checkpoint.objects.classes.dummy.CpmiVpn',
'owned-object': {
'vpnClientsSettingsForGateway': {
'create':
'com.checkpoint.objects.classes.dummy.CpmiVpnClientsSettingsForGateway',
'owned-object': {
'endpointVpnClientSettings': {
'create':
'com.checkpoint.objects.classes.dummy.CpmiEndpointVpnClientSettingsForGateway',
'owned-object': {
'endpointVpnEnable': True
}
}
}
},
'ike': {
'create': 'com.checkpoint.objects.classes.dummy.CpmiIke',
},
'sslNe': {
'create': 'com.checkpoint.objects.classes.dummy.CpmiSslNetworkExtender',
'owned-object': {
'sslEnable': False,
'gwCertificate': 'defaultCert'
}
},
'isakmpIpcompSupport': True,
'isakmpUniversalSupport': True,
}
},
'dataSourceSettings': None,
'nat': None,
'encdomain': 'ADDRESSES_BEHIND_GW',
'ignore-warnings': True,
'color': color.upper()}After I run script, object is visible in Interoperable devices, but I cannot use is. It is NOT visible when I try it add to VPN communities and also when I try add VPN community to this object it ends with error: A blocking validation error was found: Gateway does not comply to 'Participant Gateways' of Meshed community. In order to comply the gateway needs to be VPN installed and of type Host / Gateway / Cluster / Interoperable device.
Object can be 'fixed' via GUI by setting IPSec VPN -> Traditional mode configuration -> Select some enc and hash (i.e. 3des sha1) -> OK, But I cannot find the way set this through set-gneric-object
this does not work:
{'uid': objectUID, 'vpn' : {'ike' : {'isakmpHashmethods': ['SHA1']}}}what am I doing wrong? Via dbedit it works, but I would like to use clearer way ...
19 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Possible this may help you find the right way: https://community.checkpoint.com/thread/11337-class-names-available-for-use-with-the-show-generic-ob...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello again
Here is output from show generic-object for working interoprable device created by GUI:
objectValidationState: null
color: "BLACK"
manualEncdomain: "d87e9442-eefa-4ba6-8472-2dcba5806642"
vpnAllowRelay: false
ipPoolOverrideHide: true
macAddress: ""
type: "gateway"
excludeExternalInterfacesFromEncDomain: false
thirdPartyEncryption: true
gtpRateLimit: 2048
enforceGtpRateLimit: false
dnsResolverInterval: 600
interfaces: []
backupGw: false
additionalProducts: null
snmp: null
enableMulticastAcceleration: false
ipPoolSecuremoteAllocationName: null
dag: false
ipPoolSecuremote: false
encdomain: "MANUAL"
addrTypeIndication: "IPV4"
autoTopologyCustomRecalculationTime: 10
osInfo:
objId: "b4a4923a-b997-445e-a4bd-068af7403c4b"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
osBuildNum: 0
osspminor: 0
osType: 0
osVersionLevel: ""
osVerMajor: 0
osName: "Gaia"
osspmajor: 0
osVerMinor: 0
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: ""
dataSource: "NOT_MINUS_INSTALLED"
natSummaryText: ""
ipPoolAllocPerDestination: false
backupGateway: null
rangeEncdomain: null
supportIpPoolNat: false
cpProductsInstalled: false
edges: []
securityBladesTopologyMode: "TOPOLOGY_TABLE"
performEncryption: true
ipPoolGw2gw: false
certificates: []
ipPoolPerInterface: false
ipPoolExhaustRetInterval: 30
vpnRelayIfName: ""
connectra: false
supportIkeV2: true
firewall: "NOT_MINUS_INSTALLED"
connectraSettings: null
autoTopologyUseCustomRecalculationTime: false
ipaddr: "10.10.10.2"
ipPoolUnusedReturnInterval: 60
vpn:
objId: "00ace2ae-d15a-4615-b2d7-64b6850292ea"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
singleVpnIp: ""
interfaceResolvingHaPrimaryIf: ""
clientlessVpnAskUserForCertificate: "NONE"
offerNattResponder: true
enableInternetRouting: false
forceNatT: false
vpnClientsSettingsForGateway:
objId: "01fa7fc8-960d-4378-a238-a01e1650d4a6"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
usb1VpnClientSettings: null
endpointVpnClientSettings:
objId: "d5ea091b-4fb8-4a7e-afd1-3a65466570ca"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
endpointVpnEnable: true
endpointVpnConnectivityMethod: "IPSEC"
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: ""
type: "vpn_clients_settings_for_gateway"
enableBasicVpnSecuremote: true
enableVpnWithEndpointSecurity: true
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: ""
fwWireLogOnlySyn: true
singleVpnIpRa: ""
thirdPartyEncryption: true
availableVpnIpListGw: []
isakmpUdpencapsulation:
objId: "f787c070-d69e-4ebf-a143-ee49cea5860f"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
resource: "97aeb390-9aea-11d5-bd16-0090272ccb30"
active: true
folderPath: null
text: null
folder: null
is_owned: false
ownedName: ""
isakmpEmail: ""
isakmpIpcompSupport: false
accept3desForClientlessVpn: true
fwz: null
tunnelKeepaliveMethod: "TUNNEL_TEST"
dnsIpResolution: ""
useService: "97aeb443-9aea-11d5-bd16-0090272ccb30"
availableVpnIpList: []
isakmpDn: ""
isakmpDoDnsResolve: false
useCert: ""
multipleIspVpn: false
ipResolutionMechanismGw: "MAINIPVPN"
disableNoSaLogsForUser: true
replyFromSameIp: true
vpnTunnelMtu: 0
linkSelectionMode: "HIGHAVAILABILITY"
outgoingSourceIp: "AUTOMATIC"
ipsecCopyTosToInner: false
isakmpAllowedCert: []
interfaceResolvingHaPrimaryIfGw: ""
ipResolutionMechanism: "MAINIPVPN"
ikeSendFrags: false
applyResolvingMechanismToSr: true
isakmpSubnetSupport: true
isakmpAuthmethods: []
enableRouting: true
vpnCompLevel: 2
useClientlessVpn: false
dnsIpResolutionGw: ""
replyToSameIp: true
vpnLinkResolverNotification: "NONE"
supportWireMode: false
ike:
objId: "95903133-3add-438c-92f8-1e844ff8f09c"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
isakmpPhase1RekeyingTime: 1440
isakmpHashmethods: []
isakmpCrlreq: false
isakmpPhase1DhGroups:
- "97aeb629-9aea-11d5-bd16-0090272ccb30"
isakmpkeymanager: null
ikeEmptyUdpSocket: false
isakmpPhase2RekeyingKbytes: 50000
isakmpsharedkey: []
isakmpPhase2RekeyingTime: 3600
isakmpPhase2UseRekeyingKbytes: false
isakmpEncmethods: []
isakmpAggressiveSupport: false
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: "test2"
clientlessProcNum: 1
useInterfaceIp: true
tcpt:
objId: "b4a4923a-b997-445e-a4bd-068af7403c4b"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
resource: "97aeb443-9aea-11d5-bd16-0090272ccb30"
cpmiInterface: "All IPs"
active: false
vpndInternalBindPort: 444
folderPath: null
text: null
folder: null
is_owned: false
ownedName: ""
isakmpDnsName: ""
ipsecReplayCounterWindowSize: 64
sslNe:
objId: "a0201a4b-3e2f-49c5-b67a-e7251cdbe026"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
sslEnable: false
internalListeningPort: "b8f7c593-f9ee-4c55-b48a-6ce3be6760ac"
neoEnable: false
gwCertificate: "defaultCert"
endPointNameResolution:
objId: "f787c070-d69e-4ebf-a143-ee49cea5860f"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
downloadNameResolutionSettingsToEndPoint: false
useSameSettingsAsGw: true
folderPath: null
text: null
folder: null
is_owned: false
ownedName: ""
clientType: "AUTODETECT"
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: ""
name: ""
ipsecDontFragment: true
rerouteEncryptedPackets: true
outgoingSingleIp: ""
ikeFetchCrlFailOpen: false
ipsecCopyTosToOuter: true
icon: "Unknown"
takeTunnelGranularityFromComm: true
fwWireLog: false
isakmpMatchpeer: []
useInterfaceIpGw: true
ipsecFragmentInner: false
isakmpAllowedCa: null
dpdAllowedToInitIke: true
isakmpUniversalProtocol: "WILDCARD_IDS"
ikeSupportNatT: true
color: "BLACK"
natdSendAllIfcs: false
displayName: ""
ikev2AcceptAllTs: false
respondFromSameIfc: false
offerNattInitator: false
comments: ""
sendSingleNatdSource: true
isakmpUniversalSupport: true
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: "test2"
features: []
systemTags: []
tags: []
customFields: []
metaInfo: null
dataSourceSettings: null
nat: null
ipaddr6: ""
addAdtrRule: false
floodgate: "NOT_MINUS_INSTALLED"
uid: "16fdac28-af5c-4581-94a2-ee3030968bcb"
folder:
uid: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
name: "Global Objects"
domain:
uid: "41e821a0-3720-11e3-aa6e-0800200c9fde"
name: "SMC User"
meta-info:
metaOwned: false
lockStateResponse: null
validationState: "OK"
deletable: true
renameable: true
newObject: false
lastModifytime: 1549127325577
lastModifier: "mnemeth"
creationTime: 1549127325577
creator: "mnemeth"
tags: []
name: "test2"
icon: "NetworkObjects/gateway"
comments: ""
display-name: ""
customFields: []
_original_type: "CpmiGatewayPlain"
And here is the exact same device created by above script which is not working correctly ... I just changed this isakmpIpcompSupport': True to False because GUI object had this property False...
objectValidationState: null
color: "BLACK"
manualEncdomain: "d87e9442-eefa-4ba6-8472-2dcba5806642"
vpnAllowRelay: false
ipPoolOverrideHide: true
macAddress: ""
type: "gateway"
excludeExternalInterfacesFromEncDomain: false
thirdPartyEncryption: true
gtpRateLimit: 2048
enforceGtpRateLimit: false
dnsResolverInterval: 600
interfaces: []
backupGw: false
additionalProducts: null
snmp:
objId: "471f5a48-9650-423a-982b-63440b53d9b0"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
sysContact: ""
sysDescr: ""
readCommunity: ""
sysLocation: ""
sysName: ""
writeCommunity: ""
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: "test2"
enableMulticastAcceleration: false
ipPoolSecuremoteAllocationName: null
dag: false
ipPoolSecuremote: false
encdomain: "MANUAL"
addrTypeIndication: "IPV4"
autoTopologyCustomRecalculationTime: 10
osInfo:
objId: "431b7a78-ae8b-4e69-9b9c-0d89840f53e2"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
osBuildNum: 0
osspminor: 0
osType: 0
osVersionLevel: ""
osVerMajor: 0
osName: "Gaia"
osspmajor: 0
osVerMinor: 0
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: ""
dataSource: "NOT_MINUS_INSTALLED"
natSummaryText: ""
ipPoolAllocPerDestination: false
backupGateway: null
rangeEncdomain: null
supportIpPoolNat: false
cpProductsInstalled: false
edges: []
securityBladesTopologyMode: "TOPOLOGY_TABLE"
performEncryption: true
ipPoolGw2gw: false
certificates: []
ipPoolPerInterface: false
ipPoolExhaustRetInterval: 30
vpnRelayIfName: ""
connectra: false
supportIkeV2: true
firewall: "NOT_MINUS_INSTALLED"
connectraSettings: null
autoTopologyUseCustomRecalculationTime: false
ipaddr: "10.10.10.2"
ipPoolUnusedReturnInterval: 60
vpn:
objId: "06e8963e-cce6-44f5-926f-15f482109854"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
singleVpnIp: ""
interfaceResolvingHaPrimaryIf: ""
clientlessVpnAskUserForCertificate: "NONE"
offerNattResponder: true
enableInternetRouting: false
forceNatT: false
vpnClientsSettingsForGateway:
objId: "48c0e8f1-a320-45a2-8043-3b3ac22deeae"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
usb1VpnClientSettings: null
endpointVpnClientSettings:
objId: "6d30bba1-3bd4-41a6-a6ae-5d777ac929ae"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
endpointVpnEnable: true
endpointVpnConnectivityMethod: "IPSEC"
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: ""
type: "vpn_clients_settings_for_gateway"
enableBasicVpnSecuremote: true
enableVpnWithEndpointSecurity: true
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: ""
fwWireLogOnlySyn: true
singleVpnIpRa: ""
thirdPartyEncryption: true
availableVpnIpListGw: []
isakmpUdpencapsulation:
objId: "471f5a48-9650-423a-982b-63440b53d9b0"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
resource: "97aeb390-9aea-11d5-bd16-0090272ccb30"
active: true
folderPath: null
text: null
folder: null
is_owned: false
ownedName: ""
isakmpEmail: ""
isakmpIpcompSupport: false
accept3desForClientlessVpn: true
fwz: null
tunnelKeepaliveMethod: "TUNNEL_TEST"
dnsIpResolution: ""
useService: "97aeb443-9aea-11d5-bd16-0090272ccb30"
availableVpnIpList: []
isakmpDn: ""
isakmpDoDnsResolve: false
useCert: ""
multipleIspVpn: false
ipResolutionMechanismGw: "MAINIPVPN"
disableNoSaLogsForUser: true
replyFromSameIp: true
vpnTunnelMtu: 0
linkSelectionMode: "HIGHAVAILABILITY"
outgoingSourceIp: "AUTOMATIC"
ipsecCopyTosToInner: false
isakmpAllowedCert: []
interfaceResolvingHaPrimaryIfGw: ""
ipResolutionMechanism: "MAINIPVPN"
ikeSendFrags: false
applyResolvingMechanismToSr: true
isakmpSubnetSupport: true
isakmpAuthmethods: []
enableRouting: true
vpnCompLevel: 2
useClientlessVpn: false
dnsIpResolutionGw: ""
replyToSameIp: true
vpnLinkResolverNotification: "NONE"
supportWireMode: false
ike:
objId: "d48f659f-8efd-49dd-9339-48ba59de2ad0"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
isakmpPhase1RekeyingTime: 1440
isakmpHashmethods: []
isakmpCrlreq: false
isakmpPhase1DhGroups:
- "97aeb629-9aea-11d5-bd16-0090272ccb30"
isakmpkeymanager: null
ikeEmptyUdpSocket: false
isakmpPhase2RekeyingKbytes: 50000
isakmpsharedkey: []
isakmpPhase2RekeyingTime: 3600
isakmpPhase2UseRekeyingKbytes: false
isakmpEncmethods: []
isakmpAggressiveSupport: false
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: "test2"
clientlessProcNum: 1
useInterfaceIp: true
tcpt:
objId: "431b7a78-ae8b-4e69-9b9c-0d89840f53e2"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
resource: "97aeb443-9aea-11d5-bd16-0090272ccb30"
cpmiInterface: "All IPs"
active: false
vpndInternalBindPort: 444
folderPath: null
text: null
folder: null
is_owned: false
ownedName: ""
isakmpDnsName: ""
ipsecReplayCounterWindowSize: 64
sslNe:
objId: "c1293112-01c6-4448-82c7-1be64593dad3"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
sslEnable: false
internalListeningPort: "b8f7c593-f9ee-4c55-b48a-6ce3be6760ac"
neoEnable: false
gwCertificate: "defaultCert"
endPointNameResolution:
objId: "471f5a48-9650-423a-982b-63440b53d9b0"
checkPointObjId: null
domainId: "41e821a0-3720-11e3-aa6e-0800200c9fde"
downloadNameResolutionSettingsToEndPoint: false
useSameSettingsAsGw: true
folderPath: null
text: null
folder: null
is_owned: false
ownedName: ""
clientType: "AUTODETECT"
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: ""
name: ""
ipsecDontFragment: true
rerouteEncryptedPackets: true
outgoingSingleIp: ""
ikeFetchCrlFailOpen: false
ipsecCopyTosToOuter: true
icon: "Unknown"
takeTunnelGranularityFromComm: true
fwWireLog: false
isakmpMatchpeer: []
useInterfaceIpGw: true
ipsecFragmentInner: false
isakmpAllowedCa: null
dpdAllowedToInitIke: true
isakmpUniversalProtocol: "WILDCARD_IDS"
ikeSupportNatT: true
color: "BLACK"
natdSendAllIfcs: false
displayName: ""
ikev2AcceptAllTs: false
respondFromSameIfc: false
offerNattInitator: false
comments: ""
sendSingleNatdSource: true
isakmpUniversalSupport: true
folderPath: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
text: null
folder: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
is_owned: false
ownedName: "test2"
features: []
systemTags: []
tags: []
customFields: []
metaInfo: null
dataSourceSettings: null
nat: null
ipaddr6: ""
addAdtrRule: false
floodgate: "NOT_MINUS_INSTALLED"
uid: "054e4752-3c98-4a59-bf7e-6e7ff99fcab5"
folder:
uid: "e5c2231d-1dc3-408c-8cb9-588b275c2d8c"
name: "Global Objects"
domain:
uid: "41e821a0-3720-11e3-aa6e-0800200c9fde"
name: "SMC User"
meta-info:
metaOwned: false
lockStateResponse: null
validationState: "OK"
deletable: true
renameable: true
newObject: false
lastModifytime: 1549127013761
lastModifier: "mnemeth-API"
creationTime: 1549127013761
creator: "mnemeth-API"
tags: []
name: "test2"
icon: "NetworkObjects/gateway"
comments: ""
display-name: ""
customFields: []
_original_type: "CpmiGatewayPlain"
If you pass these both objects to editor and compare it, you will find that the objects ARE ALMOST THE SAME!. What is different are obviously UIDs of components, time of creation, admin username (I am using -API for scripts) and correct object has no snmp section while script obkect has snmp section. So... what can be wrong with second object, or other question, what to change in script to be correct???
Another strange thing is, when I run this command from command line from SmartConsole, the same object will be almost correct. But only almost... For first it will NOT be visible fro VPN Community, but if you assign VPN Community to the object, it will be OK and if you remove it again, after this it will be now visible from VPN Community too.
And If I create same object through dbedit with something like this (template for jinja2):
create gateway_plain {{ peerName }}
modify network_objects {{ peerName }} DAG false
modify network_objects {{ peerName }} color {{ color }}
modify network_objects {{ peerName }} VPN VPN
modify network_objects {{ peerName }} VPN:third_party_encryption true
modify network_objects {{ peerName }} VPN:IKE IKE
modify network_objects {{ peerName }} SNMP NULL
modify network_objects {{ peerName }} type gateway
modify network_objects {{ peerName }} add_adtr_rule false
modify network_objects {{ peerName }} ipaddr {{ peerIP }}
modify network_objects {{ peerName }} encdomain manual
modify network_objects {{ peerName }} manual_encdomain network_objects:{{ cryptoDomainGrp }}
update_all
It will work without any issue...
So it seems, that 4 different methods of creating the same Interoperable device (GUI, command line API, WEB API and dbedit) have different results... Strange, isnt't it?
Michael Nemeth
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another strange thing is that GUI created Interoperable object HAS in traditional mode parameters DES and MD5 selected, but these params are not shown in list from command, show generic-object... Why?
So after this recherche I think something like this
{'uid': result['uid'], 'vpn' : {'ike' : {'isakmpHashmethods': ['MD5']}}}
{'uid': result['uid'], 'vpn' : {'ike' : {'isakmpEncmethods': ['DES']}}}should definitelly help to create correct iteroperable device through WEB API, but I did not find way how to set list of methods to isakmpHashmethods and isakmpEncmethods using add generic-object or set generic-object... Is there any possibility how to do it? Thanks for help...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello again ...
I finally found in other thread "hack" with dbedit - change something (for example color), update_all, change something back, update_all. And it works....
But it makes no sence, if I NEED to use dbedit, I can make whole object through it, am I right? And I really wanted to avoid in my script connecting via ssh to SmartCenter (or in our case MDS) and run dbedit commands...
There istn't really another way to make it work WITHOUT dbedit?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Right now, you are correct: no way to make this object entirely thru API.
There are a handful of objects like this currently (gateway cluster objects being most requested).
We do plan to address this in later releases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, thnx very much. I can live with this somehow ... Another quick question. We need also create dynamic Interoperable devices ... Problem is, that if you create dynamic interoperable device through GUI, it assign some IP 0.0.x.y and increment some internal counter. I can do the same through dbedit or generic-object API, but I need to select IP manually. Is it OK to select some random "dynamic" IP from some range? I am really afraid to pud such "workaround" to production. Best way I am doing this now is creating non dynamic device with API and then finish configuration through GUI, where I just create dynamic interface and change type to dynamic (DAG)... Is there any workaround to correctly fully automate this action?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just for you guys, If you will have same problem. You really don't need use dbedit for alter color. But you really have to change something on newly created object (for example color is easiest). It works for me when I create interoperable device using add-generic-object and publish, then I change color with command set-generic-object (color is in CAPS) and again publish and then object is finally visible in VPN communities.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I have maybe final question regarding this Interoperable device creation. I see, that if you creating some section or list of interfaces for example, with add-generic-object you are using "com.checkpoint.objects.classes.dummy.CPSomething" .
Is there any list of these dummy classes? Because I finally don't need use dbedit at all, as I mentioned in my last comment, but if I have Interoperable device with certificate and I want to check DN, in object created via GUI show-generic-object looks like this:
isakmpMatchpeer:
- "DN"
and same object without checked DN checkbox looks like this
isakmpMatchpeer: []
With dbedit I can create this "DN" element with command
addelement network_objects someObjectName VPN:isakmp.matchpeer DN.
I expect that for the same action in add-generic-objects it should be something like this:
'isakmpMatchpeer' : {'create' : 'com.checkpoint.objects.classes.dummy.CP????} . maybe CPDN
Shortly: I need create in tree vpn -> isakmpMatcheer list with one element "DN".
Is there any way how to do it with add-generic-object or set-generic-object or I still need to use for this dbedit?
thnx much.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume you’ve reviewed:Re: How to find generic-object that is not defined in the API?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Michael,
I'm experiencing same "problems".
Maybe I'm something for you: I've discovered the class "com.checkpoint.objects.classes.dummy.CpmiDAGInterface" usefull to add an external interface with dynamic IP without getting into problems when try to modify the object from GUI (if I create an "com.checkpoint.objects.classes.dummy.CpmiInterface" with dynamicIp field setted to true when I try to modify object usong GUI it raise a strange error ... before this 'discovery' the only solution I had was to add the interface using GUI).
Shoud be wonderfull if CheckPoint will provide more complete documentation about Man API usage.
Now I'm trying to solve the "other problem": add elements using API.
I've to add elements to "isakmpHashmethods" and "isakmpEncmethods" ..... but at the moment I'm able to do it only using dbedit ![]() ..... I keep trying ...
..... I keep trying ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've realized that I'd made a typo on class name (no copy'n'paste), the correct class name is "com.checkpoint.objects.classes.dummy.CpmiDagInterface"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thnx for info I will test it ...I have issue with DAG, that if you create object through GUI it will assign to this object some phantom IP (0.0.x.y) and keeps counter for already assigned addresses somewhere. But if I will create object with dbedit, I don't know how to use this internal counter, I need to choose object IP by myself. And I don't know if I choose something, if it will not mess whole database or SmartCenter at all. So I am afraid to do it in production. In testing management it kinda works. Anyway here is my dbedit script for create DAG Interoprable device.
create gateway_plain {{ objName }}
modify network_objects {{ objName }} DAG true
modify network_objects {{ objName }} color orange
modify network_objects {{ objName }} VPN VPN
modify network_objects {{ objName }} VPN:third_party_encryption true
modify network_objects {{ objName }} VPN:IKE IKE
modify network_objects {{ objName }} SNMP NULL
modify network_objects {{ objName }} type gateway
modify network_objects {{ objName }} add_adtr_rule false
modify network_objects {{ objName }} ipaddr {{ ipAddr }} =====> here you MUST choose and set some object IP even if it is dynamic Interoperable device
addelement network_objects {{ objName }} VPN:isakmp.matchpeer DN
modify network_objects {{ objName }} VPN:isakmp.dn '{{ your DN here }}'
modify network_objects {{ objName }} VPN:isakmp.allowed_ca servers: {{ your CA name here }}
addelement network_objects {{ objName }} interfaces interface
modify network_objects {{ objName }} interfaces:0:ipaddr {{ lanIP }}
modify network_objects {{ objName }} interfaces:0:netmask {{ lanNetmask }}
modify network_objects {{ objName }} interfaces:0:officialname lan
modify network_objects {{ objName }} interfaces:0:ifindex 0
modify network_objects {{ objName }} interfaces:0:security:antispoof true
modify network_objects {{ objName }} interfaces:0:security:netaccess:access this
modify network_objects {{ objName }} interfaces:0:security:netaccess:perform_anti_spoofing true
addelement network_objects {{ objName }} interfaces interface
modify network_objects {{ objName }} interfaces:1:ipaddr {{ wanIP }}
modify network_objects {{ objName }} interfaces:1:netmask {{ wanNetmask }}
modify network_objects {{ objName }} interfaces:1:officialname wan_real
modify network_objects {{ objName }} interfaces:1:security:netaccess:leads_to_internet true
modify network_objects {{ objName }} interfaces:1:security:antispoof true
modify network_objects {{ objName }} interfaces:1:security:netaccess:perform_anti_spoofing true
modify network_objects {{ objName }} interfaces:1:ifindex 1
addelement network_objects {{ objName }} interfaces DAG_interface
modify network_objects {{ objName }} interfaces:2:dynamic_ip true
modify network_objects {{ objName }} interfaces:2:officialname wan
modify network_objects {{ objName }} interfaces:2:security:netaccess:leads_to_internet true
modify network_objects {{ objName }} interfaces:2:security:netaccess:perform_anti_spoofing false
modify network_objects {{ objName }} interfaces:2:ifindex 2
update_all
I don't think you need to add isakmp methods to the Interoperable device... Methods in interoperable device are important only if you run VPN rulebase in traditional mode (Which is not supported now). It is totally ok to set up crypto methods only in VPN community ... If you want I can pass my solution for VPN community also...
But even with possibility adding DAG interface, it is not solving my problem with adding DN list. I need dummy class like this. But I dont know if it exists
com.checkpoint.objects.classes.dummy.CpmiDN
If I can ask, how and where did you discover this DAG dummy class? Maybe we can find another classes, which checkpoint is silently hiding from us 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Michael,
I'm not able to find where checkpoint puts the "DAG IP counter", as you know checkpoint increment this every time you configure a gw from SmartConsole (even if you discard changes).
In ipaddr filed of a dag gw you have to use an IP from 0.0.0.0/8 network (0.0.0.0 excluded)
I think that checkpoint do it in that way hoping that nobody will configure more that ~16581375 gateways ....
If you configure through api a gw using a following IP smartconsole it doesn't check if the ip exists, and a duplication results in (I doesn't test the consequences of this situation ... ).
A workaround could be to use the same "checkpoint thinking" .... but in reverse order: starting using 0.255.255.255 and go backwards, maybe using a script that will find the last used IP to assign the previous one to the new gw. In that way is improbable that the two counters will meed each others.
To discover checkpoint classes .... I've started doing "bruteforce" .... but then I've found the ws schema!
isakmpMatchpeer type is not related to a class, let me show:
--------------------------------------------
<xs:element maxOccurs="unbounded" minOccurs="0" name="isakmpMatchpeer" nillable="true" type="tns:CpmiPublicKeyMatchingCriteriaIntCpmiPublicKeyMatchingCriteriaIsakmpMatchpeer">
<xs:annotation>
<xs:appinfo>
<DisplayName description="" value="Matching Criteria List"/>
</xs:appinfo>
</xs:annotation>
</xs:element>
--------------------------------------------
is only a restriction (I think ... I'm not so 'in touch' with web services schemas)
--------------------------------------------
<xs:simpleType name="CpmiPublicKeyMatchingCriteriaIntCpmiPublicKeyMatchingCriteriaIsakmpMatchpeer">
<xs:restriction base="xs:string">
<xs:enumeration value="DN"/>
<xs:enumeration value="EMAIL"/>
<xs:enumeration value="DNS_IP"/>
</xs:restriction>
</xs:simpleType>
--------------------------------------------
but a wasn't able to fill isakmpMatchpeer field anyway.
Maybe using two brains we can reach a solution ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Old post, but still just in case others are still reading this (I did) i found a solution to fix the object through the API.
Your comments that editing the object in dbedit fixed it made me try the same thing through the REST API.
We're using PowerShell due to our automation system, but the example below should be easy enough to port to python for those who prefer that.
Right now, I don't set interfaces, and the VPN Domain is set to a manually specified group in the first section.
# Ignore SSL:
[System.Net.ServicePointManager]::ServerCertificateValidationCallback = {$true}
# Set Variables (Change These to match your environment)
$BaseUri = "https://10.20.30.40/web_api"
$domain = "CMA_Domain_Name"
$InterDevName = "InterOpGateway1"
$InterDevIP = "10.10.10.1"
$InterDevVpnDomain = "VPNDomainGroup"
# Posted variables for easy example, but [PSCredential] are recommended for PowerShell scripting.
$user = "s_api"
$pass = "ApiRocks!"
# No changes should be required below this part, but feel free to play around.
# Remove domain for standalone managements. (Written for MDS)
$loginData = @{
"user" = $user
"password" = $password
"domain" = $domain
} | ConvertTo-Json
Write-Output "Invoking Login"
$login = Invoke-RestMethod -Method Post -Uri "$BaseUri/login" -Body $loginData -Headers @{ "content-type" = "application/json" }
$headers = @{
"content-type" = "application/json"
"x-chkp-sid" = $login.sid
}
$body = @"
{
"name": "$InterDevVpnDomain"
}
"@
$group = Invoke-RestMethod -Method Post -Uri "$BaseUri/show-group" -Body $body -Headers $headers
$groupuid = $group.uid
$addgw = @"
{
"create" : "com.checkpoint.objects.classes.dummy.CpmiGatewayPlain",
"name" : "$InterDevName",
"osInfo" : {
"osName" : "Gaia"
},
"ipaddr" : "$InterDevIP",
"thirdPartyEncryption" : "true",
"nat" : null,
"dataSourceSettings" : null,
"manualEncdomain": "$groupuid",
"encdomain": "MANUAL",
"vpn" : {
"create" : "com.checkpoint.objects.classes.dummy.CpmiVpn",
"isakmpIpcompSupport": false,
"isakmpUniversalSupport": false,
"owned-object" : {
"vpnClientsSettingsForGateway" : {
"create" : "com.checkpoint.objects.classes.dummy.CpmiVpnClientsSettingsForGateway",
"owned-object": {
"endpointVpnClientSettings" : {
"create": "com.checkpoint.objects.classes.dummy.CpmiEndpointVpnClientSettingsForGateway",
"owned-object" : {
"endpointVpnEnable" : "true"
}
}
}
},
"ike" : {
"create" : "com.checkpoint.objects.classes.dummy.CpmiIke"
},
"sslNe": {
"create": "com.checkpoint.objects.classes.dummy.CpmiSslNetworkExtender",
"owned-object" : {
"sslEnable" : "false",
"gwCertificate" : "defaultCert"
}
},
"isakmpIpcompSupport" : "true",
"isakmpUniversalSupport" : "true"
}
}
}
"@
# Add Interoperable device
Write-Output "Adding InterOperable gateway"
$gw = Invoke-RestMethod -Method Post -Uri "$BaseUri/add-generic-object" -Body $addgw -Headers $headers
$null = Invoke-RestMethod -Method Post -Uri "$BaseUri/publish" -Body "{}" -Headers $headers
Sleep 5
# Update Interoperable device to make it available for VPN Community
$gwuid = $gw.uid
$setgw = @"
{
"uid" : "$gwuid",
"nat" : null,
"dataSourceSettings" : null,
"manualEncdomain": "$groupuid",
"encdomain": "MANUAL",
"vpn" : {
"isakmpIpcompSupport": false,
"isakmpUniversalSupport": false
}
}
"@
Write-Output "Editing InterOperable gateway"
$null = Invoke-RestMethod -Method Post -Uri "$BaseUri/set-generic-object" -Body $setgw -Headers $headers
$null = Invoke-RestMethod -Method Post -Uri "$BaseUri/publish" -Body "{}" -Headers $headers
#Logout
Write-Output "All done, terminating session."
Invoke-RestMethod -Method Post -Uri "$BaseUri/logout" -Body "{}" -Headers $headers
I hope this can help others automate their tasks. Let me know if anything is unclear and I'll try to clearify.
/S
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, you are right ... to change something on freshly added device will fix it in Smartcenter, but I still have no solution for Matching Criteria and for choosing IP address of dynamic device ... Unfortunatelly we have plenty of VPNs connected here via private APNs from two mobile operators (if one fails second one is active), so DAIP is mandatory, but I am still forced to click them manually into SmartCenter 😞 ... Two years later, R80.40 is out and still no fresh wind into Interoperable Devices API.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Michael_Nemeth ,
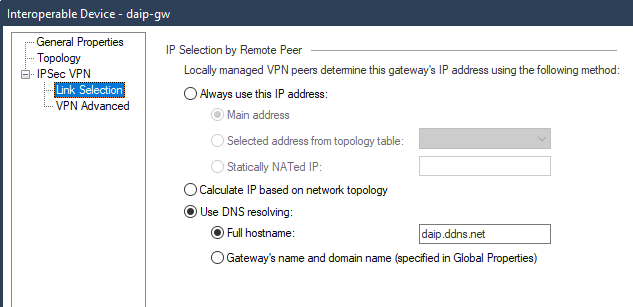
If you change the last json bit that edits the interoperable gateway, you will be able to select "Use DNS resolving" on the object. (if this is your missing bit.)
$setgw = @"
{
"uid" : "$gwuid",
"nat" : null,
"dataSourceSettings" : null,
"manualEncdomain": "$groupuid",
"encdomain": "MANUAL",
"vpn" : {
"isakmpIpcompSupport": false,
"isakmpUniversalSupport": false,
"ipResolutionMechanismGw": "DNSLOOKUP",
"dnsIpResolutionGw": "daip.ddns.net"
}
}
"@
The set-generic-object isn't officially supported, but it helps of get past the missing API's for now. 🙂
If I misunderstood your need, please let me know, I'm quite interested in solving/automating the entire VPN setups for all our use cases as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, where can I see the structure of this method?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.20 has formal API support for this.
See: https://sc1.checkpoint.com/documents/latest/APIs/index.html#cli/add-interoperable-device~v1.9%20
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 3 | |
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Wed 17 Apr 2024 @ 05:00 PM (CEST)
Mastering Compliance: Unveiling the power of Check Point Compliance BladeThu 18 Apr 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Sicherheit auf neuem Niveau: Risikoanalyse und SchutzstrategienThu 18 Apr 2024 @ 11:00 AM (CDT)
Central US: Network Security Troubleshooting - Part 3 - ClusterXLWed 17 Apr 2024 @ 05:00 PM (CEST)
Mastering Compliance: Unveiling the power of Check Point Compliance BladeThu 18 Apr 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Sicherheit auf neuem Niveau: Risikoanalyse und SchutzstrategienThu 18 Apr 2024 @ 11:00 AM (CDT)
Central US: Network Security Troubleshooting - Part 3 - ClusterXLAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center