- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Mastering Compliance
Unveiling the power of Compliance Blade
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
May the 4th (+4)
Navigating Paradigm Shifts in Cyber
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
CPX 2024 Recap
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- Re: Security Gateway Inventory
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Security Gateway Inventory
About 6 months ago, CP gave us a script to run from Provider 1 to grab all gateways and their corresponding model/software version. However, it was a very inconsistent result. Meaning that, some (active) gateways came back with just host name and IP and then some came back with host name/IP/OS Version/model number.
Anybody aware of a way to pull : Gateway Info that includes (Hostname/IP/OS-Version/Model)? I know you can export a list through network objects, but I just want active count for inventory. Any such method/script?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Small update 27th Sep 2018 - added MAC address of Mgmt interface as requested
I got little curious since no one replied ![]()
I have only tested it with R77.30, R80.10 and R76 (chassis ver) and CP appliances...
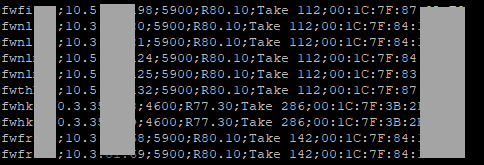
You get semicolon separated text like this - you can format it better if you need to
You run it on MDS - it's fairly slow but I wanted to keep it as simple as possible.
Script will use cpmiquerybin to fetch all physical gateways from all CMAs and then cprid_util to run some commands to collect numbers, so it's fully autonomos - does not need any input nor extra usernames/port openings etc
I've added ugly HTML version now too in output.html
#!/bin/bash
. /opt/CPshared/5.0/tmp/.CPprofile.sh
if [ -f logfile ]; then rm logfile; fi
echo '<!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01//EN" "http://www.w3.org/TR/html4/strict.dtd">' > output.html
echo '<html><head><title>Gateway Versions</title></head><body><font size="-1"><table style="text-align: left; width: 100%; font-family: Helvetica,Arial,sans-serif;" border="1" cellpadding="5" cellspacing="2"><tbody>' >> output.html
echo '<tr style="font-weight: bold; background-color: rgb(0, 0, 102); color: white;"><td>GW</td><td>IP</td><td>MODEL</td><td>MAJOR</td><td>TAKE</td><td>MAC</td></tr>' >> output.html
for CMA_NAME in $($MDSVERUTIL AllCMAs); do mdsenv $CMA_NAME; echo "CMA $CMA_NAME"; cpmiquerybin attr "" network_objects " (type='cluster_member' & vsx_cluster_member='true' & vs_cluster_member='true') | (type='cluster_member' & (! vs_cluster_member='true')) | (vsx_netobj='true') | (type='gateway'&cp_products_installed='true' & (! vs_netobj='true') & connection_state='communicating')" -a __name__,ipaddr; done 1>> logfile 2>> logfile
while read line; do
if [ `echo "$line" | grep -c ^CMA` -gt 0 ]; then
CMA_NAME=`echo "$line" | awk '{print $2}'`
mdsenv $CMA_NAME
else
GW=`echo "$line" | awk '{print $1}'`
IP=`echo "$line" | awk '{print $2}'`
MODEL=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd /bin/clish -s -c 'show asset system' | grep ^Model | awk -F: '{print $2}' | sed 's/ Check Point //'`
# Fix for chassis
if [ "x$MODEL" = "x" ]; then MODEL=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "dmiparse System Product"`; if [ "x$MODEL" = "xA-40" ]; then MODEL="41000"; fi; fi
TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "grep 'was installed successfully' /opt/CPInstLog/DA_UI.log" | egrep "Image|Jumbo|Upgrade|Bundle_T" | tail -1 | sed 's/Take/#/' | sed 's/was/#/' | sed 's/)//' | awk -F# '{print "Take"$2}' | xargs`
# Fix for earlier releases or when take cannot be read from DA logs
if [ "x$TAKE" = "x" ]; then TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "cpinfo -y FW1" | grep HOTFIX | tail -1 | awk '{print $1}'`; fi
# Fix for manually imported package installations
if [ `echo $TAKE | wc -w` -gt 2 ]; then TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "grep 'was installed successfully' /opt/CPInstLog/DA_UI.log" | egrep "Bundle_T" | tail -1 | sed 's/_T/#T/' | awk -F# '{print $2}' | sed 's/_/ /' | sed 's/T//' |awk '{print "Take "$1}'`; fi
MAJOR=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "fw ver" | sed 's/This is Check Point VPN-1(TM) & FireWall-1(R) //' | sed "s/This is Check Point's software version //" | awk '{print $1}'`
MAC=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "ifconfig -a" | egrep "Mgmt|Internal|eth0" | head -1 | awk '{print $5}'`
echo "$GW;$IP;$MODEL;$MAJOR;$TAKE;$MAC"
echo "<tr><td>$GW</td><td>$IP</td><td>$MODEL</td><td>$MAJOR</td><td>$TAKE</td><td>$MAC</td></tr>" >> output.html
fi
done < logfile
echo '</tbody></table><br></body></html>' >> output.html
78 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Small update 27th Sep 2018 - added MAC address of Mgmt interface as requested
I got little curious since no one replied ![]()
I have only tested it with R77.30, R80.10 and R76 (chassis ver) and CP appliances...
You get semicolon separated text like this - you can format it better if you need to

You run it on MDS - it's fairly slow but I wanted to keep it as simple as possible.
Script will use cpmiquerybin to fetch all physical gateways from all CMAs and then cprid_util to run some commands to collect numbers, so it's fully autonomos - does not need any input nor extra usernames/port openings etc
I've added ugly HTML version now too in output.html

#!/bin/bash
. /opt/CPshared/5.0/tmp/.CPprofile.sh
if [ -f logfile ]; then rm logfile; fi
echo '<!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01//EN" "http://www.w3.org/TR/html4/strict.dtd">' > output.html
echo '<html><head><title>Gateway Versions</title></head><body><font size="-1"><table style="text-align: left; width: 100%; font-family: Helvetica,Arial,sans-serif;" border="1" cellpadding="5" cellspacing="2"><tbody>' >> output.html
echo '<tr style="font-weight: bold; background-color: rgb(0, 0, 102); color: white;"><td>GW</td><td>IP</td><td>MODEL</td><td>MAJOR</td><td>TAKE</td><td>MAC</td></tr>' >> output.html
for CMA_NAME in $($MDSVERUTIL AllCMAs); do mdsenv $CMA_NAME; echo "CMA $CMA_NAME"; cpmiquerybin attr "" network_objects " (type='cluster_member' & vsx_cluster_member='true' & vs_cluster_member='true') | (type='cluster_member' & (! vs_cluster_member='true')) | (vsx_netobj='true') | (type='gateway'&cp_products_installed='true' & (! vs_netobj='true') & connection_state='communicating')" -a __name__,ipaddr; done 1>> logfile 2>> logfile
while read line; do
if [ `echo "$line" | grep -c ^CMA` -gt 0 ]; then
CMA_NAME=`echo "$line" | awk '{print $2}'`
mdsenv $CMA_NAME
else
GW=`echo "$line" | awk '{print $1}'`
IP=`echo "$line" | awk '{print $2}'`
MODEL=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd /bin/clish -s -c 'show asset system' | grep ^Model | awk -F: '{print $2}' | sed 's/ Check Point //'`
# Fix for chassis
if [ "x$MODEL" = "x" ]; then MODEL=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "dmiparse System Product"`; if [ "x$MODEL" = "xA-40" ]; then MODEL="41000"; fi; fi
TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "grep 'was installed successfully' /opt/CPInstLog/DA_UI.log" | egrep "Image|Jumbo|Upgrade|Bundle_T" | tail -1 | sed 's/Take/#/' | sed 's/was/#/' | sed 's/)//' | awk -F# '{print "Take"$2}' | xargs`
# Fix for earlier releases or when take cannot be read from DA logs
if [ "x$TAKE" = "x" ]; then TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "cpinfo -y FW1" | grep HOTFIX | tail -1 | awk '{print $1}'`; fi
# Fix for manually imported package installations
if [ `echo $TAKE | wc -w` -gt 2 ]; then TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "grep 'was installed successfully' /opt/CPInstLog/DA_UI.log" | egrep "Bundle_T" | tail -1 | sed 's/_T/#T/' | awk -F# '{print $2}' | sed 's/_/ /' | sed 's/T//' |awk '{print "Take "$1}'`; fi
MAJOR=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "fw ver" | sed 's/This is Check Point VPN-1(TM) & FireWall-1(R) //' | sed "s/This is Check Point's software version //" | awk '{print $1}'`
MAC=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "ifconfig -a" | egrep "Mgmt|Internal|eth0" | head -1 | awk '{print $5}'`
echo "$GW;$IP;$MODEL;$MAJOR;$TAKE;$MAC"
echo "<tr><td>$GW</td><td>$IP</td><td>$MODEL</td><td>$MAJOR</td><td>$TAKE</td><td>$MAC</td></tr>" >> output.html
fi
done < logfile
echo '</tbody></table><br></body></html>' >> output.html- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Kaspars,
Was this script supposed to be ran in a special way? When attempting to run this I kept receiving an error regarding the command " AllCMAs". Is this specific command on a certain version of hotfix or a special add in etc? I am new to the Check Point scripting world so forgive me if the question is a little newbish.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you running MDS or regular management server? That command and script itself is meant for MDS type management.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You know this means I have to move this thread to https://community.checkpoint.com/community/developers?sr=search&searchId=0678ff86-08f7-4a64-86d4-c86..., right? ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Updated script to process manually imported jumbo hotfix packages
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Kaspars.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tried to run your script on my MDS , getting the following error's
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
get_detail_list_of_gw_from_provider.sh:;line;;;;
get_detail_list_of_gw_from_provider.sh: line 14: mdsenv: command not found
file
more get_detail_list_of_gw_from_provider.sh
if [ -f logfile ]; then rm logfile; fi
echo '<!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01//EN" "http://www.w3.org/TR/html4/strict.dtd">' > output.html
echo '<html><head><title>Gateway Versions</title></head><body><font size="-1"><table style="text-align: left; width: 100%; font-family: Helvetica,Arial,sans-serif;" border="1" cellpadding="5" cellspacing="2"><tbody>' >> output.html
echo '<tr style="font-weight: bold; background-color: rgb(0, 0, 102); color: white;"><td>GW</td><td>IP</td><td>MODEL</td><td>MAJOR</td><td>TAKE</td><td>MAC</td></tr>' >> output.html
for CMA_NAME in $($MDSVERUTIL AllCMAs); do mdsenv $CMA_NAME; echo "CMA $CMA_NAME"; cpmiquerybin attr "" network_objects " (type='cluster_member' & vsx_cluster_member='true' & vs_cluster_member='true') | (type='cluster_member' & (! vs_clus
ter_member='true')) | (vsx_netobj='true') | (type='gateway'&cp_products_installed='true' & (! vs_netobj='true') & connection_state='communicating')" -a __name__,ipaddr; done 1>> logfile 2>> logfile
while read line; do
if [ `echo "$line" | grep -c ^CMA` -gt 0 ]; then
CMA_NAME=`echo "$line" | awk '{print $2}'`
mdsenv $CMA_NAME
else
GW=`echo "$line" | awk '{print $1}'`
IP=`echo "$line" | awk '{print $2}'`
MODEL=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd /bin/clish -s -c 'show asset system' | grep ^Model | awk -F: '{print $2}' | sed 's/ Check Point //'`
# Fix for chassis
if [ "x$MODEL" = "x" ]; then MODEL=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "dmiparse System Product"`; if [ "x$MODEL" = "xA-40" ]; then MODEL="41000"; fi; fi
TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "grep 'was installed successfully' /opt/CPInstLog/DA_UI.log" | egrep "Image|Jumbo|Upgrade|Bundle_T" | tail -1 | sed 's/Take/#/' | sed 's/was/#/' | sed 's
/)//' | awk -F# '{print "Take"$2}' | xargs`
# Fix for earlier releases or when take cannot be read from DA logs
if [ "x$TAKE" = "x" ]; then TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "cpinfo -y FW1" | grep HOTFIX | tail -1 | awk '{print $1}'`; fi
# Fix for manually imported package installations
if [ `echo $TAKE | wc -w` -gt 2 ]; then TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "grep 'was installed successfully' /opt/CPInstLog/DA_UI.log" | egrep "Bundle_T" | tail -1 | sed 's/_T/#T/' | awk
-F# '{print $2}' | sed 's/_/ /' | sed 's/T//' |awk '{print "Take "$1}'`; fi
MAJOR=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "fw ver" | sed 's/This is Check Point VPN-1(TM) & FireWall-1(R) //' | sed "s/This is Check Point's software version //" | awk '{print $1}'`
MAC=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "ifconfig -a" | egrep "Mgmt|Internal|eth0" | head -1 | awk '{print $5}'`
echo "$GW;$IP;$MODEL;$MAJOR;$TAKE;$MAC"
echo "<tr><td>$GW</td><td>$IP</td><td>$MODEL</td><td>$MAJOR</td><td>$TAKE</td><td>$MAC</td></tr>" >> output.html
fi
done < logfile
echo '</tbody></table><br></body></html>' >> output.html
any ideals why?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the output of
$MDSVERUTIL AllCMAs
?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have created a bunch of scripts that we use to check all kinds of stuff on our managed gateways, but provide our script with a list of hosts to use instead of collecting the systems from a management-server.
To gather the information, we use SSH with certificates to access the devices. It gets the following information from the systems:
Hostname, CP-version (major & minor), cluster-status, secureXL status, uptime, if DNS and NTP are working and if the time is set correctly, if stateful inspection is on or off, the age of the AntiBot/AntiVirus/IPS/Appl/URLf-databases, the size of /var/log/messages (if this is still the default size, it will set it to 10x2MB), if the system is 32 or 64-bit, CPUSE-version, if the box is licensed, the model and the serial number.
The scripts are rather ugly put together, but get the job done and are run on a nightly basis.
The gathered intel is written to a file, so it can be read by other processes and can be used with information we gathered from other vendors' equipment that we manage for customers.
This is combined with information of the expiration-date of VPN-certificates and the version-database we compiled ourselves and this is presented on a web-server, so we have a full overview of (almost) all systems we manage and can do this without the use of SNMP.
The use of SSH that runs over a list of systems to check is a more general way of gathering information about the systems we manage, but a lot quicker than cprid_util (which we do use, but only to gather info on SMB-devices that don't do scripts).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We run everything using bash scripts and SSH
+ Key login ourselves. This suggestion was just a simple solution if you have neither in place. Not the fastest but works without installing SSH keys or adding rules for SSH access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I give you 100 points for this script.
Nice!
Thanks
Heiko
➜ CCSM Elite, CCME, CCTE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Kaspars,
First of all thank you for this script, it really helped a lot for our inventory and to know the current OS config'd. 🙂
This script fails for SMB (embedded GAIA platform), so is there a solution in pipeline for it? or someone already found it? It will be really helpful as my company have 300+ SMB gateways like starting from 11xx to 15xx.
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
this one is working with Gaia Embedded 1400 series. It's reporting IP,hostname,version,take version,ips status.
In case of 1100 series appliancies you need to adjust line line #25 with MAJOR and put there another lines like this:
sed "s/This is Check Point's 1100 Appliance //"
#!/bin/sh
source /var/opt/CPshrd-R80.30/tmp/.CPprofile.sh
if [ -f logfile ]; then rm logfile; fi
file_name="$(date +"%m-%d-%Y")-patching.csv"
for CMA_NAME in $($MDSVERUTIL AllCMAs); do mdsenv $CMA_NAME; echo "CMA $CMA_NAME"; cpmiquerybin attr "" network_objects " (type='cluster_member' & vsx_cluster_member='true' & vs_cluster_member='true') | (type='cluster_member' & (! vs_cluster_member='true')) | (vsx_netobj='true') | (type='gateway'&cp_products_installed='true' & (! vs_netobj='true') & connection_state='communicating')" -a __name__,ipaddr; done 1>> logfile 2>> logfile
while read line; do
if [ `echo "$line" | grep -c ^CMA` -gt 0 ]; then
CMA_NAME=`echo "$line" | awk '{print $2}'`
mdsenv $CMA_NAME
else
GW=`echo "$line" | awk '{print $1}'`
IP=`echo "$line" | awk '{print $2}'`
TAKE=`$CPDIR/bin/cprid_util -timeout 5 -server $IP -verbose rexec -rcmd bash -c "grep 'was installed successfully' /opt/CPInstLog/DA_UI.log" | egrep "Image|Jumbo|Upgrade|Bundle_T" | tail -1 | sed 's/Take/#/' | sed 's/was/#/' | sed 's/)//' | awk -F# '{print "Take"$2}'`
#Fix for manually imported package installations
if [ `echo $TAKE | wc -w` -gt 2 ]; then TAKE=`$CPDIR/bin/cprid_util -timeout 5 -server $IP -verbose rexec -rcmd bash -c "grep 'was installed successfully' /opt/CPInstLog/DA_UI.log" | egrep "Bundle_T" | tail -1 | sed 's/_T/#T/' | awk -F# '{print $2}' | sed 's/_/ /' | sed 's/T//' |awk '{print "Take "$1}'`; fi
MAJOR=`$CPDIR/bin/cprid_util -timeout 10 -server $IP -verbose rexec -rcmd bash -c "fw ver" | sed 's/This is Check Point VPN-1(TM) & FireWall-1(R) //' | sed "s/This is Check Point's software version //" | sed "s/This is Check Point's 1490 Appliance //" | sed "s/This is Check Point's 1430 Appliance //" | sed "s/This is Check Point's 1450 Appliance //" | sed "s/This is Check Point's 1470 Appliance //" | awk '{print $1}'`
if [ "x$MAJOR" = "x" ]; then MAJOR=`$CPDIR/bin/cprid_util -timeout 5 -server $IP -verbose rexec -rcmd bash -c "fw ver" | awk '{print $7}'` ; fi
#echo "$IP;$GW;$CMA_NAME,$MAJOR;$TAKE\n"
IPS_STATUS=`$CPDIR/bin/cprid_util -timeout 5 -server $IP -verbose rexec -rcmd bash -c 'ips stat | grep -E "(Enabled|enabled)"'`
if [ "x$IPS_STATUS" = "x" ];
then IPS_STATUS="0"
else IPS_STATUS="1";fi
echo "$IP,$GW,$MAJOR,$TAKE,$IPS_STATUS" >> file_name
fi
done < logfile
#rm -f $file_name- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Martin,
Thank you and indeed it helped. However is there a way to get the model details of each appliance (probably adding the command to fetch from each gateway) using same script.Our MDS details are not trustful on what real model the appliance is unless we login to specific gateway and check it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you need exact model types or just series? Appliancies series are visible on gateways&servers tab, when you filter or when you export list of it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Exact model will be helpful. Our firewall resources just select whichever is the nearest model say for eg: if they have 5000 series they even select 4000 series in Smart Console or for a 1400 they might select 1100, which makes us tough to know the actual series plus model.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This version mismatch should not happend, there is some verification in background i believe, anyway Model of device you can pull via SNMP, this is most effecient method how to pull this over all gateways no matter if it's GAIA OS or Gaia Embedded.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm sure there is a way to get actual model from SMB appliances too but I'm afraid I have no access to those, so you're on your own here 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
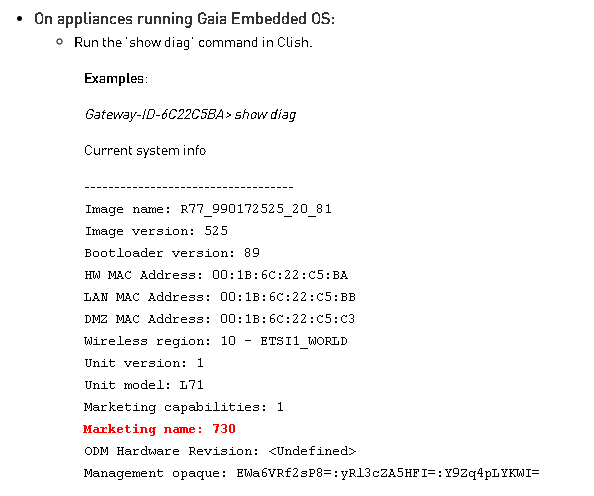
I just found this from SK37692, so you should be able to use that with the original script and grep for info
something like line below and add it to the output
MODEL=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd /bin/clish -s -c 'show diag' | grep ^Marketing | awk '{print $3}'`
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you. For some reason the script is not getting any output for model even after adding the one you recommended.
I tried with below,
MODEL=`$CPDIR/bin/cprid_util -timeout 5 -server $IP -verbose rexec -rcmd bash -c "fw ver" | awk '{print $5}'`
However some Checkpoint models have output like below which we get expected appliance model
This is Check Point's 1550 Appliance RXX- Build XXX
Some models will have output different than above for the same command (fw ver) 😡
This is Check Point's software version RXX - Build XX
Also one point I found that some models don't have "show diag" command (unsure why) and even if its there, it show as Marketing Name as <Undefined>. 🙄
Overall, thank you for Kaspars and Martin for helping me out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
For those who have GAiA and GAiA Embedded (SMB) firewalls you can use this script.
Model, version and MAC work properly.
#!/bin/bash
#
# Security Gateway Inventory - Bash script for Check Point Multi-Domain Servers (MDS)
#
# Script Author : Kaspars Zibarts
# Script Source : https://community.checkpoint.com/t5/API-CLI-Discussion-and-Samples/Security-Gateway-Inventory/td-p/32547
if [[ -e /etc/profile.d/CP.sh ]]; then source /etc/profile.d/CP.sh; else echo "Unsupported Environment"; exit 1; fi
if ! [[ `echo $MDSDIR | grep mds` ]]; then echo "Not a Multi-Domain Server (MDS)!"; exit 1; fi
echo 'Script started on '$(date "+%Y-%m-%d @ %H:%M") >> logfile
if [[ -f output.html ]]; then mv output.html output_$(date -r output.html "+%Y-%m-%d_%H-%M-%S").html; fi
echo '<!DOCTYPE html>' > output.html
echo '<html lang="en"><head><title>Gateway Versions - '$(date "+%Y-%m-%d @ %H:%M")'</title></head><body><font size="-1"><table style="text-align: left; width: 100%; font-family: Helvetica,Arial,sans-serif;" border="1" cellpadding="5" cellspacing="2"><tbody>' >> output.html
echo '<tr style="font-weight: bold; background-color: rgb(0, 0, 102); color: white;"><td>CMA</td><td>GW</td><td>IP</td><td>MODEL</td><td>MAJOR</td><td>TAKE</td><td>MAC</td></tr>' >> output.html
for CMA_NAME in $($MDSVERUTIL AllCMAs); do
mdsenv $CMA_NAME; echo "CMA $CMA_NAME"; cpmiquerybin attr "" network_objects " (type='cluster_member' & vsx_cluster_member='true' & vs_cluster_member='true') | (type='cluster_member' & (! vs_cluster_member='true')) | (vsx_netobj='true') | (type='gateway'&cp_products_installed='true' & (! vs_netobj='true') & connection_state='communicating')" -a __name__,ipaddr;
done 1>> logfile 2>> logfile
while read line; do
if [ `echo "$line" | grep -c ^CMA` -gt 0 ]; then
CMA_NAME=`echo "$line" | awk '{print $2}'`
mdsenv $CMA_NAME
else
GW=`echo "$line" | awk '{print $1}'`
IP=`echo "$line" | awk '{print $2}'`
MODEL=`$CPDIR/bin/cprid_util -timeout 5 -server $IP -verbose rexec -rcmd bash -c "fw ver" | awk '{print $5}'`
if [ "$MODEL" = "software" ]; then
MODEL=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd /bin/clish -s -c 'show asset system' | grep ^Model | awk -F: '{print $2}' | sed 's/ Check Point //'`
fi
# Fix for chassis
if [ "x$MODEL" = "x" ]; then
MODEL=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "dmiparse System Product"`
if [ "x$MODEL" = "xA-40" ]; then MODEL="41000"; fi
fi
# Get Take version
TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "grep 'was installed successfully' /opt/CPInstLog/DA_UI.log" | egrep "Image|Jumbo|Upgrade|Bundle_T" | tail -1 | sed 's/Take/#/' | sed 's/was/#/' | sed 's/)//' | awk -F# '{print "Take"$2}' | xargs`
# Fix for earlier releases or when take cannot be read from DA logs
if [ "x$TAKE" = "x" ]; then TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "cpinfo -y FW1" | grep HOTFIX | tail -1 | awk '{print $1}'`; fi
# Fix for manually imported package installations
if [ `echo $TAKE | wc -w` -gt 2 ]; then TAKE=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "grep 'was installed successfully' /opt/CPInstLog/DA_UI.log" | egrep "Bundle_T" | tail -1 | sed 's/_T/#T/' | awk -F# '{print $2}' | sed 's/_/ /' | sed 's/T//' |awk '{print "Take "$1}'`; fi
MAJOR=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "fw ver" | sed 's/This is Check Point VPN-1(TM) & FireWall-1(R) //' | sed "s/This is Check Point's software version //" | sed 's/^.*Appliance //' | awk '{print $1}'`
MAC=`$CPDIR/bin/cprid_util -server $IP -verbose rexec -rcmd bash -c "ifconfig -a" | egrep "Mgmt|Internal|eth0|WAN" | head -1 | awk '{print $5}'`
echo "$CMA_NAME;$GW;$IP;$MODEL;$MAJOR;$TAKE;$MAC"
echo "<tr><td>$CMA_NAME</td><td>$GW</td><td>$IP</td><td>$MODEL</td><td>$MAJOR</td><td>$TAKE</td><td>$MAC</td></tr>" >> output.html
fi
done < logfile
echo '</tbody></table><br></body></html>' >> output.html
echo 'Done. HTML output saved in output.html'
exit 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Does this script works in R81? For some reason its not working in R81, but fine in R80.30.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We haven't upgraded to R81 yet 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear,
Thanks for your script. I'm desperately looking for the same output for a management server NOT using MDS. Do you have another script that would work on a simple management server ? I've searched all over the place, but all clues redirect to this thread which doesn't really apply to my situation.
Thanks in advance !
Regards,
Antoine
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Is this still good for R80.40? The script throws out the following:
[Expert@MDS-P1:0]# tailf /home/admin/logfile
cma_all.sh: line 9: mdsenv: command not found
CMA FIRST_CMA
cma_all.sh: line 9: mdsenv: command not found
CMA ANOTHER_FIRST_CMA
cma_all.sh: line 9: mdsenv: command not found
CMA SECOND_CMA
cma_all.sh: line 9: mdsenv: command not found
CMA ANOTHER_SECOND_CMA
cma_all.sh: line 9: mdsenv: command not found
CMA THIRD_CMA
cma_all.sh: line 9: mdsenv: command not found
CMA ANOTHER_THIRD_CMA
cma_all.sh: line 9: mdsenv: command not found
CMA FOURTH_CMA
cma_all.sh: line 9: mdsenv: command not found
CMA ANOTHER_FOURTH_CMA
cma_all.sh: line 9: mdsenv: command not found
CMA FIFTH_CMA
cma_all.sh: line 9: mdsenv: command not found
CMA ANOTHER_FIFTH_CMA
The output of the command returns the CMAs as expected:
[Expert@MDS-P1:0]# $MDSVERUTIL AllCMAs
FIRST_CMA
ANOTHER_FIRST_CMA
SECOND_CMA
ANOTHER_SECOND_CMA
THIRD_CMA
ANOTHER_THIRD_CMA
FOURTH_CMA
ANOTHER_FOURTH_CMA
FIFTH_CMA
ANOTHER_FIFTH_CMA
There is something stopping the the command "mdsenv" from running. Environment variables??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i imported it on MDS /var/log folder as .sh file and running with sh <file name>? is this the right way to run this script
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
mgmt_cli show gateways-and-servers details-level "full"
Check Point - Management API reference
{
"from": 1,
"to": 2,
"total": 2,
"objects": [{
"uid": "302bcc2c-b3f1-405b-93dc-a5884288e499",
"name": "gw_192.0.2.14",
"type": "simple-gateway",
"ipv4-address": "192.0.2.14",
"operating-system": "Gaia",
"hardware": "Open server",
"version": "R80",
"sic-status": "communicating",
"interfaces": [{
"interface-name": "eth0",
"ipv4-address": "192.0.2.201",
"ipv4-network-mask": "255.255.255.0",
"ipv4-mask-length": 24,
"topology": {
"security-zone": {
"uid": "237a4cbc-7fb6-4d50-872a-4904468271c4",
"name": "ExternalZone",
"type": "security-zone",
"domain": {
"uid": "a0bbbc99-adef-4ef8-bb6d-defdefdefdef",
"name": "Check Point Data",
"domain-type": "data domain"
}
},
"leads-to-internet": true
},
"dynamic-ip": false
}
],
}another option would be:
mgmt_cli run-script script-name "show configuration" script "show configuration" targets.1 "corporate-gateway"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good points Tomer. The reason why I'm pulling info from gateways is that ultimately they have the "correct" information themselves about the model, SW version and take number. Else you really rely on the fact that info in the gateway object in mgmt is 100% accurate that can be misleading sometimes after upgrades when people forget to update it.. ![]() As they say - best to hear from horses mouth
As they say - best to hear from horses mouth ![]()
https://community.checkpoint.com/people/tomera5b2e7f3-09aa-32f8-96c2-f0f5bfa2988b Can you get take number of the gateway from mgmt server btw?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First of all this is good feedback for us. Consistency between gateway values defined at the Management server and the values on the gateways themselves is something we will try to emphasize better in our next releases.
You can can pull the take number by running “mgmt_cli run script” on the Management server for the script “clish -C ver” on the selected gateway targets.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 02 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - Keine Kompromisse - Sicheres SD-WANThu 02 May 2024 @ 05:00 PM (CEST)
SASE Masters: Deploying Harmony SASE for a 6,000-Strong Workforce in a Single WeekendAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center