- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Mastering Compliance
Unveiling the power of Compliance Blade
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
May the 4th (+4)
Navigating Paradigm Shifts in Cyber
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- Re: Show Package - Tool to visualize a R80 policy ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Show Package - Tool to visualize a R80 policy package over HTML pages
Overview
Check Point ShowPolicyPackage tool visualizes the contents of a R80 security policy package (layers, rulebases, objects) over HTML pages.
Description
The tool allows the security policy as well as objects in the R80 objects database to be exported into a readable format. This exported information represents a snapshot of the database.
The tool generates a compressed file (.tar.gz) containing the following files:
• HTML files - The objects and rules presented as html files. The "index.html" acts as a starting point and
lists all the available items to display.
• JSON files - The objects and rules exported as multiple JSON files.
• Log file (e.g. show_package-yyyy-mm-dd_HH-MM-ss.elg) - A log file containing debug information.
In version 2.0.6, we've added 3 new flags, which indicates whether to calculate and show the Threat/Access/NAT policy as part of the package (note all three default to true):
- --show-access-policy (true|false)
- --show-threat-policy (true|false)
- --show-nat-policy (true|false)
Instructions
This tool is hosted on GitHub repository for public use, containing a stand-alone executable Java JAR file (plug & play) and accompanied source code:
https://github.com/CheckPointSW/ShowPolicyPackage
Please follow the usage instructions and examples on this site. It contains valuable information.
P.S. This tool is also delivered along with R80 management server releases. However, the GitHub repository contains the most updated code!
Source Code Availability
The source code is now public on GitHub repository as mentioned above.
Questions?
We welcome your feedback! Please create a new thread.
NOTICE: By using this sample code you agree to terms and conditions in this Terms and Conditions
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Updated to version 2.0.6.
Also, thread is now locked, please create a new thread if you have questions related to this tool.
64 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Inbar,
Great workaround for the lack of R80 support for the previous Web Visualization Tools.
I would only suggest to clean-up the objects properties... seems to me that some information, such as uid, meta-info, is useless.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, this does not seem to work on R80.10 EA management. Getting massive Java exceptions. Any idea?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Valeri,
Can you please describe me the exceptions you are getting
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I will re-check tomorrow after EA being reinstate. Will let you know
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ignore my previous comments. found the error, it is working now
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Several notes (tested on R80.10 OS build 24, FW build 27):
1. Default package that comes with the OS installation generates java errors, need to copy over the attached one. It looks like the proper one is NOT included, as said below.
2. Need an option for automatic fingerprint accept, otherwise requires human CLI interaction
3. Links in index.html file are not working, can jump to neither NAT nore security policy files from the index.
4. Threat Prevention and Installed On files are not present at all
5. If ran without any flag, the tool dumps only one of multiple policy packages
6. Sub-rules are not shown at all
Summary: needs some work...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for posting this. RnD will contact you by email to assist.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
answered offline
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
not working on R80
Expert@cpmgmt:0]# installed_jumbo_take
R80 Jumbo Hotfix Accumulator take_76 is installed.
Error can be interpretted like incompatibility in api:
Jan 25, 2017 3:38:58 PM com.checkpoint.mgmt_api.examples.ShowRulebaseExample main
INFO: Management API 1
Jan 25, 2017 3:38:58 PM com.checkpoint.mgmt_api.examples.ShowRulebaseExample main
INFO: show_package v1.0
Jan 25, 2017 3:39:10 PM com.checkpoint.mgmt_api.examples.ShowRulebaseExample showVpnCommunities
SEVERE: Failed to run show-nat-rulebase command.Runtime error: com.checkpoint.objects.classes.dummy.CpmiSlimFwLogPolicy incompatible with com.checkpoint.objects.classes.dummy.CpmiLogPolicy
Jan 25, 2017 3:39:10 PM com.checkpoint.mgmt_api.examples.ShowRulebaseExample getPackageLayers
INFO: Access layers: Company_PROD_1_1 Security, Company_PROD_1_1 Application,
Jan 25, 2017 3:39:21 PM com.checkpoint.mgmt_api.examples.ShowRulebaseExample showAccessRulebase
SEVERE: Failed to run show-access-rulebase command (Company_PROD_1_1 Security): Runtime error: com.checkpoint.objects.classes.dummy.CpmiSlimFwLogPolicy incompatible with com.checkpoint.objects.classes.dummy.CpmiLogPolicy
Jan 25, 2017 3:39:55 PM com.checkpoint.mgmt_api.examples.ShowRulebaseExample showNATRulebase
SEVERE: Failed to run show-nat-rulebase command.Unexpected character ('"' (code 34)): was expecting comma to separate OBJECT entries
at [Source: {"offset" : 50, "limit" : 50"package :"Company_PROD_1_1,"details-level" : "full","use-object-dictionary" : true}; line: 1, column: 30]
Jan 25, 2017 3:39:56 PM com.checkpoint.mgmt_api.examples.ShowRulebaseExample main
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tomas,
Thank you for your comment!
We are aware of this bug, it is fixed in the next version of the Management Server.
The cause of the bug is that your Access/Nat policies contain a SMB (Slim) GW, which unfortunately is not handled properly by the Web API server of R-80 management.
-Igal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Getting an error...
Fingerprint was't approved. Error message: Parsing 'api fingerprint' response failed.
Script stopped running due to severe error!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sam,
Thank you for your comment!
I will contact you offline.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When running web_api_show_package.sh the -b argument needs to be included to avoid the fingerprint error on R80.
Also as noted earlier the version of this script included in R80 Take 76 blows up with a "Failed to run show-nat-rulebase command/Unexpected character" error, the files attached to this posting must be installed on the R80 SMS for it to work.
Incidentally, the version of this script that shipped with the latest R80.10 EA seems to work just fine with no updates, and the -b argument is not necessary for it to run successfully.
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That did the trick, thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a great tool thanks! Is there a way to also get the HTTPS inspection rules or could that be considered for the future?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Probably not with this script as the HTTPS Inspection rules aren't available through the R80 API yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was trying to get this to work on my R80 management box, and I got the following errors from the elg file in the generated tar.gz archive:
[Mon Jun 26 08:25:53 EDT 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: The parameters that were received:
[Mon Jun 26 08:25:53 EDT 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Limit number of object per page: 10
[Mon Jun 26 08:25:53 EDT 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Local Ips: [10.xxx.xxx.xxx, 127.0.0.1]
[Mon Jun 26 08:25:55 EDT 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Login As root: true
[Mon Jun 26 08:25:55 EDT 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Login with 'read-only' flag.
[Mon Jun 26 08:25:55 EDT 2017 com.checkpoint.mgmt_api.examples.MyLogger.severe()SEVERE]: An error occurred while logging in to the server Can't read API external port
[Mon Jun 26 08:25:55 EDT 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.logoutReportAndExit()INFO]: Script stopped running due to severe error!
[Mon Jun 26 08:25:55 EDT 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.logoutReportAndExit()INFO]: dirPath: /home/admin/showpackage/f218e1d4-5663-4a98-8f60-c6e3bb591cce
[Mon Jun 26 08:25:55 EDT 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.logoutReportAndExit()INFO]: tarGzPath: show_package-2017-06-26_08-25-52.tar.gz
Turns out I had to run this while at /home/admin.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What about IPS Exceptions? Seems the script has a problem pulling the IPS policies.
We get this error:
[Wed Jun 21 21:20:21 BRT 2017 com.checkpoint.mgmt_api.examples.MyLogger.warning()WARNING]: Failed to run show-threat-rulebase command ('IPS'): Message: 'Requested object [e84e4261-60e6-fb4e-85a9-57d32d2a7d4e] not found'. Status Code: '404'. probably IPS does not exist - continue
This IPS policy is there and we see later in the logs that it tries to pull the Exceptions:
[Wed Jun 21 21:20:22 BRT 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Run command: 'show-threat-rule-exception-rulebase' for threat layer: 'Border_Policy Threat Prevention' ('d1293b76-36c3-bb44-b02f-6fae624c96a0') with details level 'full'
However, it's not pulling anything. The IPS html page gives you this:
IPS
Domain: XXXXXXXXXX
Package: Shared across all policy packages
Layer: IPS (threat-prevention layer)
Failed to create layer. For more information, please refer to the log file in the output tar file.
Is this a known bug with the API or script?
Thanks.
Robert.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a MDM server in the test environment and imported the configuration from the production environment. When I run the show package tool I will get the error that the packages found were not installed on a gateway.
I run it on a CMA (trusted) but get more or less the same error when I run it on the MDM itself.
[Expert@MDM01:0]# ./web_api_show_package.sh -d Trusted
More than one package exists but neither one of them is installed on a gateway.
In order to show a specific package, run with -k [package name].
In order to show all the existing packages, run with -v
Script finished running successfully!
Result file location: show_package-2017-08-15_03-54-00.tar.gz
[Expert@MDM01:0]# tar -tvf show_package-2017-08-15_03-54-00.tar.gz
-rw-r--r-- 0/0 3848 2017-08-15 15:54:24 show_package-2017-08-15_03-54-00.elg
-rw-r--r-- 0/0 6926 2017-08-15 15:54:22 index.html
-rw-r--r-- 0/0 41 2017-08-15 15:54:22 index.json
[Expert@MDM01:0]# more show_package-2017-08-15_03-54-00.elg
[Tue Aug 15 15:54:01 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: The parameters that were received: domain:(-d)=Trusted
[Tue Aug 15 15:54:01 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Limit number of object per page: 10
[Tue Aug 15 15:54:01 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Local Ips: [172.29.121.153, 172.29.121.155, 172.29.121.154, 172.29.121.156, 127.0.0.1]
[Tue Aug 15 15:54:03 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Login As root: true
[Tue Aug 15 15:54:03 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Login with 'read-only' flag.
[Tue Aug 15 15:54:04 CEST 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.writeTheVersionsToTheLogger()INFO]: Management API running version: 1.1
[Tue Aug 15 15:54:04 CEST 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.writeTheVersionsToTheLogger()INFO]: show_package v1.1.3
[Tue Aug 15 15:54:04 CEST 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.writeTheVersionsToTheLogger()INFO]: Chosen port: 443
[Tue Aug 15 15:54:04 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Chosen server IP: 127.0.0.1
[Tue Aug 15 15:54:04 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Login response: {"api-server-version":"1.1","last-login-was-at":{"iso-8601":"2017-08-15T15:31+0200","posix":1502803879},"standby":false,"read-only":true,"url":"https:\/\/127.0.0.1:443\/web_api","sid":"5ry-lWVEKbEqs_Hk4JgFhOLPXKHTf3hYpQlDedx_mdw"}
[Tue Aug 15 15:54:04 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Run command: 'show-gateways-and-servers' with details level 'full'
[Tue Aug 15 15:54:13 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Found 47 gateways from 'show-gateways-and-servers'
[Tue Aug 15 15:54:13 CEST 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.collectGatewaysInUseAndInstalledPolicies()INFO]: Found 0 gateways that have a policy installed on them
[Tue Aug 15 15:54:13 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Run command: 'show-vpn-communities-star' with details level 'full'
[Tue Aug 15 15:54:13 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Run command: 'show-vpn-communities-meshed' with details level 'full'
[Tue Aug 15 15:54:14 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Found 2 vpn communities
[Tue Aug 15 15:54:14 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Run command: 'show-packages' with details level 'full'
[Tue Aug 15 15:54:22 CEST 2017 com.checkpoint.mgmt_api.examples.MyLogger.debug()DEBUG]: Found 23 packages
[Tue Aug 15 15:54:22 CEST 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.showPackages()INFO]: Packages which were found on the management: [BT--FRW28-Wota, BT--FRW45_VSX, BT-BX--FRW11-12-GPD-oranje, BT-BX--FRW24-RI, BT-BX--FRW38-39-RC, BT-BX--FRW43-44_VSX, BT-BX-OTA-P-scheiding-Perform, BT-BX-WS-Beheer-HP, BT-FRW1-2-Simpel, BT-FRW1-2-Test, BT-FRW1-2-Test_Traditional, Default-NG, GANBHR, GENLB, INF-WIFI, IPTBHR, ISBHR, OPS, STORBHR-EMC, test-bt--frw98-99, test-mark, zDeletedRules-Dummy, ZT--FRW35-Testnetwerk]
[Tue Aug 15 15:54:22 CEST 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.showPackages()INFO]: Packages which were installed on gateways: []
[Tue Aug 15 15:54:24 CEST 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.logoutReportAndExit()INFO]: Script finished running successfully!
[Tue Aug 15 15:54:24 CEST 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.logoutReportAndExit()INFO]: dirPath: /opt/CPsuite-R80/fw1/scripts/f4fa6147-04e9-4679-8cd2-32b2399e6e6e
[Tue Aug 15 15:54:24 CEST 2017 com.checkpoint.mgmt_api.examples.ShowPackageTool.logoutReportAndExit()INFO]: tarGzPath: show_package-2017-08-15_03-54-00.tar.gz
When I try it on a package it works : [Expert@MDM01:0]# ./web_api_show_package.sh -d Trusted -k BT--FRW28-Wota
Script finished running with warnings!
Result file location: show_package-2017-08-15_04-10-22.tar.gz
[ExpertMDM01:0]# tar -tvf show_package-2017-08-15_04-10-22.tar.gz
-rw-r--r-- 0/0 1434330 2017-08-15 16:12:41 BT--FRW28-Wota_objects.html
-rw-r--r-- 0/0 95956 2017-08-15 16:12:39 BT--FRW28-Wota NAT-Trusted.json
-rw-r--r-- 0/0 8479 2017-08-15 16:12:41 index.html
-rw-r--r-- 0/0 240001 2017-08-15 16:12:33 BT--FRW28-Wota Security-Trusted.html
-rw-r--r-- 0/0 1233 2017-08-15 16:10:41 BT--FRW28-Wota Application-Trusted.json
-rw-r--r-- 0/0 136998 2017-08-15 16:12:39 BT--FRW28-Wota NAT-Trusted.html
-rw-r--r-- 0/0 1594 2017-08-15 16:12:41 index.json
-rw-r--r-- 0/0 43577 2017-08-15 16:10:41 Generiek_Trusted Security-Global.html
-rw-r--r-- 0/0 200914 2017-08-15 16:12:33 BT--FRW28-Wota Security-Trusted.json
-rw-r--r-- 0/0 10255 2017-08-15 16:12:47 show_package-2017-08-15_04-10-22.elg
-rw-r--r-- 0/0 42222 2017-08-15 16:12:41 BT--FRW28-Wota Threat Prevention-Trusted.html
-rw-r--r-- 0/0 17466 2017-08-15 16:10:41 Generiek_Trusted Security-Global.json
-rw-r--r-- 0/0 0 2017-08-15 16:12:40 IPS-Trusted.json
-rw-r--r-- 0/0 41040 2017-08-15 16:12:40 IPS-Trusted.html
-rw-r--r-- 0/0 27450 2017-08-15 16:10:41 BT--FRW28-Wota Application-Trusted.html
-rw-r--r-- 0/0 979 2017-08-15 16:12:41 BT--FRW28-Wota Threat Prevention-Trusted.json
-rw-r--r-- 0/0 1429184 2017-08-15 16:12:41 BT--FRW28-Wota_objects.json
Does anyone know how to solve this issue ? As far as I understood it should be possible to run the script from the MDM and from every domain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Mark,
In a default case only packages that there policy is installed on gateway will be shown.
In order to see policy that is not installed on gateway use -k flag.
Inbar Moskovich.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Inbar,
I have made an export from our production environment (where all the policy’s are installed on the different gateways) and imported this configuration into our test MDM environment. When I run the show_package script there I get the result as described. I would expect that it should recognize that the policy’s are installed because that’s the case in the production environment. How does the script test if the policy is installed ?
Does it really connect to the different gateways (I can hardly believe that) or does the script just look for a compiled policy ?
Is the way I use the script a supported way, or are you just able to run it in the environment where the actual gateways are in ?
Regards,
Mark
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I found the problem. There were no compiled policy files after the export/import from R77.20 to R80.10. After I pushed some policy's in our testenvironment the script works fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Where can you get the 1.1.4 version of the code? The link above seems to provide the 1.1.3 version still (or the code didn't increment the version number.).
$ java -jar ./jar/web_api_show_package-jar-with-dependencies.jar -h
show-package version: v1.1.3
web_api_show_package.sh optional-switches
optional-switches:
---------------
[-m server-IP]
....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Aaron,
This is the 1.1.4 version of the code, the code didn't increment the version number.
Thank you for your comment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
On gaia 77.30, We used to cpdb2web to export our policy to xml and then we execute a tool to list and test firewall rules. (https://sourcesup.renater.fr/projects/jtacl/)
What is the best way to reproduce this with show_package script ?
It doesn't look like to be xml compatible.
Extraction duration of the the policy is about 10 times long than with precedent tool.
Any tips would be apreciate as we can't use our analysis tool from a month now ;(
Kinds regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Fabrice,
Currently the supported formats are html, json and csv:
The show package tool exports the data in html and json formats.
The ExportImportPolicyPackage exports the data in csv format.
Regards,
Inbar
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The source code is now an open source on GitHub repository:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi https://community.checkpoint.com/people/rdeck5af054c0-4c71-4395-9c31-2a794ff5bc37
I've used this script to export my Inline Policy package and did not get any error. But when I open the export html file it only shows the Parent rules.
Is this a known limitation?
Thanks,
Nader
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Nader,
The display over HTML is modular.
The main page displayes the parent layer rules -
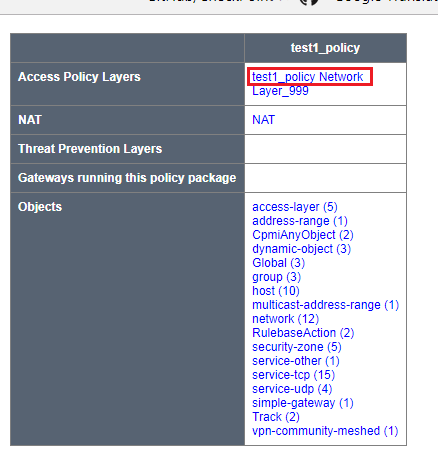

The "Action" column indicates whether it is an inline layer. If you click on the link, you will navigate to the rules of that inline layer -
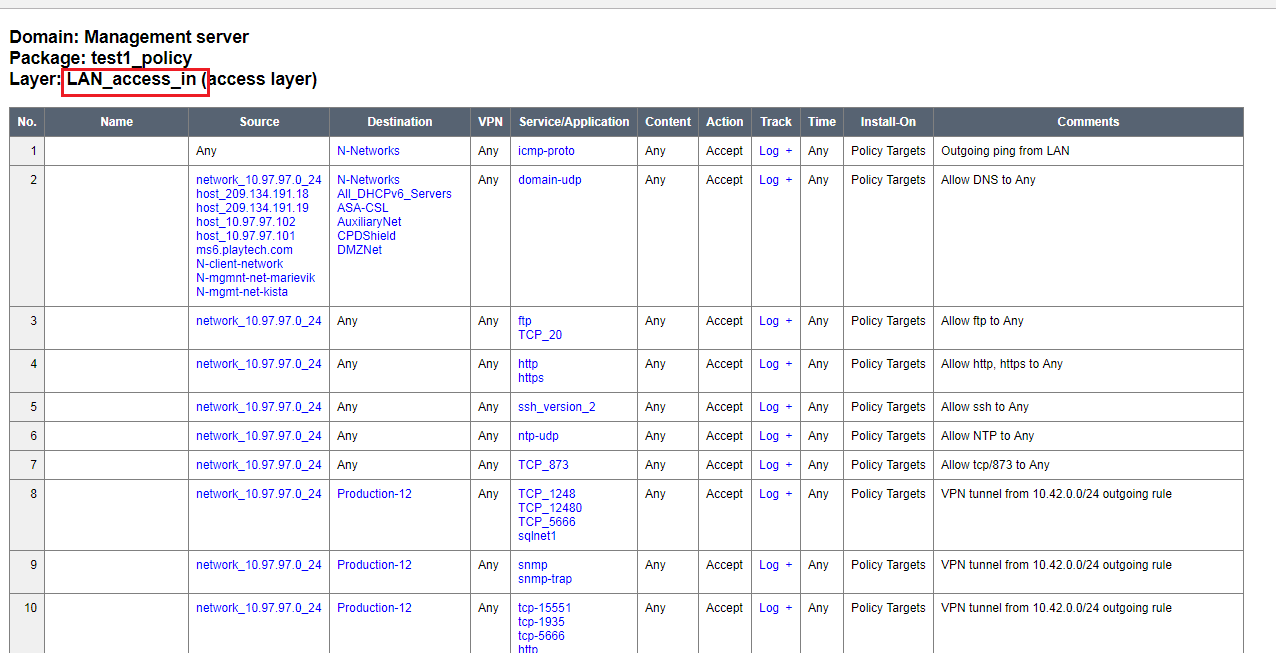
Hope that this clarifies how the tool works.
Robert.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 05:00 PM (CEST)
SASE Masters: Deploying Harmony SASE for a 6,000-Strong Workforce in a Single WeekendAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center


